Disclaimer: All views presented here, in this newsletter, are my own.
Author or the newsletter are not liable for any actions taken by any individual or any organization / business / entity. The information provided is for education and awareness and is not specific to any business or situation.
Table of Contents
👉In this edition, we'll be covering, at a high-level, the key stakeholders & their interactions within industrial ecosystem, introduce a typical IACS / OT / ICS project lifecycle and relevant cybersecurity activities and cover basics on OT Cybersecurity requirements specification (per ISA/IEC 62443 standards).
Assuming, we have the results from OT site(/s) assessments, business inventory discovered, cybersecurity strategy and roadmap in place, presented and approved by executive leadership, and an OT cybersecurity policy defined; (Note: all these covered in previous newsletter editions); so what's next?
📚Now we have to define a minimum set of OT cybersecurity best practices requirements documented - standards checklist (with supported guidance)🎯- (it should support the documented digital transformation strategy, minimum technical requirements, industry 4.0/IIOT reference architecture, IT/OT cybersecurity policy, regulatory requirements-if any, and aligned with the threat landscape for your organization sector - see below).
Threat Landscape📔
Several industry reports📔since 2020 till 2023, clearly highlights that there's a steady increase in the number of ransomware attacks / incidents impacting many asset owners in the manufacturing industry or critical infrastructure sector. ☣⚡
Key Stakeholders - Roles & their interactions
Below figure depicts a simplified high-level view of end user organization (or asset owners), other stakeholders and their interactions for a typical manufacturing environment or organization in critical infrastructure sectors. (Note: may not represents all possible relationships / interactions).

STL - OT - Stakeholders & their Interactions
➡️Note: product manufacturers can also be maintenance service providers and may have systems integration capabilities as well as preferred partners that they work with.✅
Is this limited to manufacturers only? certainly not - even other critical infrastructure environments like financial sector, data centres and businesses with smart buildings, smart distribution centres, etc. and other business operations involves similar stakeholders interaction scenarios.
Acronym Soup
Let's define the key stakeholders, their responsibilities and some specific terms:
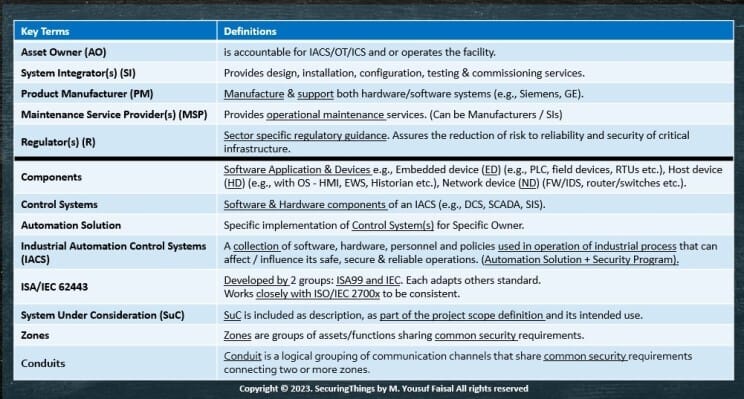
Key Terms & Definitions
IACS / OT / ICS Project Lifecycle & Cybersecurity Activities🎯
A typical IACS / OT / ICS Project lifecycle have following stages, highlighted in the figure below. At each stage of the project lifecycle, from procurement to decommissioning, certain cybersecurity activities can be embedded into the lifecycle to ensure security is not an afterthought.🎯
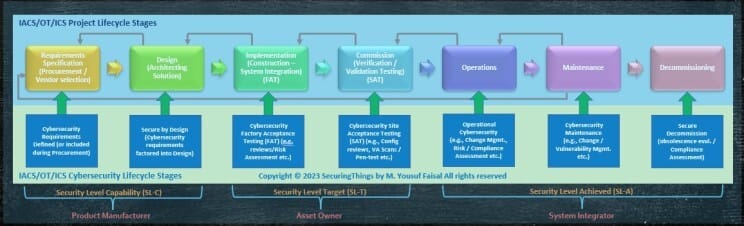
Typical IACS/OT/ICS Project Lifecycle Stages & Cybersecurity Activities at each stage of Lifecycle
More on cybersecurity activities throughout the OT project lifecycle in future newsletter edition.
➡️For greenfield projects / new implementations - ensure cybersecurity requirements are defined and factored into each stage of the project lifecycle.
➡️For brownfield projects / existing implementations - start with accessing risks, identifying gaps, vulnerabilities and explore remediation paths, upgrades and other maintenance activities to add some of these cybersecurity elements.
Tip: If you as an organization is just thinking of starting out on such a journey to embed cybersecurity activities into your IACS / OT / ICS Project lifecycle - but lacks skills/resources and or business buy-in; it's recommended to take an iterative incremental approach, whereby, you establish an initial set of practices to be incorporated as quick wins - iterate, mature, and add more cybersecurity activities. Don't boil the ocean at the beginning.
👉We'll be focusing on first stage of project lifecycle i.e. for establishing a list of cybersecurity requirements specifications.✅
ISA/IEC 62443 Standards - Cybersecurity Requirements Specification (CRS)📋
✅According to ISA/IEC 62443 standards, Cybersecurity Requirements Specification (CRS)📋- documents - general security requirements based upon organization policy and standards, relevant regulations and the outcome of the high-level risk assessment as well as any mandatory security functions of the Systems Under Consideration (SuC).

OT Cybersecurity Requirements Specification (CRS) per ISA/IEC 62443 Standards
Looking at the above list of items, there's lots to cover in a CRS document, for any given SuC. (More on the overview of ISA/IEC 62443 standards, security target levels etc. in future newsletter edition).
Safety, Reliability, Availability, Integrity, and Confidentiality related cybersecurity requirements may be logically grouped together, as well as monitoring and reporting requirements. Grouping requirements can provide better organization of the information. For example, Access Control requirements may include:
Identification and authentication of users
User roles and privileges
User administration
Password management and more.
➡️Note: Cybersecurity acceptance testing (e.g. CFAT or CSAT) (pre-commissioning) performs verification of the cybersecurity requirements specifications defined in CRS.✅
✳ The Challenge ✳
Many asset owners, in particular, SMB manufacturers don't have the required resources or skills sets and may find it difficult to build such a document or practice. Also they need to review a plethora of reference standards and guidance documents (many of them are old/outdated) and may find it complex or difficult to follow a full list of standard specific requirements - typical list is 100+ requirements for any given standards or guidance document.
✳ The Solution ✳📜
Asset owners, can establish a predefined reference set of minimum best practices requirements specifications, for standardisation across all production sites or facilities, for any new or existing SuC (systems under consideration) or all projects. Later for each specific projects just add delta to requirements specification e.g., assumptions, specific security controls needs, selecting security target levels etc.
Each requirement, should be supported by specific guidance, reference standards, control elements for greater staff awareness and minimize ambiguity.
CRS, need to include variety of domains/topics to be covered as part of IACS project lifecycle from PPT perspective:
People - educate the relevant internal stakeholders / team members (staff/contractors) that will be directly involved or are responsible for following and executing on OT-CBPRS. Example stakeholders are IT/OT cybersecurity, business operations, engineering, procurement, quality and audit teams.
Process - Establish cybersecurity related processes around procurement, design specifications, implementation, cybersecurity verification / acceptance testing (CFAT or CSAT) pre/post commissioning, operations, a supplier compliance monitoring program to manage suppliers related risks, routine maintenance, and decommissioning.
Technology - Leverage all available key digital technology and security solutions stack for controls or countermeasures throughout the project lifecycle activities.
----------------------------------------------------------------------------------------
✳📢Securing Things - OT Cybersecurity Best Practices Requirements Specification (OT-CBPRS)🎯📜- reference checklist for global SMB Manufacturers - a MVP Offer!✳ (for asset owners only) -
👉Offer valid for both single or multi-site / multi-geographic operations. Large global manufacturers can contact for a custom requirements specification.
🔍Potential Use Cases🎯
Following is a list of potential use cases where by such a reference OT-CBPRS checklist would benefit asset owners:
➡️to self-assess your brownfield implementations to identify potential gaps.✅
➡️to include relevant requirements as part of the RFP/RFQ during procurement stage.✅
➡️Minimum, OT-CBPRS for all GREEN field projects and or existing BROWN field project upgrades. Helps achieve standardization across plant sites for all projects.✅
➡️Supports OT/ICS Cybersecurity Policy and basic elements of an integrated cybersecurity activities throughout the OT Project Lifecycle.✅
➡️Due diligence for identifying basic current state of factories/plant sites during Mergers and Acquisitions to potentially strike a better deal & making informed business decisions.✅
➡️Aligns with several requirements from international regulatory or best practices standards e.g., IEC 62443 standards requirements for Cybersecurity Requirements Specification (CBR) document, NIST etc.✅
➡️Potentially use it as evidence to present it to insurers / brokers while negotiating cyber insurance.✅
➡️Use it as part of due diligence process, during Mergers and Acquisitions, for identifying current state of production sites/facilities in order to potentially strike a better deal & making informed business decisions.✅
Securing Things (Sponsor)
OT CBPRS (Cybersecurity Best Practices Requirements Specification) Toolkit!
➡️Special MVP Offer for Asset Owners (SMB Manufacturers)🎯- Reach out for special price💰offer for the standard checklist or get a custom quote for customized checklist for your environment and for other business needs related to IT/OT cybersecurity project support; - feel free to DM me or reach out at info[@]securingthings[.]com
The Solution (For Asset Owners Only) - Toolkit to get a head start for your OT/ICS Cybersecurity journey for SMB/SME industrial environment. Bonus - comes with limited complimentary seats for IT & OT CySEAT offering.
Below is a brief walkthrough on the toolkit:
(Note: Next iteration would include the ISA/IEC 62443-2-1 Security Program related requirements).
Ways in which I can help?
Whenever you are ready - I can help you with:
A - IT & OT Cybersecurity Advisory / Consulting services - for securing your business and or its digital transformation journey.
B - Security Awareness Training & Phishing Awareness Portal - Train your staff and build a Security awareness program through our subscription based service.
C - Securing Things Academy (STA) - Security trainings for IT & OT practitioners.
Visit the newsletter website for Links to above services and or reach out at info[at]securingthings[dot]com or DM me via LinkedIn.
D - Securing Things Newsletter - Sponsor this newsletter to showcase your brand globally, or subscribe to simply Get Smarter at Securing Things.
Reach out at newsletter[at]securingthings[dot]com or DM me via LinkedIn.
How are we doing?
I invite you as part of #SecuringThings community to share your feedback.
Rate the newsletter content
Your feedback and input is invaluable to me as we work together to strengthen our cybersecurity defenses and create a safer and smarter digital society.
Let us know how we can improve this and or what you’d like to see in future?
Thank you for your trust and continued support.
Do register, validate your email, and request login link to submit poll to be able to enter a chance to win a future course giveaway.
Thanks for reading - until the next edition!
It’s a Great Day to Start Securing Things for a Smart & Safer Society.
Take care and Best Regards,
M. Yousuf Faisal. (Advice | Consult Cyber & business leaders in their journey on Securing Things (IT, OT/ICS, IIOT, digital transformation, Industry 4.0, & AI) & share everything I learn on this Newsletter | and upcoming Academy).
The Newsletter Platform Built for Growth
When starting a newsletter, there are plenty of choices. But there’s only one publishing tool built to help you grow your publications as quickly and sustainably as possible.
beehiiv was founded by some of the earliest employees of the Morning Brew, and they know what it takes to grow a newsletter from zero to millions.
The all-in-one publishing suite comes with built-in growth tools, customization, and best-in-class analytics that actually move the needle - all in an easy-to-use interface.
Not to mention—responsive audience polls, a custom referral program, SEO-optimized webpages, and so much more.
If you’ve considered starting a newsletter, there’s no better place to get started and no better time than now.




