Digital Transformation & Cybersecurity Strategy - Premier
Disclaimer: All views presented here, in this newsletter, are my own.
Author or the newsletter are not liable for any actions taken by an individual or an organization / business / entity. The information provided is for education and awareness and is not specific to any business or situation.
Table of Contents
Digital Transformation (DT) from an industry 4.0 perspective is not a project but rather a strategy or a journey. Similarly, defining IT & OT Cybersecurity strategy and achieving maturity is also a journey and not a project in itself.
While cybersecurity needs to be an integral part of the overall DT strategy as a whole, for any smart critical infrastructure and or manufacturing business, it is important to understand that its not limited to the DT strategy but is applicable to the entire business operations as a whole (beyond DT initiatives).
Any DT initiative ignoring the importance/need of cyber-security, increases cyber risks to operations, and could potentially create major issues/hurdles for a long-term DT strategy and can turn out to be costly for the business. DT is one of key drivers for many businesses initiating their cyber-security program.
Stakeholders from both the DT team (e.g., Chief Digital Officer (CDO) / Director) and Cybersecurity team (e.g., Chief Information Security Officer (CISO)) need to understand the key tenants of a typical strategy / journey, each team plans to embark on, and should have common understanding of key goals to meet business objectives.
The diagrams below represents, at a high-level, an example of the steps both teams may initiate, or draw parallels from, to support each other's strategic objectives - rather than being in conflict with each other. Both programs need to cover all areas of automation stack (per ISA 95 - part 2).
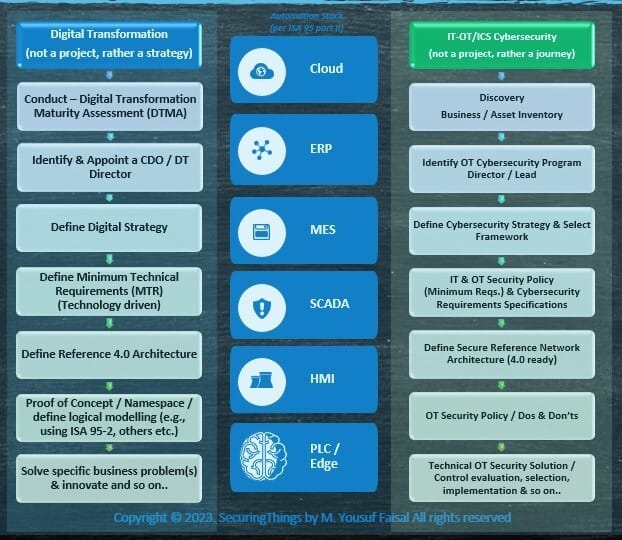
Example Steps for DT Strategy & Cybersecurity Journey
some more context on the above steps, below:

Example Steps for DT Strategy & Cybersecurity Journey Brief
If you are embarking on such a journey, whereby both teams are starting certain initiatives in these two areas, it is always good to work as a single virtually integrated business unit/team to avoid repetitive tasks (e.g., conducting discovery on business inventory) and save business time, effort and costs on any potentially overlapping activities.
Businesses that are planning expansion (e.g., green fields projects / implementation) are in a perfect position to define, align and execute both these strategies.
For businesses planning for (or going through) mergers & acquisitions within the industrial space - if the newly acquired business, presents higher cyber risk levels with lower maturity in these areas, the overall organizational maturity (and compliance) can be impacted and can potentially cause negative consequences to the business. It may also require a re-organization of these two teams. Therefore, it's highly critical that the acquisition party, as part of due diligence process, considers reviewing the maturity around these two strategies to identify cyber risks, and also potentially presents an opportunity to leverage the findings, to better negotiate the right deal.
More on this topic in future posts.
Feel free to reach out or get in touch at info[@]securingthings[dot]com for any business needs, project support, discussions and or simply information sharing.
Securing Things Academy:
IT & OT CySEAT (Cyber Security Education And Transformation) course is designed for IT and OT cybersecurity practitioners. Join the wait-list → here.
Checkout a brief overview below:
Ways in which I can help?
Whenever you are ready - I can help you with:
A - IT & OT Cybersecurity Advisory / Consulting services - for securing your business and or its digital transformation journey.
B - Security Awareness Training & Phishing Awareness Portal - Train your staff and build a Security awareness program through our subscription based service.
C - Securing Things Academy (STA) - Security trainings for IT & OT practitioners.
Visit the newsletter website for Links to above services and or reach out at info[at]securingthings[dot]com or DM me via LinkedIn.
D - Securing Things Newsletter - Sponsor this newsletter to showcase your brand globally, or subscribe to simply Get Smarter at Securing Things.
Reach out at newsletter[at]securingthings[dot]com or DM me via LinkedIn.
How are we doing?
I invite you as part of #SecuringThings community to share your feedback.
Rate the newsletter content
Your feedback and input is invaluable to me as we work together to strengthen our cybersecurity defenses and create a safer and smarter digital society.
Let us know how we can improve this and or what you’d like to see in future?
Thank you for your trust and continued support.
Do register, validate your email, and request login link to submit poll to be able to enter a chance to win a future course giveaway.
Thanks for reading - until the next edition!
It’s a Great Day to Start Securing Things for a Smart & Safer Society.
Take care and Best Regards,
M. Yousuf Faisal. (Advice | Consult Cyber & business leaders in their journey on Securing Things (IT, OT/ICS, IIOT, digital transformation, Industry 4.0, & AI) & share everything I learn on this Newsletter | and upcoming Academy).
The Newsletter Platform Built for Growth
When starting a newsletter, there are plenty of choices. But there’s only one publishing tool built to help you grow your publications as quickly and sustainably as possible.
beehiiv was founded by some of the earliest employees of the Morning Brew, and they know what it takes to grow a newsletter from zero to millions.
The all-in-one publishing suite comes with built-in growth tools, customization, and best-in-class analytics that actually move the needle - all in an easy-to-use interface.
Not to mention—responsive audience polls, a custom referral program, SEO-optimized webpages, and so much more.
If you’ve considered starting a newsletter, there’s no better place to get started and no better time than now.



