Disclaimer: All views presented here, in this newsletter, are my own.
Author or the newsletter are not liable for any actions taken by any individual or any organization / business / entity. The information provided is for education and awareness purposes only and is not specific to any business and or situation.
Table of Contents
Hi Securing Things Community,
Are you aware of IT & OT cybersecurity career roadmaps / competence framework available? have you planned your career progression?
Are you:
a recent graduate or learner
an automation / OT / ICS professional
an existing IT security professional
an experienced professional from a non-IT/Security/Automation field
And want to learn more about cybersecurity career roadmaps? If so;
In this newsletter edition, we’ll continue to expand on “Getting started in IT & OT Cybersecurity”, covering “Phase A and Step 4”. In addition, I’ll be sharing few interesting Cybersecurity competence framework links, my recent most viewed social media posts from June 2024, updates on Securing Things Academy and my asks.
Special Message:
Before we begin, do me a favour and make sure you hit the “Subscribe” button to let me know that you care and keep me motivated to publish more. Thanks! Note: remember to validate your email address to ensure that you don’t miss any future newsletter editions.
1. Phase A - Initiate, Validate, Prepare & Plan
Phase A, as the name implies is all about initiating, validating, preparing and plan - doing the preliminary work check before you take a leap of faith on getting started in cybersecurity.
In this newsletter, let’s expand and talk about Step 4. Last step in Phase A.
But in case, if you are seeing this for first time or you’ve missed the previous 3 posts for my 3 phase & 12 steps blueprint, here are the links below:
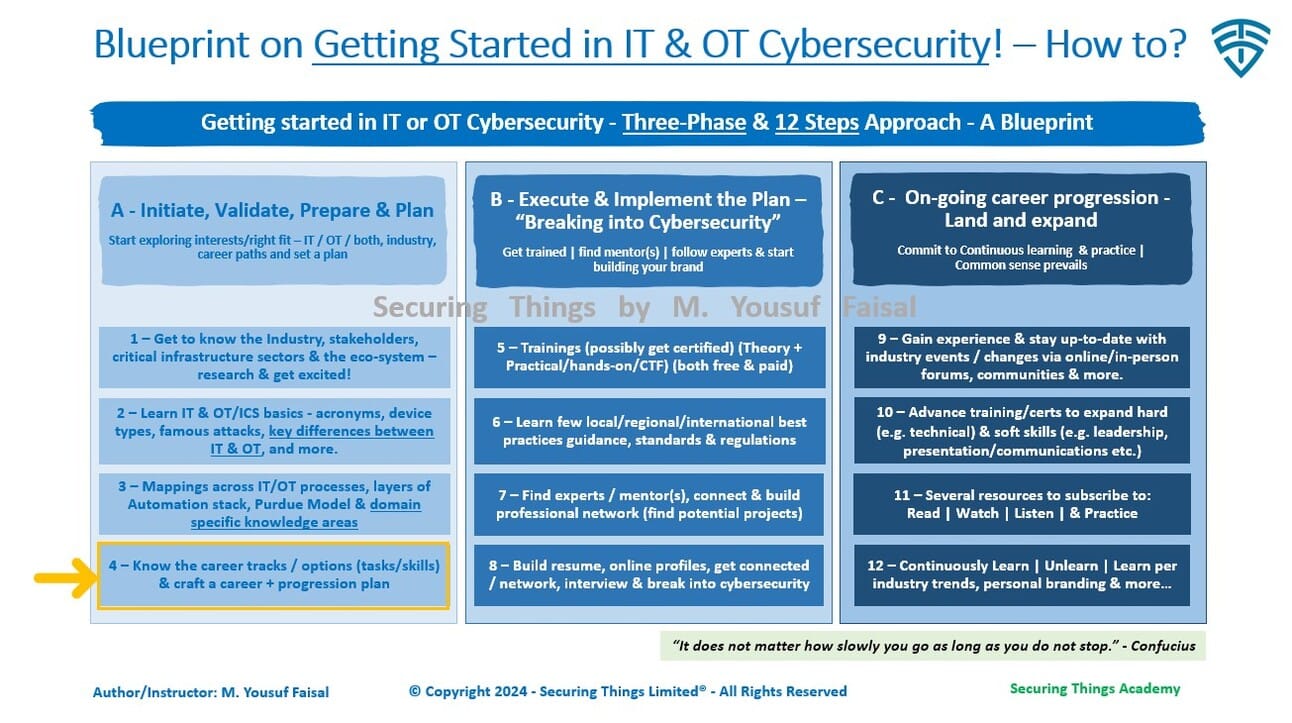
Step 4 - Getting started in IT & OT Cybersecurity - Blueprint by M. Yousuf Faisal
Step 4 – Know the career tracks / options (tasks/skills) & craft a career + progression plan.
So now that you’ve had some understanding of all the basics around terms/acronyms, basic security concepts and priorities for IT and OT/ICS from step 1, step 2, and step 3. We are now going to dive in on the career tracks / options.
👉– Whether you are a recent graduate or learner, OR an experienced professional from a non-IT/Security/Automation field, OR an automation professional, OR an existing IT security professional - should know some of the example highlighted cybersecurity competence frameworks below - these are handy resources to plan for your career progressions - but not mandatory to be followed exactly. Research, validate your areas of interests that you’re more likely going to enjoy learning/practicing. Some career tracks are more technical and hands-on compared to others. Choose wisely, as you have limited time, energy and budgets.
More broadly, the competencies can be spread across IT & OT cybersecurity side:
Leadership Roles
Governance, Risks & Compliance (/Audit) and Legal
Prediction / Intelligence / Researchers
Offensive/Ethical Hackers - focus on security testing/exploitation (often called RED Teams)
Defenders - focus on Protection/Detection: (often called Blue Teams)
Architects / Designers / Product or Development
Deployment / Implementation
Operations / maintenance
Responders - security monitoring, incident response, malware researchers (often called Blue Teams)
Creators / founders - solving any of the above industry problems.
👉– There are a number of government and private sector guidance available - use it and build STBOK (securing things body of knowledge) (yes an acronym I introduced in Step 1 of the blueprint). Here is an example list of cybersecurity competence frameworks for IT & OT Cybersecurity:
NICE Framework (NIST SP 800-181r1) by NIST - a US national cybersecurity competency framework commonly referred to as the NICE Framework. In March 2024, NICE Framework Components v1.0.0 was released. It builds a common lexicon and applies across public, private, and academic sectors. Divides in 7 Work Role Categories (high-level grouping of common cybersecurity functions) as shown below:
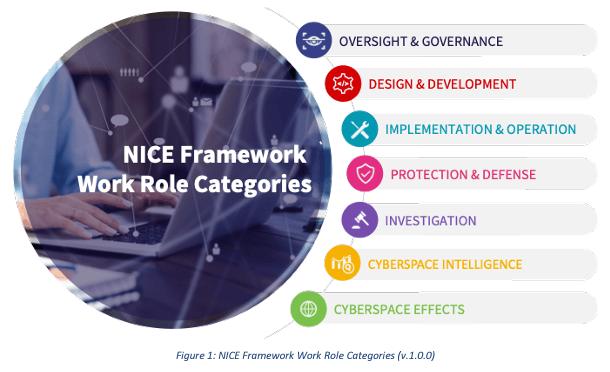
Source: NIST/NICE framework document
Canadian cyber security skills framework (ITSM.00.039) - is based on NICE framework as well. This is an unclassified publication that has been issued under the authority of the Head of the Canadian Centre for Cyber Security (Cyber Centre).
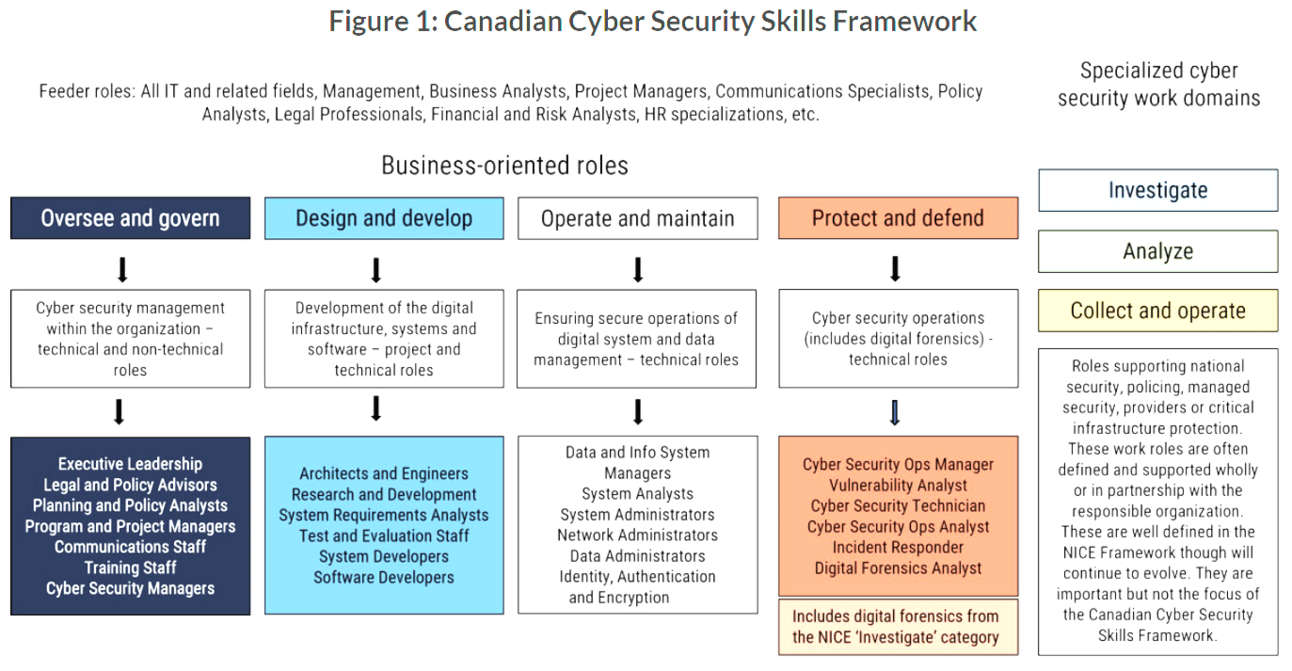
Source: Canadian Cybersecurity Skills Framework
European Cybersecurity Skills Framework (ECSF) - build a common understanding of cybersecurity professional role profiles in Europe and common mappings with the appropriate skills and competences required. Below is a list of 12 typical cybersecurity professional role profiles along with their identified titles, missions, tasks, skills, knowledge, competences.

Source: ENISA Competence Framework - for European Cybersecurity Professionals
UK Cyber Skills Framework by UK Cyber Skills Council - outlines the career path in cybersecurity with 16 specialist categories and suggests pathways through and between them. Not mandatory to be followed.

Source: UK Cyber Skills Council
ASD Cyber Skills Framework - The ASD Cyber Skills Framework v.2.0 captures updates from the frameworks that support it: Skills Framework for the Information Age 7 (SFIA 7) and the Chartered Institute for Information Security (CIISec) Framework v.2.4 (formerly the Institute for Information Security Professionals). Focuses on the capabilities, skills and levels of nine cyber roles which have been grouped under four disciplines.

Source: ASD Cyber Skills Framework
The Saudi Cybersecurity Workforce Framework (SCyWF) by NCA - outlines has 5 cybersecurity work categories (CARD, LWD, GRCL, PD & ICS/OT), 12 specialty areas and 40 job roles. SCyWF is outlined below:
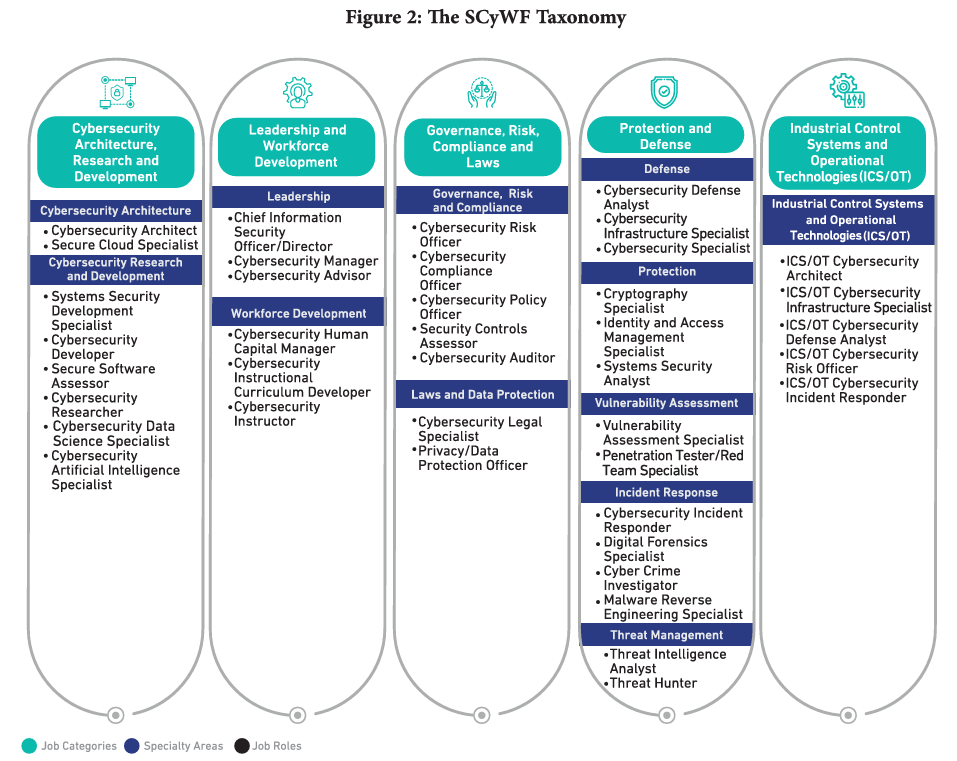
Source: NCA SCyWF
Operational Technology Cybersecurity Competency Framework (OTCCF) by CSA Singapore - provides the foundation to attract and develop talent for the emerging OT cybersecurity sector in Singapore.

Source: OTCCF by CSA Singapore
Enhanced Competency Framework on Cybersecurity (ECF-C) by Hong Kong Monetary Authority (HKMA) - competency standards for cybersecurity practitioners in the Hong Kong banking industry. Outlines basic and advance certifications/trainings for First line of defence (IT Security Operations and Delivery), second line of defence (IT Risk Management and Control) and third Line of defence (IT Audit).
And many more private guidance been published by different training providers and other institutions.
👉– Do some more research per your specific industry of interests - Google / Ask your fav AI agent, LLM or chatbot, - ChatGPT or others. You may want to start with looking at your local government backed skills/competence program as starting point of reference to build your career roadmap plan.
👉– Core elements of your 3-5 year career plan would include:
Career path - across single / multiple supplementary domains.
Certifications to target
Practical timelines - target dates for completion
Selection of Courses / Training providers
Costs and any other resources required to achieve your goals.
Note: In upcoming STA's cyber mentorship & Getting started in IT & OT Cybersecurity course offering - I'll deep dive across some of these frameworks.
👉– There are huge list of government and private sector guidance available - use it and build STBOK (securing things body of knowledge); yes an acronym I introduced in Step 1 of the blueprint.
👉– Decision Point: Now that you’ve build a solid foundation on the industry, terms/acronyms, basic concepts, processes, career tracks/options explored, this marks an end to Phase A of your journey. IT or OT - you’d like to be part of and hence what industry/entities, trainings/certs, and roles to target.
Once this is done, move to next Phase B - Implement & Execute Plan - Breaking into Cybersecurity.
📢 Watch out for explainer video on this step in near future. 📢 Make sure to subscribe and bookmark this. Will only be available for subscribers.
What other important aspects of this steps you’d recommend? comment below.
2. My Recent Most Viewed Posts:
In case you’ve missed - here are my recently most viewed social posts.
Getting started in IT & OT Cybersecurity - a blueprint / framework to 2x/5x/10x your cybersecurity career. Intro | Phase A, Step 1 and Step 2 and Step 3.
IT & IT Cybersecurity - Strategy, Program, Roadmap Execution & Management - an example recommended approach towards a growing challenge for CISOs, CIOs, CXOs of industrial organisations worldwide.
Chronicles of Cybersecurity Consulting - 1st in series - The Bleeding Password. A real-life story from an cybersecurity review exercise.
3. Securing Things Academy - Updates:
Securing Things Academy Promo released.
Landing web pages for few courses are partially completed and or getting updates including the course content. More on this later.
4. My Asks
👉 Do share, comment and add your experience and insights - as this may help someone bring some clarity and make right choices in their career decisions and or progression. Our world needs more cybersecurity professionals.
Securing Things Academy:
IT & OT CySEAT (Cyber Security Education And Transformation) course is designed for IT and OT cybersecurity practitioners. Join the wait-list → here.
Checkout a brief overview below:
Ways in which I can help?
Whenever you are ready - I can help you with:
A - IT & OT Cybersecurity Advisory / Consulting services - for securing your business and or its digital transformation journey.
B - Security Awareness Training & Phishing Awareness Portal - Train your staff and build a Security awareness program subscription based service.
C - Securing Things Academy (STA) - Security trainings for IT & OT practitioners.
Visit the newsletter website for Links to above services and or reach out at info[at]securingthings[dot]com or DM me via LinkedIn.
D - Securing Things Newsletter - Sponsor this newsletter to showcase your brand globally, or subscribe to simply Get Smarter at Securing Things.
Reach out at newsletter[at]securingthings[dot]com or DM me via LinkedIn.
How are we doing?
I invite you as part of #SecuringThings community to share your feedback.
Rate the newsletter content
Your feedback and input is invaluable to me as we work together to strengthen our cybersecurity defenses and create a safer and smarter digital society.
Let us know how we can improve this and or what you’d like to see in future?
Thank you for your trust and continued support.
Do register, validate your email, and request login link to submit poll to be able to enter a chance to win a future course giveaway.
Thanks for reading - until the next edition!
It’s a Great Day to Start Securing Things for a Smart & Safer Society.
Take care and Best Regards,
M. Yousuf Faisal. (Advice | Consult Cyber & business leaders in their journey on Securing Things (IT, OT/ICS, IIOT, digital transformation, Industry 4.0, & AI) & share everything I learn on this Newsletter | and upcoming Academy).
The Newsletter Platform Built for Growth
When starting a newsletter, there are plenty of choices. But there’s only one publishing tool built to help you grow your publications as quickly and sustainably as possible.
Beehiiv was founded by some of the earliest employees of the Morning Brew, and they know what it takes to grow a newsletter from zero to millions.
The all-in-one publishing suite comes with built-in growth tools, customization, and best-in-class analytics that actually move the needle - all in an easy-to-use interface.
Not to mention—responsive audience polls, a custom referral program, SEO-optimized webpage’s, and so much more.
If you’ve considered starting a newsletter, there’s no better place to get started and no better time than now.


