Disclaimer: All views presented here, in this newsletter, are my own.
Author or the newsletter are not liable for any actions taken by any individual or any organization / business / entity. The information provided is for education and awareness purposes only and is not specific to any business and or situation.
Hi Securing Things Community,
📢 Cybersecurity or Digital Transformation Maturity Assessment + Sample Request for information (RFI)!🛡️
Many manufacturers, still struggle with starting out on defining and or executing their Digital Transformation and or Cybersecurity Strategies and maturity (yes, both journeys have a completely different focus and goal). One that would drive innovation for production operations to help produce more with less, predict failures and provide state of production operations in real-time accurately, and the other that could potentially ensure that operations stay resilient to cyber threats and consequently avoid any production loss / downtime respectively.
But there are solutions to both these problems and help is available out in the market.
Special Message:
Before we begin, do me a favour and make sure you hit the “Subscribe” button to let me know that you care and keep me motivated to publish more. Thanks!
If you are in this situation, your manufacturing environment is most probably at risk, both at, getting crushed by competition, and or getting penetrated by the adversaries.
Whether you are CIO, CISO, OT / automation expert, or part of operations senior leadership team and have recognise the crucial importance of having both strategies in place, act now and raise political capital awareness internally.
Though these two strategies have totally different focus, goals, skills sets required, organisational alignment, investments and support needs, however, they have some commonality in terms of the approach and execution. I have highlighted some in a previous article titled “Digital Transformation & Cybersecurity Strategy - Premier”.
Securing Things Academy:
IT & OT CySEAT (Cyber Security Education And Transformation) course is designed for IT and OT cybersecurity practitioners. Join the wait-list → here.
Checkout a brief overview below:
Discovery - Business Inventory!
One of the first steps in both Digital transformation and Cybersecurity strategy journey is discovering and identifying the business inventory. This foundational step helps:
OT Solution Architects or industry 4.0 leaders or System Integrators identify the current state of the business (i.e. 3.0 or 4.0 and which processes could potentially be automated). May also potentially identify what you were doing wrong if previous transformation efforts have failed. Key is choosing the right partner.
OT Security Architects or Cybersecurity leaders identify the current state with assets, associated vulnerabilities, and related attack surface for the organisation. Interested in learning more on OT security assessments, check out a previous article on OT/ICS Cybersecurity Assessments/Reviews.
To support such an exercise, you’ll need to plan and request for data and information collection. Below is an example sample Request for Information (RFI) and Workshop tracking worksheet that I’ve used while performing initial discovery (note - this is not an exhaustive list and may vary per project needs). Develop one that suits your specific project goals accordingly.
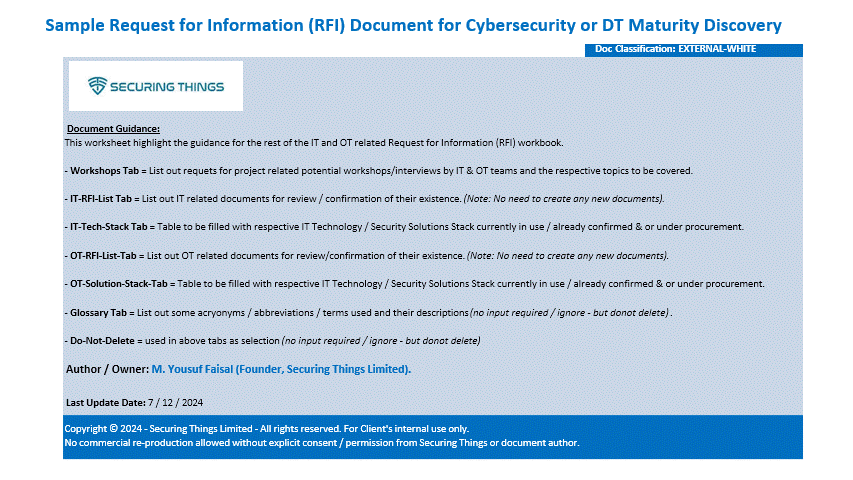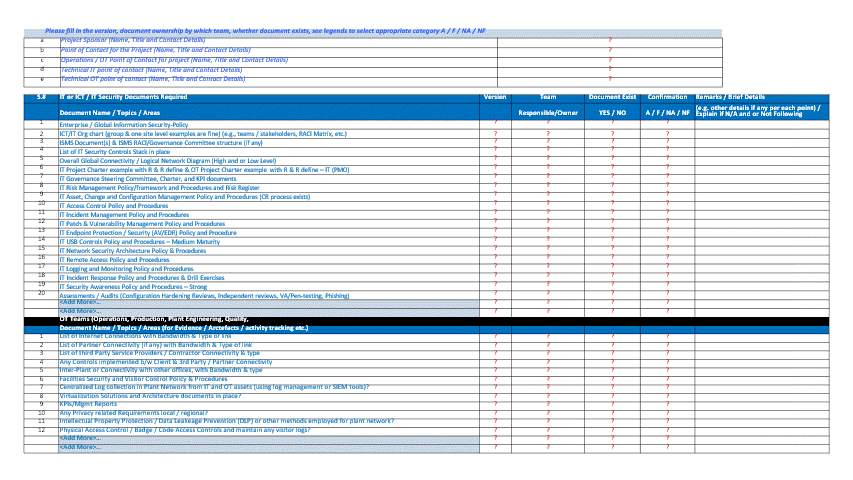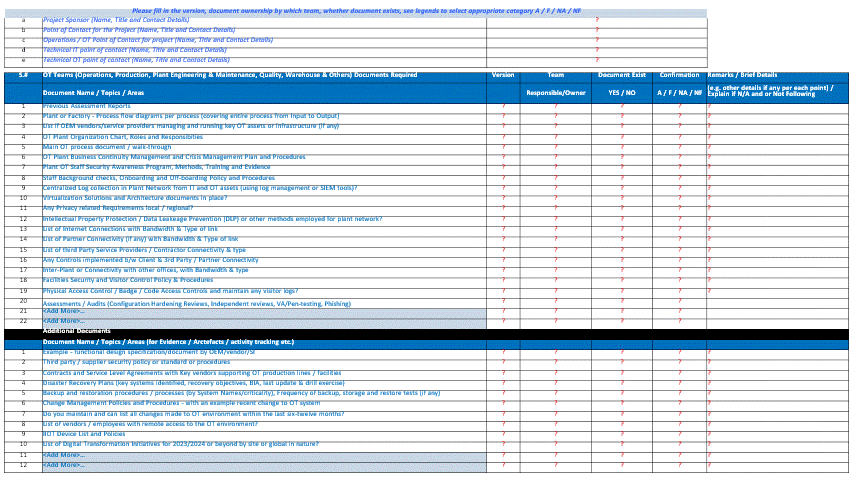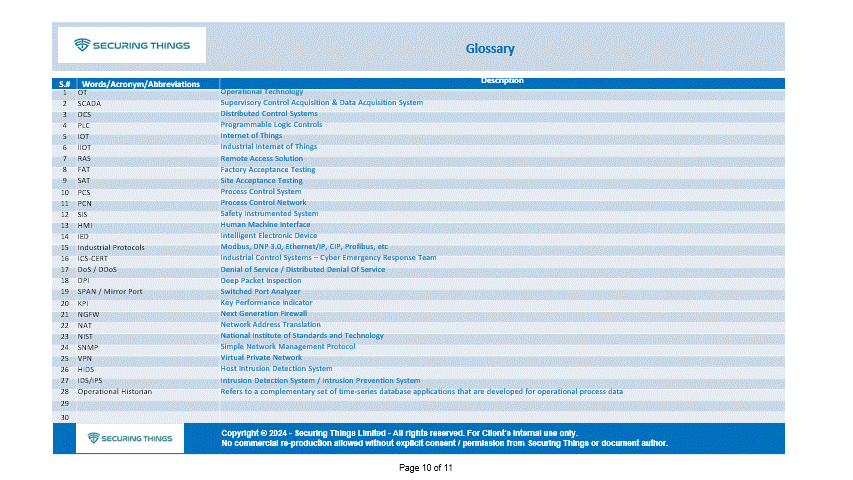
Sample RFI, part of IT-OT CySEAT Course
You’ve Done the initial Discovery - Now What?
After completing the discovery phase, which involves conducting interviews with personnel from both the IT and OT/production control network teams, reviewing relevant documents and network architecture, conducting a walkthrough of the plant floor, and collecting data such as manual processes, printouts, packet captures, configuration details, and connectivity information:
for the digital transformation maturity review - your solution architect would have identified your digital transformation maturity level / scale, established potential transformation use cases.
for the cybersecurity maturity review - your OT security consultant or architect would have identified potential cybersecurity risks and improvement opportunities in terms of people, processes and technology.
Cyber Defense Matrix across Automation Stack
A possible way of looking at your business inventory and data collected is to use Cyber defense matrix (by Sunil Yu) and identify devices, applications, networks, data and users at each layer of automation stack (from cloud to factory floor down to the PLCs/edge or physical devices), potential risks and security controls around pre-cyber event and post-cyber event.

Each layer of Automation Stack, assessed for Devices, Apps, Networks, Data, & Users
Above diagram highlights a sample list of potential security controls that may exists, or may be missing, suitable or required for your environment. The cyber defense matrix, also shows you the degree of effort / dependency across people, process and technology to implement any of these security measures. This is just one of the many ways to present cyber security controls gaps for easy understanding.
Note: Once you’ve established a baseline need for addressing cyber risks, and completed your rapid assessment, execute remediation / strategy and as you gradually mature perform a thorough Digital Transformation Maturity Assessment (using RAMI or others) and or Cybersecurity risk assessment (using standards like ISA/IEC 62443), respectively for your environment.
There’s much more to securing things for your digital manufacturing environment.
Approach the two pronged problem that puts your manufacturing business at risk, at the pre-eval phase together, and help save your business time, money and resources.
CIOs, CISOs, CDOs, OT / Automation leaders, how are you addressing these different needs for your manufacturing environment to making sure you remain competitive and also secure? - do type in comments below and enrich this resource.
My Recent Most Viewed Social Posts
In case you’ve missed - here are some of my recent most viewed social posts.
Quantum Computing Cybersecurity Crash Course - the Future Security Concerns.
"Boost Your Defense Game - IT & OT/ICS Cybersecurity Training [Securing Things by M. Yousuf Faisal]"
IT & OT/ICS CySEAT - only on Securing Things Academy (40% off) - Training course brief introduction.
🚀 Ready to Transform Your Career? Dive into IT & OT/ICS Cybersecurity🔐- Phase A - Getting started in IT & OT/ICS Cybersecurity.
🚀 Ready to Transform Your Career? Dive into IT & OT/ICS Cybersecurity🔐- Phase B - Getting started in IT & OT/ICS Cybersecurity.
🚀 Ready to Transform Your Career? Dive into IT & OT/ICS Cybersecurity🔐- The 3 Phase, 12 steps blue print - Getting started in IT & OT/ICS Cybersecurity.
🚀 Ready to Transform Your Career? Dive into IT & OT/ICS Cybersecurity🔐- 4 personas perspective, for 3 phase blue print - Getting started in IT & OT/ICS Cybersecurity.
Getting OT/ICS visibility for industrial, data centre or smart buildings environments.
IT & OT Security Dozen framework for building, executing & managing a Cybersecurity & Resilience Transformation Program.
Securing Things Academy:
IT & OT CySEAT (Cyber Security Education And Transformation) course is designed for IT and OT cybersecurity practitioners. Join the wait-list → here.
Checkout a brief overview below:
Ways in which I can help?
Whenever you are ready - I can help you with:
A - IT & OT Cybersecurity Advisory / Consulting services - for securing your business and or its digital transformation journey.
B - Security Awareness Training & Phishing Awareness Portal - Train your staff and build a Security awareness program subscription based service.
C - Securing Things Academy (STA) - Security trainings for IT & OT practitioners.
Visit the newsletter website for Links to above services and or reach out at info[at]securingthings[dot]com or DM me via LinkedIn.
D - Securing Things Newsletter - Sponsor this newsletter to showcase your brand globally, or subscribe to simply Get Smarter at Securing Things.
Reach out at newsletter[at]securingthings[dot]com or DM me via LinkedIn.
How are we doing?
I invite you as part of #SecuringThings community to share your feedback.
Rate the newsletter content
Your feedback and input is invaluable to me as we work together to strengthen our cybersecurity defenses and create a safer and smarter digital society.
Let us know how we can improve this and or what you’d like to see in future?
Thank you for your trust and continued support.
Do register, validate your email, and request login link to submit poll to be able to enter a chance to win a future course giveaway.
Thanks for reading - until the next edition!
It’s a Great Day to Start Securing Things for a Smart & Safer Society.
Take care and Best Regards,
M. Yousuf Faisal. (Advice | Consult Cyber & business leaders in their journey on Securing Things (IT, OT/ICS, IIOT, digital transformation, Industry 4.0, & AI) & share everything I learn on this Newsletter | and upcoming Academy).


