Disclaimer: All views presented here, in this newsletter, are my own.
Author or the newsletter are not liable for any actions taken by any individual or any organization / business / entity. The information provided is for education and awareness purposes only and is not specific to any business and or situation.
Table of Contents
Hi Securing Things Community,
Are you aware of the security concepts - around IT & OT processes, layers of Automation stack, Purdue Model & domain specific knowledge areas? Are you:
a recent graduate or learner
an automation / OT / ICS professional
an existing IT security professional
an experienced professional from a non-IT/Security/Automation field
And want to learn more about cybersecurity? If so;
In this newsletter edition, we’ll continue to expand on “Getting started in IT & OT Cybersecurity”, covering “Phase A and Step 3”. In addition, I’ll be sharing few interesting cybersecurity resources/links, my recent most viewed social media posts from June/May 2024 and updates on Securing Things Academy.
Special Message:
Before we begin, do me a favour and make sure you hit the “Subscribe” button to let me know that you care and keep me motivated to publish more. Thanks! Note: remember to validate your email address to ensure that you don’t miss any future newsletter editions.
1. Phase A - Initiate, Validate, Prepare & Plan
Phase A, as the name implies is all about initiating, validating, preparing and plan - doing the preliminary work check before you take a leap of faith on getting started in cybersecurity.
In this newsletter, let’s expand and talk about Step 3.
But in case, if you are seeing this for first time or you’ve missed the previous 3 posts for my 3 phase & 12 steps blueprint, here are the links below:
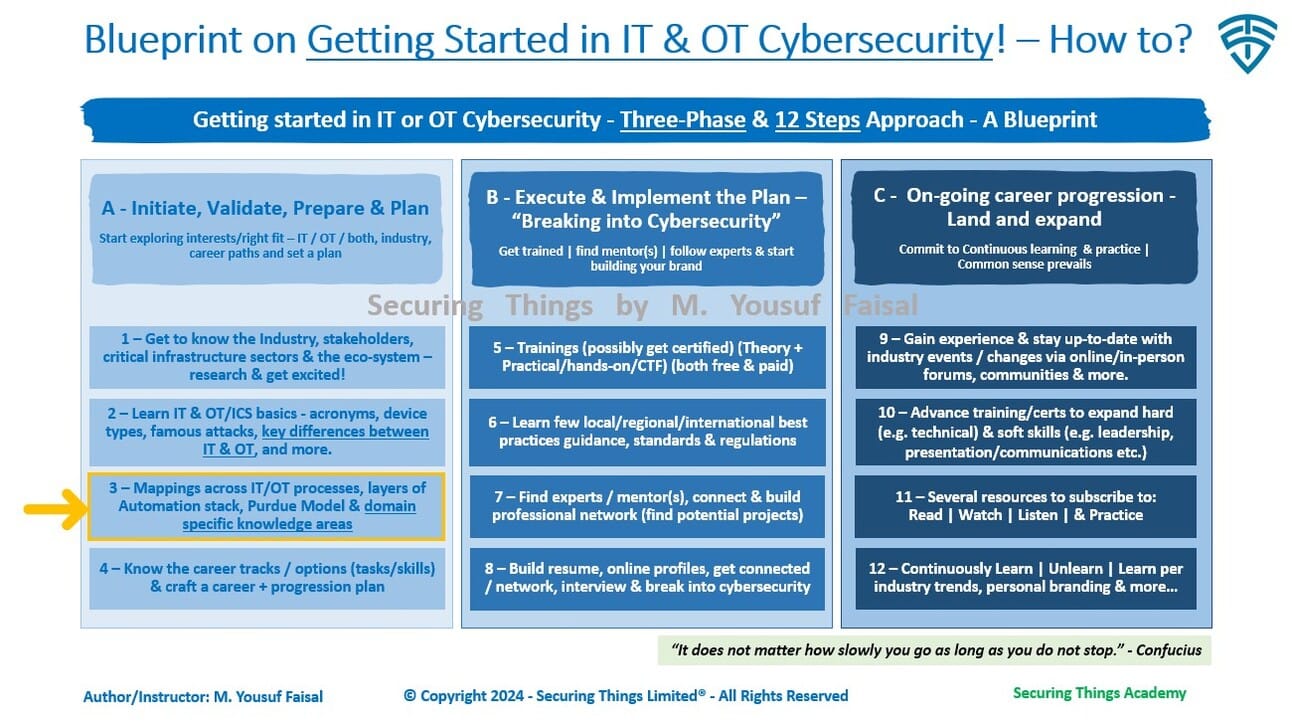
Step 3 - Getting started in IT & OT Cybersecurity - Blueprint by M. Yousuf Faisal
Step 3 – Mappings across IT/OT processes, layers of Automation stack, Purdue Model & domain specific knowledge areas.
So now that you’ve had some understanding of basic terms/acronyms, basic security concepts and priorities for IT and OT/ICS from step 1 and step 2. We are now going to dive a bit deeper in some popular concepts on IT and OT processes.
👉– For a recent graduate or learner and an experienced professional from a non-IT/Security/Automation field - we need to spend a little more time here, by getting familiar with some key IT & OT related security processes. Though most of such security processes are applicable to all industry, some approaches may differ for different industry. If you have a specific target industry in mind, start from there.
👉– For An automation professional, you should already have a good understanding and idea around major/critical OT related processes e.g. change management. However, if you are completely new to cybersecurity, follow the above as well.
👉– If you are an existing IT security professional - you should already have a good understanding and idea around all major IT cybersecurity processes. So you might want to focus on the differences in cybersecurity approach of the similar processes from OT perspective e.g., change / configuration management, vulnerability & patch management etc..
👉– For all personas types - the information that needs to be learned / gained may differ slightly according to industry, interests and IT or OT side of things. However, all above personas should learn about and be familiar with the following two concepts i.e., automation stack and PERA/Purdue Model widely used within the industry.
👉– From an industry perspective - one must keep up with industry updates as new advancements related to IT & OT processes, automation, and emerging technologies (e.g. AI usage) are introduced. Be ready to commit to lifelong learning.
👉– For purpose of this article, we’ll take an example of “Manufacturing Sector”:
For any given manufacturer, below outlines a typical manufacturing workflow lifecycle - simplified: (starting at CRM - customer relationship management and going through a continuous cycle). Explainer video coming soon.
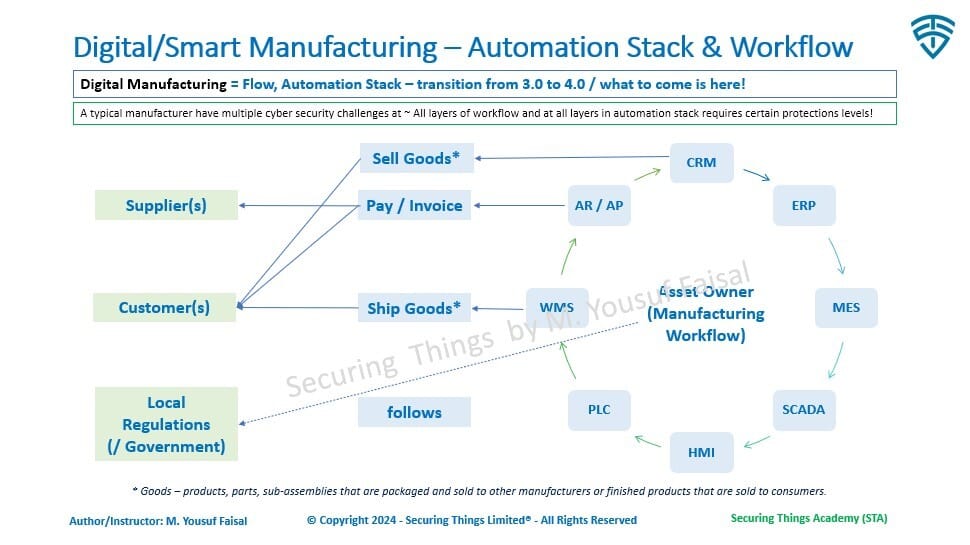
STA-IT-OT-Manufacturing-Workflow-by-M. Yousuf Faisal
and the 6 layers of automation stack (per ISA 95 standards) and the physical devices: (note: these are important as all the connectivity, and integration work for business automation (i.e., for an industry 4.0 organisation) occurs across these 6 blue layers, and hence, the importance of knowing cyber-physical risks that needs to be addressed. Explainer video coming soon.

STA-IT-OT-Cybersecurity-Focus-Automation-Stack-by-M. Yousuf Faisal
The more popular concepts within the manufacturing or critical infrastructure sector; i.e., PERA / (enhanced) Purdue Reference model - many a times referenced in network architecture discussions (though it was not originally intended to be used for network segregation). Below is just one of the many examples of this model. At this stage you just need to focus on the L0-L5 layers and description - not to worry about rest (more on the rest later) - Checkout details in one of my previous posts “Part 3” of OT Security Dozen series. Explainer video coming soon.
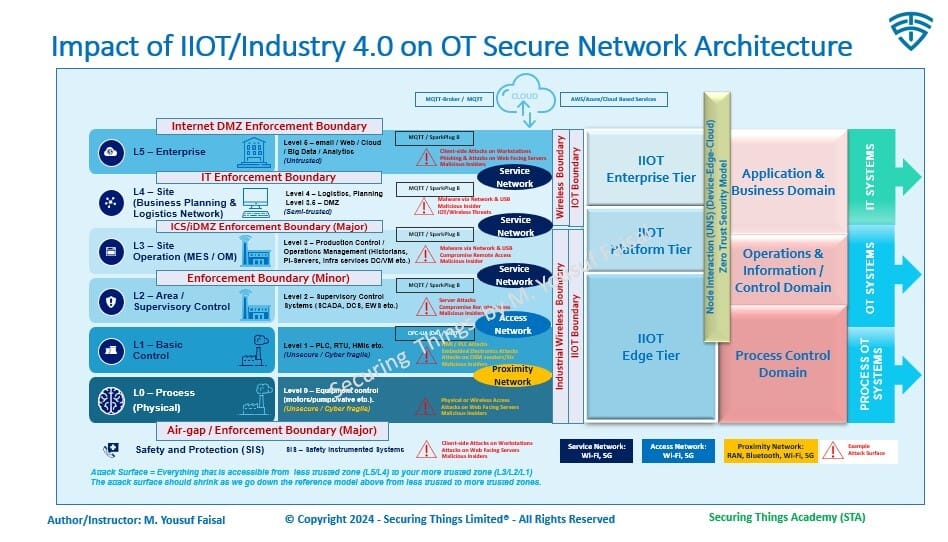
STA-IT-OT-Secure-Network-Architecture-by-M. Yousuf Faisal
Once you’ve understood the above the typical list of IT and OT Security processes and industry best practices are going to be per different industry guidance and sectors but some main commonalities are outlined here as some key example:
Asset / Inventory Management - all about inventorying your business (hardware, software, information etc.).
Change Management - all about ensuring tracking of control changes to your assets to ensure systems safety, reliability, availability, integrity, and confidentiality.
Configuration Management - all about ensuring assets are configured securely and optimally, to ensure systems safety, reliability, availability, integrity, and confidentiality.
Vulnerability & Patch Management - all about identifying, tracking, prioritizing, patching and remediation vulnerabilities.
Endpoint Security (anti-virus/malware, USB, whitelisting & others)
Backup and Disaster Recovery - all about ensuring that data that’s critical to business is backed up and is available in a disaster scenario.
Log management & SecOps (security operations) - all about ensuring that all key digital activities are recorded/logged and someone is monitoring and taking actions around any malicious activity.
Incident Response - all about ensuring that teams are prepared to respond to a cyber incident and ensure quick resumption to normal operations, tracking root cause and documenting lessons learned and ensuring measures are in place to avoid it in future (where possible).
Risk Management - all about identifying, documenting and assessing risks to business and figuring out treatment plans to reduce them to an acceptable business threshold.
Third-party Risk Management - ensuring that all service providers and or third-parties involved in your business cycles are monitored for risk to your business and have sufficient contract provisions and or control measures to minimise business impact.
Physical security and more..
👉– Do some more research per your specific industry of interests - Google / Ask your fav AI agent, LLM or chatbot, - ChatGPT or others.
Here’s an example list of critical infrastructure sectors classified by US:

US Critical Information Infrastructure (CII) Sectors
You may want to start with looking at your local government designation and or classification of critical sectors e.g. for Singapore its slightly different per the following:

Singapore CII Industry sectors classification
Note: In upcoming STA's cyber mentorship & Getting started in IT & OT Cybersecurity course offering - I'll deep dive across the basics on manufacturing workflow, layers of automation stack, Purdue Model, risks covering IT and OT side of the business.
👉– There are huge list of government and private sector guidance available - use it and build STBOK (securing things body of knowledge); yes an acronym I introduced in Step 1 of the blueprint.
👉– Remember, not to stress yourself out, this is still not a decision point yet, rather having a better understanding for later part in crafting your journey to know which side - IT or OT - you’d like to be part of and hence what industry/entities, trainings/certs, and roles to target.
Once this is done, move to next steps. You shouldn’t be spending too much time on this, but at the same time you shouldn’t be skipping this step. As eventually you’ll have to explore and understand these.
📢 Watch out for explainer video on this steps in near future posts/videos. 📢 Make sure to subscribe and bookmark this. Will only be available for subscribers.
What other important aspects of this steps you’d recommend? comment below.
2. Cybersecurity & AI Reads & News
Following is a list of few interesting reads and news:
CIS 8 mappings to NIST CSF v2 - Center of Information Security, recently released a document with mappings of CIS Critical Security Controls (CSC) v8 and CIS Safeguards against NIST Cybersecurity framework 2.0. A handy resource for cyber professionals in GRC space.
Detecting OT Cybersecurity Threats Using the Known-Unknown Matrix - A useful tool for understanding and knowing how to detect cybersecurity threats, including OT cybersecurity threats, is the Known-Unknown Matrix, by Nozomi Networks.
ISACA’s Digital Trust Ecosystem Framework (DTEF) - Focusing on the key components of building trustworthy relationships between enterprises and consumers, the Framework addresses three traditional elements (people, process, and technology), and adds a fourth critical element (organization).
VMware Abused in Recent MITRE Hack for Persistence, Evasion - MITRE has shared information on how hackers abused VMware for persistence and detection evasion in the recent hack.
Learning Microsoft Co-pilot for Security - Learn about Microsoft Co-pilot for Security, an AI-powered, cloud-based security analysis tool that enables security analyst and IT admins to process security signals and protect at the speed and scale of AI.
3. My Recent Most Viewed Posts:
In case you’ve missed - here are my recently most viewed social posts.
IT & IT Cybersecurity - Strategy, Program, Roadmap Execution & Management - an example recommended approach towards a growing challenge for CXOs of industrial organisations worldwide.
Getting started in IT & OT Cybersecurity - a blueprint / framework to 2x/5x/10x your cybersecurity career. Intro | Phase A, Step 1 and Step 2.
Chronicles of Cybersecurity Consulting - 1st in series - The Bleeding Password. A real-life story from an cybersecurity review exercise.
👉 Do share, comment and add your experience and insights - as this may help someone bring some clarity and make right choices in their career decisions and or progression. Our world needs more cybersecurity professionals.
👉 I hope to make a difference & help at-least 100/> people in 2024 (ideally 1K/>) (am not making a bold claim of million or something) to give back to the community.
4. Securing Things Academy - Updates:
Securing Things Academy Promo released or download below.
and previous newsletter posts, revealed plans for the following course ideas:

Initial Plan for STA
5. My Asks
Do provide your valuable input to help me decide on few things on Securing Things Academy (STA) promo link/pdf download above:
Are the courses / topics ideas mentioned above resonates with you?
Your preference? (or if you an expert, do they align with market needs)?
Any course / certification name suggestions suggestion, per above list?
Or rather prefer Mini courses on similar topics?
Securing Things Academy:
IT & OT CySEAT (Cyber Security Education And Transformation) course is designed for IT and OT cybersecurity practitioners. Join the wait-list → here.
Checkout a brief overview below:
Ways in which I can help?
Whenever you are ready - I can help you with:
A - IT & OT Cybersecurity Advisory / Consulting services - for securing your business and or its digital transformation journey.
B - Security Awareness Training & Phishing Awareness Portal - Train your staff and build a Security awareness program subscription based service.
C - Securing Things Academy (STA) - Security trainings for IT & OT practitioners.
Visit the newsletter website for Links to above services and or reach out at info[at]securingthings[dot]com or DM me via LinkedIn.
D - Securing Things Newsletter - Sponsor this newsletter to showcase your brand globally, or subscribe to simply Get Smarter at Securing Things.
Reach out at newsletter[at]securingthings[dot]com or DM me via LinkedIn.
How are we doing?
I invite you as part of #SecuringThings community to share your feedback.
Rate the newsletter content
Your feedback and input is invaluable to me as we work together to strengthen our cybersecurity defenses and create a safer and smarter digital society.
Let us know how we can improve this and or what you’d like to see in future?
Thank you for your trust and continued support.
Do register, validate your email, and request login link to submit poll to be able to enter a chance to win a future course giveaway.
Thanks for reading - until the next edition!
It’s a Great Day to Start Securing Things for a Smart & Safer Society.
Take care and Best Regards,
M. Yousuf Faisal. (Advice | Consult Cyber & business leaders in their journey on Securing Things (IT, OT/ICS, IIOT, digital transformation, Industry 4.0, & AI) & share everything I learn on this Newsletter | and upcoming Academy).
The Newsletter Platform Built for Growth
When starting a newsletter, there are plenty of choices. But there’s only one publishing tool built to help you grow your publications as quickly and sustainably as possible.
Beehiiv was founded by some of the earliest employees of the Morning Brew, and they know what it takes to grow a newsletter from zero to millions.
The all-in-one publishing suite comes with built-in growth tools, customization, and best-in-class analytics that actually move the needle - all in an easy-to-use interface.
Not to mention—responsive audience polls, a custom referral program, SEO-optimized webpage’s, and so much more.
If you’ve considered starting a newsletter, there’s no better place to get started and no better time than now.



