Disclaimer: All views presented here, in this newsletter, are my own.
Author or the newsletter are not liable for any actions taken by any individual or any organization / business / entity. The information provided is for education and awareness and is not specific to any business or situation.
Table of Contents
This is part-1 of a multi-part series on ISA/IEC 62443 standards series - an introductory overview. This and later parts of the series, will cover, but not limited to, key roles/stakeholders, key concepts and approaches of ISA/IEC 62443, brief overview on the documents within the series of standards, industrial automation control systems (IACS) Cybersecurity Lifecycle, individual and product certifications. So be sure to subscribe to Securing:Things Newsletter, Securing Things Limited page, follow hashtag #SecuringThings and or on twitter @SecuringThings.
Introduction & Background:
International Society of Automations' ISA99 Committee and the International Electrotechnical Commission (IEC) Technical Committee 65/Working Group 10 have developed and published the ISA/IEC 62443 series of standards and technical reports.
The 📜 ISA/IEC 62443 series of standards and technical reports📜:
define requirements and processes for implementing and maintaining secure industrial automation and control systems (IACS). ✅
set best practices and a way to assess level of security performance. ✅
endorsed by the United Nations and integrated into the draft of the UN’s Economic and Social Council’s proposal for a common regulatory framework on cyber security in Europe. The IEC also officially designated the IEC/ISA 62443 series of standards as “horizontal,” i.e., the standard series are proven to be applicable to a wide range of different industries.✅
set cybersecurity benchmarks in all industry sectors that use IACS, including electric power generation and distribution, medical devices, transportation, building automation, discrete manufacturing, and process industries such as chemicals, oil and gas.✅
covers everything from establishing an OT cybersecurity management systems (CSMS) (aligned with ISO 27001 ISMS), provides details on risk assessments and management, vulnerability management, supply chain security issues and components or systems certification and more. ✅
provides a comprehensive approach to applying cybersecurity to industrial systems, and promotes collaboration by bringing operations, process safety, IT/ICT and cybersecurity teams working together towards a common goal.
An internationally accepted standard for any organization with industrial assets, needing protection from cyber threats. The ISA/IEC 62443 standards are referenced in many other international standards, frameworks, guidelines such as the NIST Cybersecurity Framework. Most recently, referenced in the CISA Cybersecurity Performance Goals (CPGs.) The CPGs extensively reference ISA/IEC 62443-2-1 and ISA/IEC 62443-3-3 in almost every category, including data security, device and account security, governance and supply chain/third party, training, vulnerability management, and incident response and recovery.
ISA founded the ISA Global Cybersecurity Alliance (ISAGCA) in 2019 to advocate for the importance of automation cybersecurity and to further the adoption of the ISA/IEC 62443 series of standards, worldwide.
Definitions & IACS Roles & Responsibilities

✅For extended taxonomy reference please refer to➡️IACS Taxonomy Glossary.
Key roles and their inter-relationships include the following:
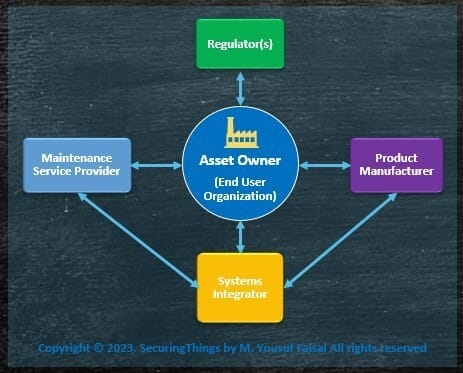
STL - OT - Stakeholders & their Interactions
Each role performs certain tasks and are responsible for a different set of activities, as outlined in the figure below (which is self explanatory):

Source: IACS Roles & Responsibilities by ISASecure and ISAGCA
✅For more details checkout➡️IACS Principal Roles and Responsibilities
ISA/IEC 62443 Standards Series📜
There are a series of documents (1000+ pages) that constitute different parts of standards document and or technical requirements highlighted in figure below:
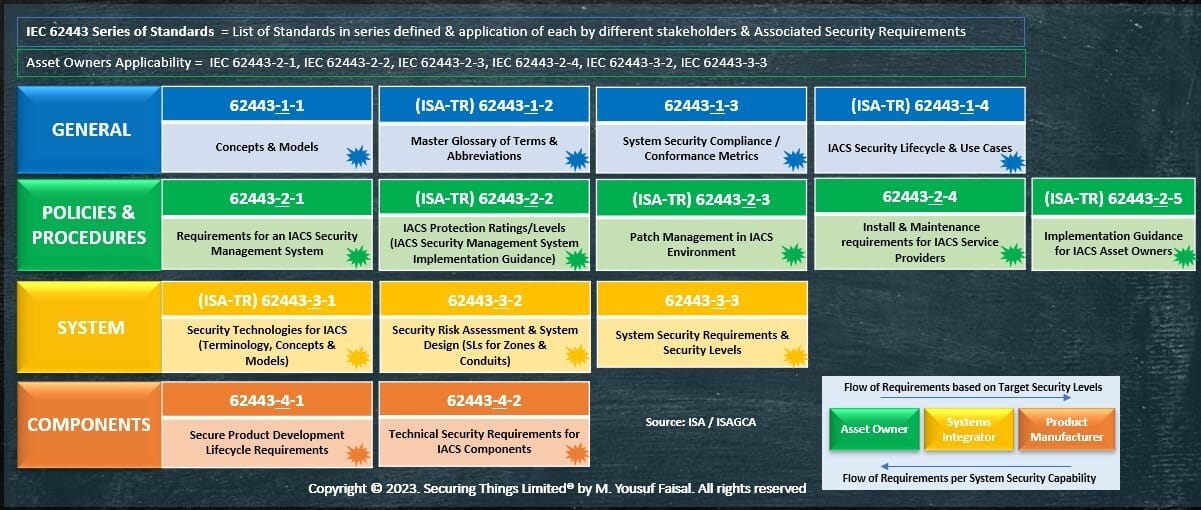
ISA/IEC 62443 Series of Standards
Tip to remember - By M. Yousuf Faisal:
To memorize above diagram, remember the term - "GPS Connected", where
- G stands for General at 1 - hence 62443-1-X,
- P = Policies & Procedures at 2 - hence 62443-2-X,
- S = Systems at 3 - hence 62443-3-X, and
- C = Component at 4 - hence 62443-4-X.
So in conversations, if someone mentions 62443-2-2 or other part, you can quickly relate to which group or part of standard is being referred to in the series of standards. General – Group 1: addressing topics that are common to the entire series.
Policies & Procedures – Group 2: covers policies/procedures associated with IACS security.
System Requirements – Group 3: includes requirements at the system level.
Component Requirements – Group 4: includes more specific and detailed requirements associated with development of IACS products.
Note: The standards are regularly updated, modified, and expanded. There are certain standards that are currently being updated (to be published in future) and certain documents that are not yet classified or accepted as standards and hence are referred as Technical requirements. Individuals and organizations are welcome to join the ISA community to serve on its various subcommittees.
Organizations can adapt a ISA/IEC 62443 standards, a risk-based approach, outlining a methodical process to ensure consistency in requirements across all stakeholder roles and responsibilities, incorporating security measures throughout a typical IACS project lifecycle. Ultimately, the goal is to improve the reliability, integrity, and security of IACS environments against a successful cyberattack.
Cybersecurity Lifecycle
The security lifecycle in the ISA 62443 standard includes three phases: Assess, Develop and Implement, and Maintain. The security life cycle is a continuous process for minimizing risks to the IACS environment.
✅ Assess phase ➡️ topics include high-level cyber risk assessment, allocation of IACS assets to security zones or conduits, and detailed cyber risk assessment. ISA standard 62443-3-2 provides guidelines for the assess phase.
✅ Develop and Implementation phase ➡️ topics include cybersecurity requirements specification, the design and engineering of security countermeasures, and the installation, commissioning, and validation of cyber security countermeasures. ISA standard 62443-3-2 and 62443-3-3 provides guidelines for this phase. The design and development of other means of risk reduction may also be included.
✅ Maintain phase ➡️ topics includes cyber security countermeasures maintenance, monitoring, and change management, as well as incident response and recovery. ISA standard 62443-2-1 addresses cybersecurity maintenance and provides guidelines for processes which should be continuously monitored. Also includes a cybersecurity management system for policies, procedures, training and awareness. Periodic cybersecurity audits should also be conducted as a continuous process.
✅ For more details checkout ➡️ Guide to Security Lifecycles in ISA/IEC 62443
✳Certifications✳
ISASecure is a member-driven organization comprised of end users, suppliers, tool providers, cloud providers, and integrators. Founded in 2007,
Securing Things is a supporting member of ISASecure. Checkout below:
ISA Security Compliance Institute (ISCI) manages the ISASecure cybersecurity certification program which certifies to ISA/IEC 62443 standards.
Supplier and Product Certifications
🎯For suppliers and product manufacturers ISASecure provides the following certifications:
👉Product certification for IACS components called ➡️ Component Security Assurance (CSA)
👉Product certification for IIoT Components called ➡️ IIoT Component Security Assurance (ICSA)
👉Process certification for IACS systems called ➡️ System Security Assurance (SSA)
👉 Process certification for IACS development organizations called ➡️ Security Development Lifecycle Assurance (SDLA)
✅For more details checkout ➡️ Overview of ISASecure Certification for ISA/IEC 62443.
Asset Owners Certification
🎯More recently - The International Society of Automation (ISA), along with the ISA Security Compliance Institute (ISCI), has announced in Feb 2023 its intention to create an all-new conformity assessment scheme for automation systems deployed at operating sites.
👉Certification for facilities operating an IACS called ➡️ IACS Security Assurance (IACSSA) - anticipate rollout in early 2025 with full training program and qualification process for conformity assessment bodies.
✅For more details checkout ➡️ IACS Security Assurance (IACSSA) – ISASecure Site Assessment Program.
Professional/Individual's Certifications
🎯ISA provides training and certification for individuals on ISA/IEC 62443 standards in 4 part training and certificate exam series Covering the Complete Cybersecurity Lifecycle for Industrial Automation and Control Systems, leading to an Expert certification.
✅For more details checkout ➡️ ISA Cybersecurity Certificate Training Program.

Source: ISA and ISAGCA
You have the option to choose between a Classroom, Virtual Classroom and or Self-Paced Modular training options.
References
More on ISA/IEC 62443 cybersecurity series in future newsletter editions.
So be sure to subscribe to Securing:Things Newsletter, Securing Things Limited page and follow #SecuringThings on LinkedIn and @SecuringThings on X/twitter.
Feel free to reach out or get in touch at info[@]securingthings[.]com for any business needs, project support, discussions and or simply information sharing.
Follow @securingthings.
Securing Things Academy:
IT & OT CySEAT (Cyber Security Education And Transformation) course is designed for IT and OT cybersecurity practitioners. Join the wait-list → here.
Checkout a brief overview below:
Ways in which I can help?
Whenever you are ready - I can help you with:
A - IT & OT Cybersecurity Advisory / Consulting services - for securing your business and or its digital transformation journey.
B - Security Awareness Training & Phishing Awareness Portal - Train your staff and build a Security awareness program subscription based service.
C - Securing Things Academy (STA) - Security trainings for IT & OT practitioners.
Visit the newsletter website for Links to above services and or reach out at info[at]securingthings[dot]com or DM me via LinkedIn.
D - Securing Things Newsletter - Sponsor this newsletter to showcase your brand globally, or subscribe to simply Get Smarter at Securing Things.
Reach out at newsletter[at]securingthings[dot]com or DM me via LinkedIn.
How are we doing?
I invite you as part of #SecuringThings community to share your feedback.
Rate the newsletter content
Your feedback and input is invaluable to me as we work together to strengthen our cybersecurity defenses and create a safer and smarter digital society.
Let us know how we can improve this and or what you’d like to see in future?
Thank you for your trust and continued support.
Do register, validate your email, and request login link to submit poll to be able to enter a chance to win a future course giveaway.
Thanks for reading - until the next edition!
It’s a Great Day to Start Securing Things for a Smart & Safer Society.
Take care and Best Regards,
M. Yousuf Faisal. (Advice | Consult Cyber & business leaders in their journey on Securing Things (IT, OT/ICS, IIOT, digital transformation, Industry 4.0, & AI) & share everything I learn on this Newsletter | and upcoming Academy).
The Newsletter Platform Built for Growth
When starting a newsletter, there are plenty of choices. But there’s only one publishing tool built to help you grow your publications as quickly and sustainably as possible.
beehiiv was founded by some of the earliest employees of the Morning Brew, and they know what it takes to grow a newsletter from zero to millions.
The all-in-one publishing suite comes with built-in growth tools, customization, and best-in-class analytics that actually move the needle - all in an easy-to-use interface.
Not to mention—responsive audience polls, a custom referral program, SEO-optimized webpages, and so much more.
If you’ve considered starting a newsletter, there’s no better place to get started and no better time than now.

![ISA/IEC 62443 Standards Series - Overview (Part 1) [Securing Things by M. Yousuf Faisal]](https://media.beehiiv.com/cdn-cgi/image/fit=scale-down,quality=80,format=auto,onerror=redirect/uploads/asset/file/f7bd5c90-599e-4bf0-ab86-2f8b0763a2dc/ST-Newsletter-ISA-IEC-62443-Standards-Overview-Part1-by-MYousufFaisal.jpg)

