PART # 1 – OT/ICS Cybersecurity Assessments
This is Part 1 of The OT Security Dozen – a 12-part series of building an OT / ICS Cyber security Program for an industrial operations environment - 2022, a year of OT/ICS Cyber security Assessments.
Originally published on LinkedIn Securing:Things newsletter on March 11, 2022..
Note: you may have noticed that OT/ICS Cyber security awareness is a common theme across "The OT Security Dozen" and hence no exclusive part on awareness itself. The aim for this post/series is to raise awareness on each type of controls covered and hence is considered an essential/integral necessity across this 12-part series.
Table of Contents

In recent years, especially since pandemic; the world has seen, read and experienced a significant rise of cyber-physical attacks exploiting vulnerabilities and process weaknesses across multiple industrial sectors; eventually leading to downtime and breaches, impacting business operations for organizations worldwide. And if you’ve been reading industry threat intel reports and or predictions for 2022; the future isn’t any bright. To make things worse, the pace of digital transformation (to 4.0 or 5.0) driven by accelerated competition and growth, isn’t going to slow things down either, on the contrary, going accelerate it. This eventually necessitates the need for continuous cyber risks evaluation and measurement on OT / ICS Cyber security side in addition to attention generally been given on the IT side.
Have spoken to several end user organizations over past 2 years; on a wide variety of Cyber security needs, guiding them on a typical OT/ICS Cyber security strategy, most of them were convinced that discovering and accessing the current OT/ICS operations Cyber security maturity state is the right first step. Since pandemic, APAC market have seen an increased awareness from industrial organizations to start exploring their OT/ICS Cyber security journey by performing such reviews/assessments. However, many still struggle to understand and or justify the need for such.
My goal for this post, is to help “end user / operator” organizations (especially, manufacturing sector) understand typical drivers behind such assessments, dynamics of such an exercise or a project, type of assessments options available to choose from and typical execution methodology for an increased awareness of the process. Ultimately the goal is to familiarize with engagement and execution process for identifying OT/ICS Cyber security risks, maturity state, for creating a strategy and road-map for building an OT/ICS Cyber security Program for continuous improvement and measurement.
Need for OT/ICS Cybersecurity Assessments / Reviews
Why Industrial Clients needs ICS/OT Cyber security Assessments?
Except for few slightly mature industrial or critical infrastructure sectors e.g., utility/power - many manufacturers in Asia Pacific, have just only started exploring or plan on doing OT/ICS Cyber security assessments against their plant/production control networks environments - (even though many of these manufacturers are part of global operations).
There are perceived myths or objections that some of the stakeholders within an end-user / owner/operator may have e.g., it’s risky and would impact my production environment or my operations is running for several years, nothing has happened to me, why would anyone want to target my environment. There's enough attack, incident and breach data available to overcome and address such myths. Regardless of the industrial sector you are part of, some other common drivers or triggers for such an initiative could potentially be e.g., compliance/regulatory driven, in response to breach/incident, led by digital transformation projects that warrants a closure look at Cyber security and or other needs around improving overall risk visibility and awareness.
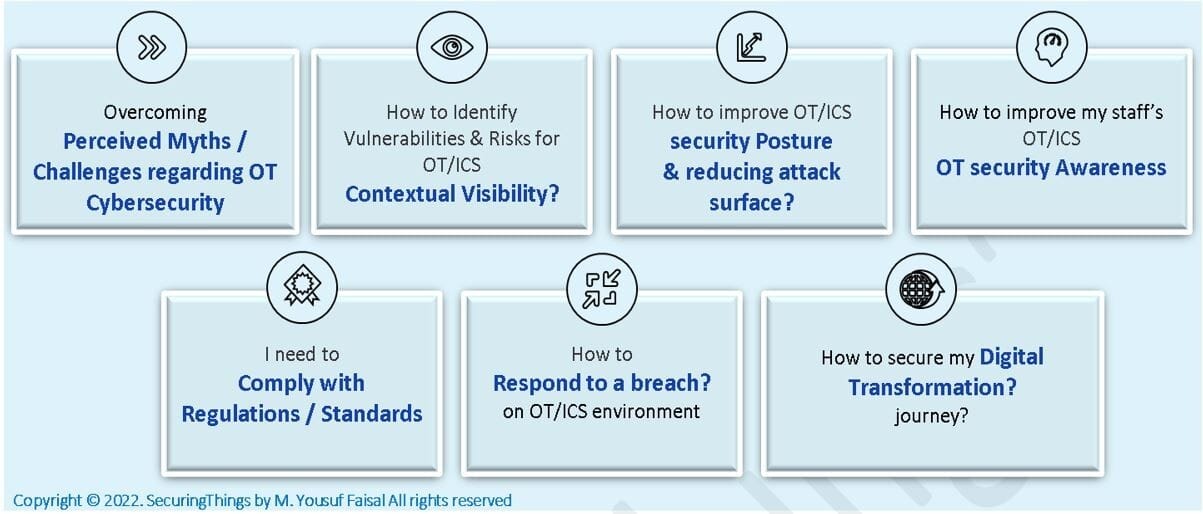
Typical drivers for OT/ICS Cyber security Assessments
Options for OT/ICS Assessments
For OT Cyber security Assessments - Clients depending on their industry needs and maturity of their environment & where they are at - have few assessment options (with slightly different target goals) to choose from. Some of these options are presented below.

Options for OT/ICS Cyber security Assessments
If your organization is embarking on this journey for the 1st time, you should be a bit thorough in your assessment process vs organizations that are much mature and have done this several times. Whichever option you choose; the best approach is the one that combines both manual means (i.e., documentation reviews + interviews + site walk-through) and technical discovery (i.e., logically collect data utilizing different technical tools/techniques) and optionally supported with scenario driven threat analysis to get a complete validated state of your operations. As simply relying on manual methods, means that you are accepting the unknown risks that are not discovered until validated via technical means/techniques.
Evaluation and Engagement
Once you’ve selected the direction, look to see whether you’ve internal skill sets and SMEs within the organization to perform such an exercise. If you lack resources and or expertise, always engage a trusted and an experienced 3rd party consultant or service provider. Define scope of the engagement and develop selection criteria for evaluating responses from 3rd parties.
Note: More on how to evaluate and create criteria for 3rd party/vendor assessment selection to be covered in future extension to this series.
Mapping to Industry Standards

OT/ICS Cyber security Assessment / Review Methodology
OT/ICS Cyber security Project Life-cycle – Phases
A typical OT/ICS Cyber security Project life-cycle approach span across distinct stages:
Stage 1 = Discover & Assess your environment,
Stage 2 = Identify controls/security levels, build a prioritized and actionable road-map.
Stage 3 = (Remediate &) Implement
Stage 4 = Maintain
For the purpose of this article – Phases 3 and 4 are not discussed (to be covered in future posts) and we’ll keep a focus on stage 1 and 2 for the rest of this article.
OT/ICS Assessments – Execution Approach & Flow
Assessment execution follows an iterative process, while performing certain tasks with each step having a defined goal/milestone. Typically, such an engagement, depending upon the size and complexity and industry sector can take anything in between a couple of weeks or even few months. Below diagram depicts an example step wise execution approach and flow:

OT/ICS Cyber security Assessments – Execution Approach & Flow
OT/ICS Cyber security Assessment – Technical Tools & Techniques
In terms of the cool technical part of such an OT/ICS Cyber security assessments / review – some of the technical analysis techniques (but not limited to) that we can use to achieve our assessment goals are highlighted in the figure below at a high-level (without focusing on the tools itself).

OT/ICS Cyber security Assessments – Tools & Techniques
In terms of tools, a combination of certain specialized open source and commercial specialized OT security and IT security tools can potentially be leveraged. Key thing to note here is that by utilizing these techniques we can get a high value outcome with low or no impact to OT or production environment.
OT/ICS Network Architecture View
At the heart of the assessment is – OT/ICS network architectural review of in-scope plant operations. Often labelled with different terms like OT/ICS network, Plant or Process control network (PCN) / an Industrial automation and control systems (IACS) network, or simply the production network.
When it comes to analysing the OT/ICS network Architecture reviews as part of the assessment; a common approach is to analyse the environment and its traffic flow against ISA Purdue Reference Model (PRM)– which is a method of grouping of technologies based on their criticality to cyber-physical process. Below is an example figure highlighting the Purdue levels.

OT/ICS Network Architecture View – Purdue Enterprise Reference Architecture (PERA)
Organizations that follow PRM segmentation – choose one of the following three options:
Physical Segmentation – is an old method but still being used in many environments
Segmentation with Security Zones/VLANs – focused on traffic control from North-South.
Micro-segmentation by Policy or Layer 7 – focused on traffic control from North-South.
Several environments are also working towards building their OT/ICS Cloud Strategy as part of their IIOT/Industry 4.0 or digital transformation initiatives by planning to push data out of OT to cloud / middle-ware which eventually will require an approach with both north-south and east-west traffic controls & monitoring.
A secure OT network architecture is the 1st level of defense, a strong perimeter between business and production control or OT network is essential, but not enough. We need to build additional sub-perimeters inside the control network. So, Level 3 / 4 is the most important security perimeter and Level 2, and Level 1 are most critical because they directly influence the process. Within the controls network Level 0 to Level 3 - we can create sub-security zones. The Ultimate goal is to be able to build a reference architecture is to identify data flows within or between different security zones and whether the traffic is required to be allowed or restricted. Building these rules will help ensure that attack surface is greatly limited. Everything that is accessible from your less trusted zone to your more trusted zone is an attack surface. The attack surface should shrink as you go further down the PRM as shown in the figure below.

OT/ICS Network Architecture View – Purdue Enterprise Reference Architecture (PERA)
Note
• More on this in Part 3 - OT/ICS Cyber security Architecture & Segmentation (between IT & OT networks) (Phase 2 - Implement | Deploy (Protect & Detect)
• I've not shown the safety zone separately, however, several enforcement's need to be in place for safety systems i.e., ideally disconnected from other networks – air gaped may be desirable. However, in most safety information systems (SIS) implementation scenarios, this is not possible because safety system sometime needs to take over control from the primary logical control, to tell the controller that it has seized control of responsibility of the operations. Apply protective controls such as unidirectional gateways / data diodes, and ICS/OT firewall between the systems. SIS is the most important system and will prevent the worst-case scenario. Attacker should never be able to get to safety system.Identify & Build - Business Inventory as part of the process
Its’ highly recommended that as you progress through the process, either identify if the system under consideration (SUC) has a proper business (/assets) inventory. If none exists, it’s important to build one. For each layer or level of Purdue model start building a list of all hardware or software or system components. Knowing the classification and criticality of assets are essential to understand which assets are critical to the production operations and or deals with sensitive data. This will also help in discovering risks and vulnerabilities. You can’t protect what you don’t know exists.
Note: Building such a Business (Asset) Inventory and mapping all hardware / software / systems components is also going to be an invaluable and common step, especially if your environment is planning or initiating a Digital Transformation Maturity Assessment (DTMA) as part of industry 4.0 transformation journey.
OT Cyber security - Security and Maturity Levels
Once you have done the manual and technical discovery along with the architecture review, now it’s time to start defining the current security and maturity levels and plan to define target security and maturity levels. In order to do this, you've the option to select and or can define your own security and maturity levels, as part of the analysis for building a model-based progressive improvement plan, depending upon the ease, familiarity and maturity of your environment. E.g.: if you are using standards like ISA/IEC 62443 as the basis of your assessments, it’ll provide you with different security levels (target, achieved, capability) with ISA/IEC 62443-3-3 defining 5 different security levels (SL) (0, 1, 2, 3 and 4), each with an increasing level of security and for identifying current and target maturity levels, C2M2 or CMMI based maturity models can be utilized in conjunction with security levels to understand relevant protection levels.
Analysis, Reporting & Presentation
After analysis is done, the report should clearly highlight the scope with system under consideration and any limitations and at bare minimum. Ideally the report should be divided into:
Executive Summary with overall dashboards or heatmaps, (optional) benchmark data against industry peers and short/concise overall analysis focused for executive stakeholders,
Management Summary with prioritized remediation roadmaps, and
Technical Details highlighting all observations, technical gap details, risks/vulnerabilities, and recommendations (short term and long term – both tactical and strategic) along with current and target/future maturity state for all different domains/topics, list of security controls missing / required and clear mapping of baseline and recommended controls.
The Presentation should provide a concise summary of the report that is easy to digest and follow.
Note: More on reporting and presentation to be covered in future posts.
Below is an example OT/ICS Cyber Risk Strategy, mapped to different project lifecycle from Strategy, Architecture to Implementation to Run/Operations phases. While certain activities are mapped to 4 stages of Prevent, Predict, Detect & Respond of Gartner adaptive security model for OT security. (Note: this is not an exhaustive list and presented as an example only).

OT/ICS Cyber security Strategy – High level Example Only
Recommendations
If haven’t done so before, immediately engage an experienced independent consultant/third-party to perform an IT-OT or OT/ICS specific Cyber security assessment. It’s important to identify assets, vulnerabilities and risks to OT/ICS operations environment so to apply preventive and detective controls. Ensure enough planning or preparation is done, and the project is socialized with relevant stakeholders to get appropriate time and resource commitments.
Key Takeaways
Once the outcome from assessment and potential gaps are available – you are on your way of building a secure-by-design OT Cyber security strategy, aligned with organizational business needs with:
Defined business priorities (input from risk or business impact analysis, regulations/legal, revenue, safety & public perception)
most to least critical assets identified – i.e., Prioritization & Classification of assets have been determined accurately.
Cyber risks identified, based on analysis via Threat & Consequences driven Scenarios (e.g., Malware, Ransomware, IP Theft/data leak etc.)
Security controls identified & selected (Preventive, Detective, and Responsive) - each will have some implications from a people, process, and technology perspective, mapped to your choice of industry standards and or framework/regulations against which compliance is required.
Execute the strategy & continue to monitor on-going measurement. (e.g., measure KPIs against threat scenarios across different asset classification and analyse when new threat/scenarios emerge).
Based on your budget and resources, the aim is to constantly be maturing the OT/ICS environment.
NEXT STEPS:
Understanding your current risk profile to chart your future IT/OT/IIOT Cyber Security Strategy starts with OT/ICS Cyber security Assessments (Risk & Maturity).

OT/ICS Cyber security Assessments – Take Next Steps
Feel free to reach out if you have similar concerns or needs.
It’s a great day to start SecuringThings!
#securingthings #digitaltransformation #ot #ics #otsecurity #otsecuritydozen #otcybersecurity #icssecurity #isa #icscybersecurity #sgcii #securedigitaltransformation #operationaltechnology #industry40 #iec62443 #criticalinfrastructure #criticalinfrastructureprotection #manufacturing #criticalinformationinfrastructure #securityawareness #otsecurityawareness #icssecurityawareness #otstrategy #iiot #icscybersecurityprogram #otcybersecurityprogram #industrialcontrolsystems #industrialautomation
The Newsletter Platform Built for Growth
When starting a newsletter, there are plenty of choices. But there’s only one publishing tool built to help you grow your publications as quickly and sustainably as possible.
beehiiv was founded by some of the earliest employees of the Morning Brew, and they know what it takes to grow a newsletter from zero to millions.
The all-in-one publishing suite comes with built-in growth tools, customization, and best-in-class analytics that actually move the needle - all in an easy-to-use interface.
Not to mention—responsive audience polls, a custom referral program, SEO-optimized webpages, and so much more.
If you’ve considered starting a newsletter, there’s no better place to get started and no better time than now.



