IT & OT Cybersecurity Strategy
Disclaimer: All views presented here, in this newsletter, are my own.
Author or the newsletter are not liable for any actions taken by any individual or any organization / business / entity. The information provided is for education and awareness and is not specific to any business or situation.

Table of Contents
Background
Continuing from one of the previous newsletter edition titled Digital Transformation & Cybersecurity Strategy Premier, a high-level overview on both strategic topics, this edition, will expand further on drafting and writing an IT/OT cybersecurity strategy for any #criticalinfrastructure or given industrial organization.
Cybersecurity Strategy journey begins with discovery process - identifying your business inventory - this includes (but not limited to) - an inventory of IT technology stack, OT/IOT technology stack and Data inventory, across all layers of automation life-cycle + the physical layer (sensors, actuators, machines etc.) for each site along with internal/external connections.

Execution Steps - Discovery / Assessment / Business Inventory
The discovery or assessment process is explained in OT Security Dozen Series Part# 1 – OT/ICS Cyber security Assessments in helping discover the required business inventory.
Next step is identifying the individual(s) and respective team that will be leading the execution of strategy; which is a must have before embarking on this journey, in order to have clear ownership and accountability. Therefore, appointing a suitable CISO / and or Cybersecurity Director or Lead (typically under the CISO or CIO organization) for Cybersecurity program is essential.
Once the business inventory is identified and documented and cybersecurity leader has been appointed, the next logic step is initiating drafting a Cybersecurity strategy document, followed by choosing/selecting a preferred framework to be used as reference to build program elements around.
IT & OT/IOT Cybersecurity Strategy Document
The combined / integrated IT & OT/IOT cybersecurity strategy document takes input from multiple sources (e.g., comprehensive discovery and or assessment exercise) that highlights inventory, associated risks, vulnerabilities and threats and prioritized remediation action plan or road-map.
The strategy document should be reviewed by all stakeholders that are directly responsible, sponsoring and or supporting the execution of the strategy and approved by relevant stakeholders. The content of the document may cover and include the following (an example table of content provided below):
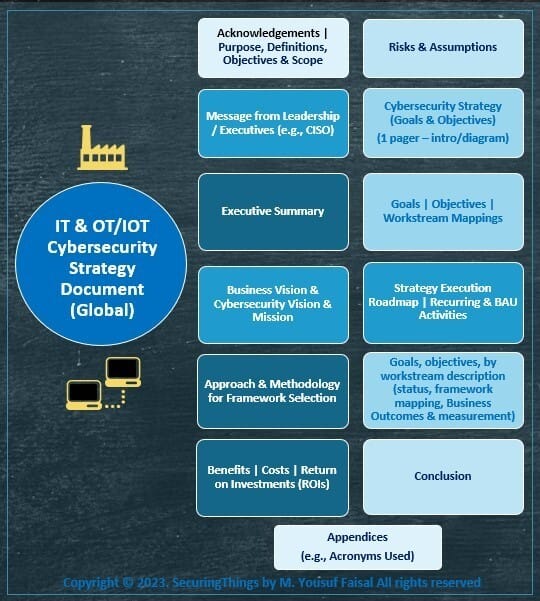
Cybersecurity Strategy Document - Example Table of Content
Keep the document concise and simple to understand, the length of the document should be in between 30-55 pages at most. Update the document whenever necessary and or at-least every 2-3 years cycle.
Next Steps:
Document minimum technical requirements as part of the framework.
Document required cybersecurity policies (Dos' and Don'ts) - for building such policies (checkout the future post “Part # 2 - OT / ICS Cyber security Policy & Governance” from #OTSecurityDozen series).
Document 4.0/IIOT ready secure reference network architecture - (for building one checkout future post “Part # 3 - OT / ICS Network Security Architecture & Segmentation” from the #OTSecurityDozen series).
Next for OT/ICS environment, establish a practice of creating Cybersecurity Requirements Specifications (CRS) (for all greenfield projects and or for brownfield operations upgrades). CRS per #iec62443 standards includes the following:

Elements of Cybersecurity Requirements Specification (CRS)
Reference Strategy Documents
Cybersecurity and Infrastructure Security Agency (CISA) of US have few relevant documents as listed below:
Earlier this week US White House has prescribed a new 69-point National Cybersecurity Strategy Implementation Plan (July 2023) - a new road-map with following 5 pillars:
Pillar One | Defending Critical Infrastructure - Update the National Cyber Incident Response Plan (1.4.1)
Pillar Two | Disrupting and Dismantling Threat Actors - Combat Ransomware (2.5.2 and 2.5.4)
Pillar Three | Shaping Market Forces and Driving Security and Resilience - Software Bill of Materials (3.3.2)
Pillar Four | Investing in a Resilient Future - Drive Key Cybersecurity Standards (4.1.3, 4.3.3)
Pillar Five | Forging International Partnerships to Pursue Shared Goals - International Cyberspace and Digital Policy Strategy (5.1.1 and 5.1.2)
More on this topic in future posts.
In case its time for documenting your 1st IT & OT Cybersecurity Strategy or time for an update/re-write - feel free to reach out to me via DM or get in touch at info[@]securingthings[dot]com for any business needs, project support, discussions and or simply information sharing.
Securing Things (Sponsor)
IT & OT CySEAT (Cyber Security Education And Transformation) course is designed for IT and OT cybersecurity practitioners. Join the wait-list → here.
Checkout a brief overview below:
Ways in which I can help?
Whenever you are ready - I can help you with:
A - IT & OT Cybersecurity Advisory / Consulting services - for securing your business and or its digital transformation journey.
B - Security Awareness Training & Phishing Awareness Portal - Train your staff and build a Security awareness program through our subscription based service.
C - Securing Things Academy (STA) - Security trainings for IT & OT practitioners.
Visit the newsletter website for Links to above services and or reach out at info[at]securingthings[dot]com or DM me via LinkedIn.
D - Securing Things Newsletter - Sponsor this newsletter to showcase your brand globally, or subscribe to simply Get Smarter at Securing Things.
Reach out at newsletter[at]securingthings[dot]com or DM me via LinkedIn.
How are we doing?
I invite you as part of #SecuringThings community to share your feedback.
Rate the newsletter content
Your feedback and input is invaluable to me as we work together to strengthen our cybersecurity defenses and create a safer and smarter digital society.
Let us know how we can improve this and or what you’d like to see in future?
Thank you for your trust and continued support.
Do register, validate your email, and request login link to submit poll to be able to enter a chance to win a future course giveaway.
Thanks for reading - until the next edition!
It’s a Great Day to Start Securing Things for a Smart & Safer Society.
Take care and Best Regards,
M. Yousuf Faisal. (Advice | Consult Cyber & business leaders in their journey on Securing Things (IT, OT/ICS, IIOT, digital transformation, Industry 4.0, & AI) & share everything I learn on this Newsletter | and upcoming Academy).
The Newsletter Platform Built for Growth
When starting a newsletter, there are plenty of choices. But there’s only one publishing tool built to help you grow your publications as quickly and sustainably as possible.
beehiiv was founded by some of the earliest employees of the Morning Brew, and they know what it takes to grow a newsletter from zero to millions.
The all-in-one publishing suite comes with built-in growth tools, customization, and best-in-class analytics that actually move the needle - all in an easy-to-use interface.
Not to mention—responsive audience polls, a custom referral program, SEO-optimized webpages, and so much more.
If you’ve considered starting a newsletter, there’s no better place to get started and no better time than now.


