Disclaimer: All views presented here, in this newsletter, are my own.
Author or the newsletter are not liable for any actions taken by any individual or any organization / business / entity. The information provided is for education and awareness purposes only and is not specific to any business and or situation.
Table of Contents
Hello Securing Things Community,
This is Part-2 of a multi-part series on ISA/IEC 62443 standards overview - and will be expanding upon the 4 main groups and the series of documents, their purpose, security levels, expand IACS cybersecurity lifecycle phases, individual and product certifications.
In ISA/IEC 62443 Standards Overview Series - Part 1, we covered, introduction & background about the standards series, basics around:
key stakeholders, IACS roles & responsibilities,
4 groups of standards requirements,
3 phase IACS Cybersecurity Lifecycle, and
introduce you to certification options from Supplier and Product, Asset owner Certifications from #ISASecure (Securing Things is a supporting member of ISASecure), and
cybersecurity certifications for individuals by #ISA.
{Quick test - Part 1 included a tip to remember the 4 groups in the standards series with the help of a short phrase; see if you can recall, without giving a peep at Part 1. Did you? if not go ahead and click the Part 1 link above and checkout the code snippet like this for the tip...}. :-) hope that'll help you remember. But before we begin, do me a favour and make sure you hit the “Subscribe” button to let me know that you care or liked and keep me motivated to publish more. Thanks!
Securing Things Academy:
IT & OT CySEAT (Cyber Security Education And Transformation) course is designed for IT and OT cybersecurity practitioners. Join the wait-list → here.
Checkout a brief overview below:
But first, let’s cover some basic definitions, which builds the foundation of understanding in later part of the series.
Important Terms, definitions and relationships
Definition & relationships between different OT terms per #62443:

Key terms to know
➡ Components✅ = Devices & Software Apps. Includes IIOT components.
➡ Control Systems✅= Software & hardware components. Includes IIOT Systems.
➡ Automation Solution✅= Specific implementation of Control Systems
➡ Industrial Automation Control Systems (IACS)✅= Combo of Automation Solution + People + Security Program. Includes IIOT IACS.
➡ Cloud✅= collection of networked remote servers.
➡ System Under Consideration (SuC)✅= project scope definition.
➡ Zones & Conduits✅= Zones are groups of assets/functions & Conduits are logical groups of communication channels, sharing common security requirements.
➡ All these generates data and data flows ✅ based on information model e.g. ISA95.
➡ All covered in standards ✅e.g. ISA/IEC 62443, ISA95, etc. and other related standards.
ISA/IEC 62443 Standards Series📜
Here’s a current list of published standards below as covered previously.

ISA/IEC 62443 series of standards and flow of requirements on target security levels
There are few standards that are been worked on as of now for revisions. The most recent update is for Part 2-1 with significant changes to the standards document.
A simplified overview from ISASecure / ISAGCA presentation is below:
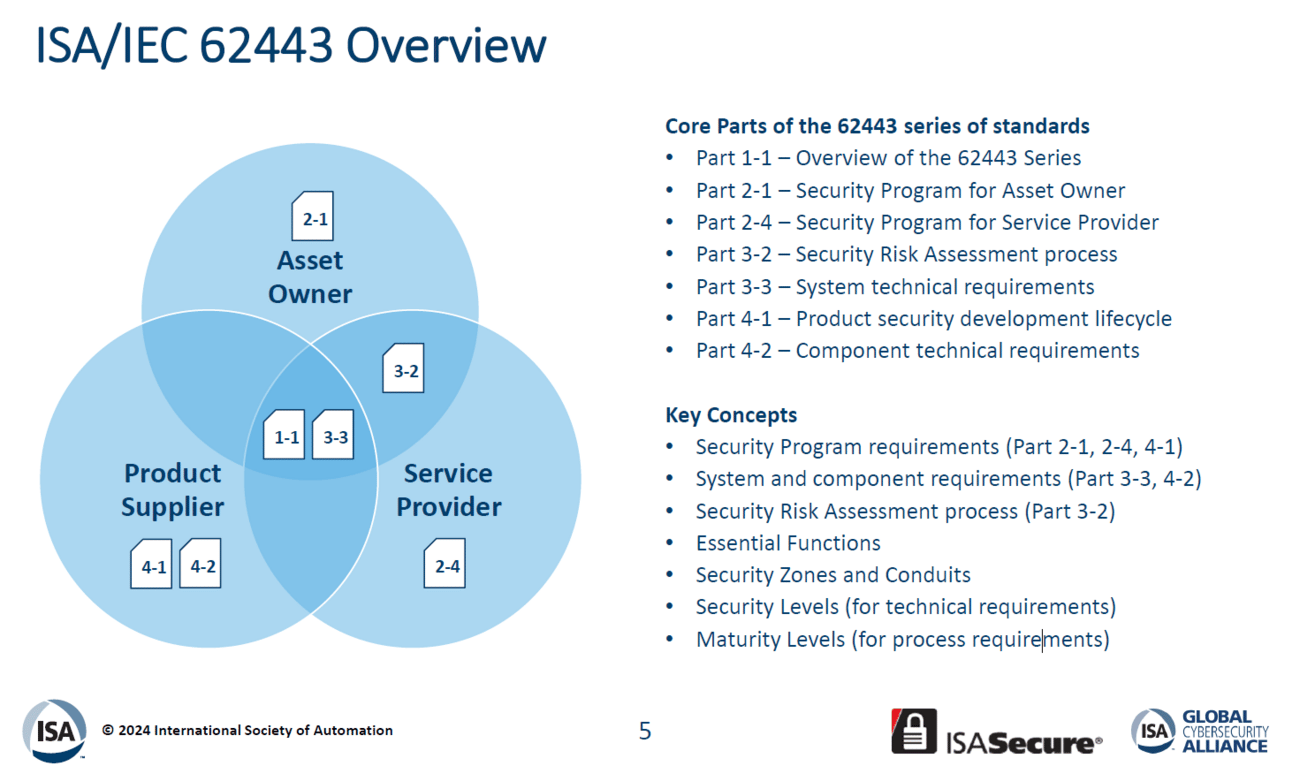
Overview
ISA/IEC 62443 is a functional standard that sets security performance objectives without specifying how to achieve them.
General:
As the group name implied, this group includes standard supporting documents addressing topics that are common to the entire series.
Standards Part | Part Description |
|---|---|
Part 1-1 Terminology, concepts and models <starting point> | Offers an overview of the standards series, introducing terminology, concepts, and models. It is intended for those seeking to understand the fundamental concepts of the series. |
Part 1-2 Master glossary of terms and definitions. | A list of terms and abbreviations used throughout the series. |
Part 1-3 System security conformance metrics | Describes a methodology to develop quantitative metrics from standards' process and technical requirements. |
Part 1-4 IACS security lifecycle and use cases | Offers a detailed overview of the IACS security lifecycle and use cases demonstrating various applications. |
Policies & Procedures:
Standards documents in this group focus on the policies and procedures associated with IACS security.
Standards Part | Part Description |
|---|---|
Part 2-1 Establishing an IACS security program | Outlines requirements for defining and implementing an effective IACS Security Program for asset owners responsible for its design and execution. |
Part 2-2 Security Program Ratings | Offers a method to assess an IACS's protection level against ISA/IEC 62443 standards. |
Part 2-3 Patch management in the IACS environment | Guidance on IACS patch management for those responsible for designing and implementing such programs. |
Part 2-4 Security Program requirements for IACS service providers | Specify requirements for IACS service providers, including system integrators and maintenance providers. |
Part 2-5 Implementation guidance for IACS asset owners | Guides asset owners on operating an effective IACS Security Program. |
Systems:
Standards documents in this group address requirements at the system level.
Standards Part | Part Description |
|---|---|
Part 3-1 Security technologies for IACS | Explains the use of security technologies in an IACS environment for those interested in their applicability to control systems. |
Part 3-2 Security risk assessment for system design | Focuses on cybersecurity risk assessment and system design for IACS, creating a Zone and Conduit model, Risk Assessments, and Target Security Levels, documented in the Cybersecurity Requirements Specification, primarily for asset owners and system integrators. |
Part 3-3 System security requirements and security levels | Outlines IACS system requirements by security level for control system suppliers, integrators, and asset owners. |
Components:
Standards documents that provide information about the more specific and detailed requirements associated with the development of IACS products.
Standards Part | Part Description |
|---|---|
Part 4-1 Secure Product development lifecycle requirements | Outlines secure development lifecycle requirements for OEMs/product suppliers or developers, targeting Control System and Component product suppliers. And is required for Secure Development Life-Cycle Assurance (SDLA) Certification from ISCI. |
Part 4-2 Technical security requirement for IACS components | Outlines security level requirements for IACS Components, including Embedded Devices, Host Devices, Network Devices, and Software Applications, aimed at suppliers of control system components. |
IEC 62443-4-1, along with IEC 62443-4-2 and IEC 62443-3-3, helps organizations develop a 'Secure Development Lifecycle' to ensure security throughout the lifecycle of devices and applications.
Securing Things Academy:
IT & OT CySEAT (Cyber Security Education And Transformation) course is designed for IT and OT cybersecurity practitioners. Join the wait-list → here.
Checkout a brief overview below:
Standards Referencing ISA/IEC 62443
The series is referenced throughout the NIST Cybersecurity Framework (CSF), and CISA Cybersecurity Performance Goals (CPGs.).
The CPGs frequently reference ISA/IEC 62443-2-1 and ISA/IEC 62443-3-3 across categories like account security, device security, data security, governance and training, vulnerability management, supply chain/third party, and response and recovery.
Adoption of ISA/IEC 62443 standard is optional and dependent upon a risk assessment of IACS under consideration. Compliance and conformance is voluntary and consensus driven.
Standards Elements
ISA/IEC 62443 standards series contains the following two elements:
Normative Elements - those parts that shall be complied with to demonstrate compliance with the standard. Indicated by use of words “shall” or “must”.
Informative Elements - provide clarification or additional information. May not contain requirements. Words “shall” or “must” are not used.
Security Level (SL)
A Security Level (SL) is defined as a measure of confidence that the system, zone, or conduit functions in the intended manner and provide a level of assurance for risk reduction and minimises the chance of exposure due to vulnerabilities.
How and when an organization uses SLs depends on where they are in their life cycle.
There are three types of SLs used throughout the ISA/IEC 62443 Series:
Target Security Levels (SL-T) are the desired security levels for an Automation Solution, indicating the protection needed for the system, zone, or conduit. An Asset Owner uses the risk assessment process (Part 3-2) to determine and document the appropriate SL-T in their Cybersecurity Requirements Specification.
Capability Security Levels (SL-C) are the native technical security countermeasures within a system (Part 3-3) or component (Part 4-2) that can be configured to protect the Automation Solution without additional compensating countermeasures.
Achieved Security Levels (SL-A) are the actual measured SLs for an Automation Solution, determined post-operation.
The SL-C requirements for systems (Part 3-3) and components (Part 4-2) are grouped into different levels using an increasing level of potential risk reduction, as shown below.
SL-Cs are qualitative (in contrast to quantitative risk reduction in safety engineering) and takes an attacker perspective on the motives and how many resources, means, and skills they would need to overcome the security countermeasures required at that SL.

Security Levels per ISA/IEC 62443 standard
Standards Requirements
Within the standard there’s are several types of requirements with a hierarchy including:
Foundational Requirements (FR)
System Requirements (SR)
Component Requirements (CR)
Host Device Requirements (HDR)
Network Device Requirements (NDR).
For each type of requirement above, there’s a defined security level. Security level of FR is derived from its SR and CR.
This is it for now on Part 2.
Stay tuned to find out more in Part 3- ISA/IEC 62443 Standards Series Overview in a future newsletter edition, in which we’ll cover, more on the standards, what are the foundational requirements, its relationship with other requirements, applicability of different parts of the standard across the cybersecurity lifecycle phases, zones and conduits, reference architecture and more.
References
ISA main website → https://www.isa.org/
ISA Global Cybersecurity Alliance (ISAGCA) → https://gca.isa.org/resources. e.g.:
Quick Start Guide to ISA/IEC 62443
IoT Security Maturity Model: 62443 Mappings for Asset Owners and Product Suppliers
and more…
In case you’ve missed - here are some of my recent most viewed social posts.
Role of AI & Cybersecurity in Manufacturing - Use Cases, Predictions, Threats, Mitigations.
This is it - Good Bye. Happy New Year! Recap on 2024 and the Future of Securing Things in 2025.
Cybersecurity (IT, OT/ICS, AI, Open source) Insights from Q4 2024
What the heck is ITDR - A crash course on Identity Threat Detection & Response.
IT & OT/ICS Cybersecurity Policy(/ies) - Deciding on the Policy Route for your industrial environments.
Digital Manufacturing at Risk - Start with Cybersecurity and Digital Transformation Maturity Assessment Reviews Now!
Ways in which I can help?
Whenever you are ready - I can help you / your organization / your customers with:
A - IT & OT Cybersecurity Advisory / Consulting services - for securing your organisation’s or client’s digital transformation journey.
B - Security Awareness Training & Phishing Awareness Portal - Train your staff and build a Security awareness program.
C - Securing Things Academy (STA) - Security trainings for IT & OT practitioners.
D - Securing Things Newsletter - Get your brand (personal / business) in front of global audience by sponsoring this newsletter. And or simply subscribe to Get smarter at Securing Things.
Reach out at info[at]securingthings[dot]com or DM me via LinkedIn.
Feedback
I invite #SecuringThings community to share their feedback.
Your feedback and input is invaluable to me as we work together to strengthen our cybersecurity defenses and create a safer and smarter digital society. Thank you for your trust and continued support.
Do register, validate your email, and request login link to submit poll to be able to enter a chance to win a future course giveaway. Also:
Rate the newsletter content
Thanks for reading - until the next edition!
It’s a Great Day to Start Securing Things for a Smart & Safer Society.
Take care and Best Regards,
M. Yousuf Faisal. (Advice | Consult Cyber & business leaders in their journey on Securing Things (IT, OT/ICS, IIOT, digital transformation, Industry 4.0, & AI) & share everything I learn on this Newsletter | and upcoming Academy).


