Disclaimer: All views presented here, in this newsletter, are my own.
Author or the newsletter are not liable for any actions taken by any individual or any organization / business / entity. The information provided is for education and awareness purposes only and is not specific to any business and or situation.
Hey there,
Hope you are doing well. This is Part-5 of a multi-part series on ISA/IEC 62443 standards overview - and I will be expanding further on the following:
✍️ Links to my previous four parts of the ISA/IEC 62443 overview series.
📘 SP replacing CSMS IEC 62443-2-1:2024 - Security Program (SP)📜.
‼️ ISA-62443-2-1:2024 core 8 Security Program Elements (SPEs)📜.
↪️ Mapping of these SPEs with my The OT Security Dozen framework.
↪️ How CISO’s role have evolved in context of an OT Security Program.
📘 ISCI certification for Asset Owners, ACS Security Assurance (ACSSA)📜.
✍️ Few interesting reference resources.
Ready? let’s dig in.
Yours truly.
— Yousuf.
In case you missed, here’s are the previous 4 parts of the series:
introduction & background about the standards series,
key stakeholders, IACS roles & responsibilities,
4 groups of standards requirements,
3 phase IACS Cybersecurity Lifecycle,
ISA Secure Certifications for Suppliers, Products, Asset owners & individuals,
important terms, definitions & relationships,
Standards series introduction (of each standard part),
Standards elements, security levels, & types of standards requirements.
Foundational Requirements (FRs) and its relationships with System Requirements (SRs) and Component Requirements (CRs)
Zones, Sub-zones and conduits
Recently updated ISA/IEC 62443-2-1:2024 standard intro for Asset Owners. Security Program.
But before we begin, do me a favour and make sure you hit the “Subscribe” button to let me know that you care or liked and keep me motivated to publish more. Thanks!
Securing Things Related Offer:
Current iteration of my OT-CBPRS toolkit - Perfect for small to medium-sized regional or global manufacturers! This toolkit outlines OT cybersecurity best practices requirements specification. It sets a baseline and offers complementary support for your OT security policy needs. Use it to establish upfront requirements for any new OT security projects and watch your security soar!
Next iteration of my OT-CBPRS toolkit will include an OT Security Policy document as well for an additional amount and these requirements more closely aligned towards ISA/IEC 62443-2-1 requirements.
Get ready to supercharge your OT security! Dive into the OT-CBPRS toolkit and register your interest now to craft the ultimate policy and requirements specification. Don't miss out on this offer to uplift your OT Cybersecurity Program!
Read more about → OT/ICS Cybersecurity Requirements Specification for SMB Manufacturers [Securing Things by M. Yousuf Faisal].
IEC 62443-2-1:2024 - Security Program 📜
The ISA/IEC 62443-2-1:2024 standard, provides a foundation for asset owners to build their IACS (industrial automation control systems) (or simply OT) Security Program (note: mentioned in Part 4, OT CSMS is no longer used).
Standard provides asset owners with a framework to develop and evolve their SPs.
An effective OT SP defines and establishes a roadmap of capabilities for addressing all elements of security risk management and execution of secure business operations with on-going monitoring and measurement of the program.
Success of an OT SP rely on organisational buy-in from board room to factory floor.
A shared responsibility between asset owners, operators, integrators, contractors and or consultants. A more elaborate illustration between different parties is:
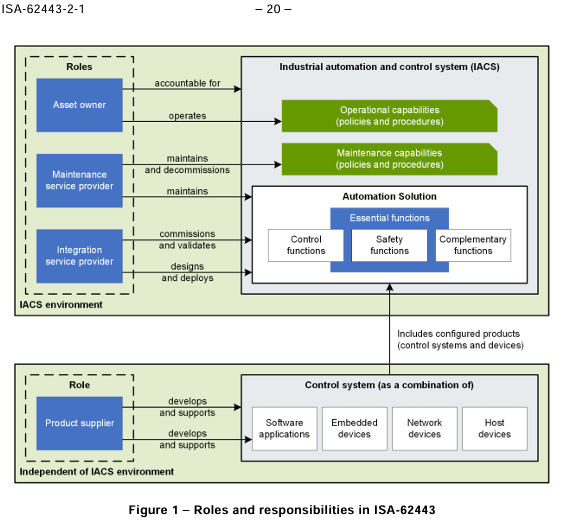
Source: ISA-62443 Preview from ISA.org
Integrating these SPEs as part of the SP into daily activities will allow asset owners to maintain a more resilient operations.
Security Program Elements (SPE)
Unlike the previous version ISA-62443-2-1:2009 which defines different “elements” as requirements for CSMS. Instead, in ISA-62443-2-1:2024 these elements are reworded as Security Program Elements or SPEs in short (hereafter).
The latest edition includes the following 8 SPEs:
SPE 1 – Organizational security measures (ORG) - includes following:
Alignment with an ISMS (enterprise cybersecurity) program,
Roles & Responsibilities, background checks,
Security awareness trainings, security responsibility trainings,
Supply Chain security elements.
Security assessments and reviews, and
Security of Physical access elements.
SPE 2 – Configuration management (CM) - includes following:
OT Asset inventory baseline (hardware / software and network communications),
Infrastructure documentation (network drawings etc.),
Configuration settings (/management), and
Change control (/management).
SPE 3 – Network & communications security (NET) - includes following:
Network Security (segmentation from non-IACS or OT zones, documentation of zones interconnections, segmentation from safety systems, network autonomy, network disconnection from external networks, internal network access control, accessible services, user messaging and network time distribution),
Secure wireless access (protocols, separation, properties, addresses)
Secure remote access (applications, connections and termination).
SPE 4 – Component security (COMP) - includes following:
Components and portable media (hardening, dedicated media),
Malware protection (software validation and installation),
Patch management (security patch authenticity/integrity, validation, installation, patch status, retention of security, and mitigation).
SPE 5 – Protection of data (DATA) - includes following:
Data Security Lifecycle (classification, confidentiality, Safety system configuration mode, retention policy etc.) and
Cryptographic mechanisms (key management, data Integrity).
SPE 6 – User access control (USER) - includes following:
Identification and authentication (identity assignment / removal / persistence, access rights assignment, least privilege, software service authentication / interactive login rights, human user authentication, MFA, mutual authentication, password protection, shared, compromised passwords, user login display information, failure displays, consecutive login failures, session integrity, concurrent sessions, screen lock, component authentication),
authorization and access control (authorization, separation of duties, multiple approvals, manual elevation of privileges).
SPE 7 – Event and incident management (EVENT) - includes following:
Event and incident management (Event detection, reporting, Event reporting interfaces
Logging, log entries, log access, event analysis, incident handling and response, vulnerability handling.
SPE 8 – System integrity and availability (AVAIL) - includes following:.
System availability and intended functionality (continuity management, Resource availability management, Failure-state),
Backup/restore/archive (non-interference, verification, media and restoration).
The point to illustrate here is that these are all very similar elements of an enterprise or IT security program, the key variable difference here is that, as cyber practitioners, we need to see their applicability in the context of the cyber-physical industrial processes and the related risks, impacts and consequences which are different from IT, e.g., OT patch management practices are considerably different from IT patch management and so on with other program elements.
Mapping with my OT Security Dozen framework
Published in the 1st quarter of 2022, my OT Security Dozen framework, was an effort to simplify the program elements based on limited experience.
Whether its, the ISA-62443-2-1 standard SPEs and or SANS Top 5 ICS considerations, STL OT security Dozen framework could be mapped with easily. A simple illustration below.

OT Security Dozen Framework Mapped to ISA-62443-2-1
Concluding part 5 here.
Stay tuned to find out more in Part 6 - ISA/IEC 62443 Standards Series Overview in a future newsletter edition, in which we’ll cover, cybersecurity risk assessments using 62443-3-2 and 3-3, applicability of different parts of the standard across the cybersecurity lifecycle phases, and more.
References
ISA main website → https://www.isa.org/
Announcement on the 62443-2-1 updated → https://www.isa.org/news-press-releases/2025/january/update-to-isa-iec-62443-standards-addresses-organi
ISA Global Cybersecurity Alliance (ISAGCA) → https://gca.isa.org/resources.
Related Offer:
Current iteration of my OT-CBPRS toolkit - Perfect for small to medium-sized regional or global manufacturers! This toolkit outlines OT cybersecurity best practices requirements specification. It sets a baseline and offers complementary support for your OT security policy needs. Use it to establish upfront requirements for any new OT security projects and watch your security soar!
Next iteration of my OT-CBPRS toolkit will include an OT Security Policy document as well for an additional amount and these requirements more closely aligned towards ISA/IEC 62443-2-1 requirements.
Get ready to supercharge your OT security! Dive into the OT-CBPRS toolkit and register your interest now to craft the ultimate policy and requirements specification. Don't miss out on this offer to uplift your OT Cybersecurity Program!
Read more about → OT/ICS Cybersecurity Requirements Specification for SMB Manufacturers [Securing Things by M. Yousuf Faisal].
How CISO’s role have evolved for OT Security Program
In the past, most CISO’s within critical infrastructure and or especially in manufacturing were limited in their roles and responsibilities across the enterprise side of things, while CIO and other teams were involved in supporting industrial IT.
In the last few years, things dramatically shifted for CISOs, and their role evolved into taking cybersecurity responsibilities for the OT side as well and they had to figure their way into the unknown territories of OT environments.
CISOs, are now tasked to mobilise security program activities involving plant side operations.
ACS Security Assurance (ACSSA) Certification to ISA/IEC 62443-2-1, 2-4, 3-2, 3-3
Last year, ISA, along with the ISA Security Compliance Institute (ISCI), has announced its intention to create an all-new conformity assessment scheme for automation systems deployed at operating sites — i.e. asset owners / operators or OT site assessment security assurance program - ACSSA Certifications.
OT cybersecurity IACS assessment scheme would certify individual automation and control systems that are in the operation and maintenance phase of their security lifecycle at end user sites.
Scope includes all types of automation and control systems in all industries.
1st in line will be starting with traditional process industries and adjacent industries in critical infrastructure like oil and gas, chemicals, and water/wastewater.
2nd in line will be market segments like railways, ports, electric sector, EV infrastructure, DER, and pipelines.
The scheme will include an on-site control system assessment program and site certification program.
Note: Securing Things is a General member of the ISCI.
Few interesting reads
Here are some interesting reads of the week:
Read: OT/ICS Cybersecurity - Volume 2 by automation website.
Read: Cyber-Physical Energy Systems Security: Threat Modeling, Risk Assessment, Resources, Metrics, and Case Studies - paper by Ioannis Zografopoulos, Juan Ospina, XiaoRui Liu & Charalambos Konstantinou.
Read: Security Best Practices and Risk Assessment of SCADA and Industrial Control Systems - by Guillermo A. Francia, III, David Thornton, and Joshua Dawson.
Read: Cyber Security Risk Assessment on Industry 4.0 using ICS testbed with AI and Cloud - by Wataru Matsuda; Mariko Fujimoto; Tomomi Aoyama; Takuho Mitsunaga.
OpenBAS: Open-source Breach & Attack Simulation! - An open-source platform provides a comprehensive environment for planning, scheduling, and conducting cyber adversary simulation campaigns.
My Recent Most Viewed Social Posts:
In case you’ve missed - here are some of my recent most viewed social posts.
The Digital Factory (Data Flow) - Part 2 Industry 4.0 data/event driven data flows and security considerations and how's CISO's role is evolved in OT security.
Cybersecurity & Data Privacy for Hong Kong - HK Cybersecurity Market, upcoming Critical Infrastructure Bill 2024 regulations, Data Privacy Program Core elements, HK markets and more.
Cybersecurity and AI Across the Industrial Automation Stack - Monthly Digest # 0. - Idea and poll around the subject.
Tip to remember ISA/IEC 62443 Standards Group & Overview Part 2.
📢 📰 Secure by 3Ds (Demand | Design | Default) 📢 📰 ✅ The trifecta reshaping IT & OT cybersecurity industry!
The Digital Factory (Hub & Spoke) - UNS concept, Digital factory, 4.0, data/event driven architecture, industry conferences, and more.
OT Security Visibility Solutions & Metrics -✅Lessons learned consulting on top OT Security Solutions, KPIs/ODMs, & more🚀.
IT & OT/ICS Cybersecurity Policy(/ies) - Deciding on the Policy Route for your industrial environments.
Securing Things Academy:
IT & OT CySEAT (Cyber Security Education And Transformation) course is designed for IT and OT cybersecurity practitioners. Join the wait-list → here.
Checkout a brief overview below:
Ways in which I can help?
Whenever you are ready - I can help you with:
A - IT & OT Cybersecurity Advisory / Consulting services - for securing your business and or its digital transformation journey.
B - Security Awareness Training & Phishing Awareness Portal - Train your staff and build a Security awareness program subscription based service.
C - Securing Things Academy (STA) - Security trainings for IT & OT practitioners.
Visit the newsletter website for Links to above services and or reach out at info[at]securingthings[dot]com or DM me via LinkedIn.
D - Securing Things Newsletter - Sponsor this newsletter to showcase your brand globally, or subscribe to simply Get Smarter at Securing Things.
Reach out at newsletter[at]securingthings[dot]com or DM me via LinkedIn.
✉️ Wrapping Up - How are we doing?
I invite you as part of #SecuringThings community to share your feedback.
Rate the newsletter content
Your feedback and input is invaluable to me as we work together to strengthen our cybersecurity defenses and create a safer and smarter digital society.
Let us know how we can improve this and or what you’d like to see in future?
Thank you for your trust and continued support.
Do register, validate your email, and request login link to submit poll to be able to enter a chance to win a future course giveaway.
Thanks for reading - until the next edition!
It’s a Great Day to Start Securing Things for a Smart & Safer Society.
Take care and Best Regards,
M. Yousuf Faisal. (Advice | Consult Cyber & business leaders in their journey on Securing Things (IT, OT/ICS, IIOT, digital transformation, Industry 4.0, & AI) & share everything I learn on this Newsletter | and upcoming Academy).