Disclaimer: All views presented here, in this newsletter, are my own.
Author or the newsletter are not liable for any actions taken by any individual or any organization / business / entity. The information provided is for education and awareness purposes only and is not specific to any business and or situation.
Hey there,
Hope you are doing well.
This is Part 2 of special a multi-part series titled:
🔐OT Cybersecurity Procurement Process & Practices (OTCS PPP) - ultimate guide📘- for procuring / buying industrial solutions / services to protect our industrial operations and or critical infrastructure.
🚨 For IT-OT Tech, Cybersecurity & Industrial Procurement Professionals! 🚨
🔥 What you’ll learn in this series:
📘Part 1 - Foundations & best practices for OT cybersecurity procurement (already published, click Part 1 in case you missed it).
📘Part 2 - Tailored strategies for the Water & Wastewater Utility sector (we cover Alana' Murrays 7 step framework. She share✍️her expert insights, drawing from years of hands-on experience from water / wastewater utility sector).
In the upcoming newsletter’s we’ll cover the following.
Part 3 - Procurement insights for the Manufacturing industry
Part 4 - Industry 4.0 supply chain security dos & don’ts every buyer must know
What would you like us to add more? Let us know in the comments below.
In this edition, we’ll also cover,
related📘industry best practice references, risk assessment tools, and guidance 📘for Water Wastewater utility sector and
updates on next part 3 and upcoming webinar where I’ll be joining as one of the panel participant among seasoned leaders and newsletter.
If you find Alana's 7-step framework helpful, we'd love to hear from you! Please let us know by filling out the poll at the end of this edition and feel free to share your thoughts through comments, likes, or reshares.
♻️if you know someone in your professional circle who will benefit from this guidance and or are interested in learning. Thanks 🌟
So let’s dig in.
Yours truly.
— Yousuf.
Call out for expert insights:
Also, if you are an expert in Power, Transportation (Airport and Railway) and Oil & Gas sectors📜and want to contribute to this series ✍
DM 📥 / drop a comment 👇 for guest posts and get a shout out! 📢
I see many of you visit the newsletter site, consume the content, however, a low percentage of you actually registers.
So before we begin, do me a favour and make sure you hit the “Subscribe” button to let me know that you care or liked what you’ve read and keep me motivated to publish more. Thanks!
Together with:
Optimize global IT operations with our World at Work Guide
Explore this ready-to-go guide to support your IT operations in 130+ countries. Discover how:
Standardizing global IT operations enhances efficiency and reduces overhead
Ensuring compliance with local IT legislation to safeguard your operations
Integrating Deel IT with EOR, global payroll, and contractor management optimizes your tech stack
Leverage Deel IT to manage your global operations with ease.
7 Critical Steps for Bullet-proofing Your OT Cybersecurity Procurement Process in Water & Wastewater Utilities📜
By Alana Murray is an industrial controls expert with 35+ years of experience in critical infrastructure sectors, including water/wastewater utilities. She writes on operational technology security and just about everything else in the industrial control system industry.
Here are 7 critical steps for bullet proofing OT cybersecurity Procurement processes:
Clearly define Cybersecurity Requirements from day one.
Incorporate Security Clauses in Contracts, that have real teeth.
Focus on Lifecycle Security, not just installation.
Secure the Supply Chain like water quality depends on it (because it does).
Implement comprehensive vendor assessment tailored to water operations.
Foster Genuine cross-functional collaboration (not just meeting invites).
Apply a Risk-Based Approach grounded in water system realities.
Plus,
Real-World Implementation: Putting These Steps into Action
Next Steps: Building Your OT Security Procurement Process.
7 Critical Steps for Bullet-proofing Your OT Cybersecurity Procurement Process in Water & Wastewater Utilities by Alana Murray - Original post → here.
To continue reading → Register below to read for free, where Alana breaks down each of these 7 steps in detail, with industry specific examples/references.
The 7 Critical Steps framework - The Breakdown📜
By Alana Murray - an industrial controls expert with 35+ years of experience in critical infrastructure sectors, including water/wastewater utilities. She writes on operational technology security and just about everything else in the industrial control system industry.
1. Clearly Define Cybersecurity Requirements from Day One
The days of purchasing PLCs (Programmable Logic Controllers), RTUs (Remote Terminal Units), HMIs (Human Machine Interfaces), and SCADA (Supervisory Control and Data Acquisition) systems based solely on functionality and price are long gone.
But I still see too many RFPs (Requests for Proposal) with vague language like "must include security features" without specifying what those features should be.
Water-specific approach: For water utilities, your cybersecurity requirements should directly reference key frameworks and regulations:
The EPA's (Environmental Protection Agency) Cybersecurity Memorandum now requires states to evaluate OT/ICS (Industrial Control Systems) security during sanitary surveys, which means your procured systems need to satisfy these inspections.
Draw from the American Water Works Association (AWWA) Cybersecurity Risk Management Guidance.
Specify conformance to IEC 62443 standards (international standards for industrial automation and control systems security) when procuring control system components.
A practical example: Instead of writing "remote access must be secure," specify: "Remote access solutions must support multi-factor authentication (requiring at least two forms of verification, such as a password plus a temporary code), encrypted connections, time-limited sessions, and detailed session logging.
Watch out for: Don't rely on the default security configurations of any industrial control system. I've seen newly installed water treatment SCADA systems with default passwords, open ports, and unnecessary services running, all because specific security hardening wasn't included in the requirements phase.
2. Incorporate Security Clauses in Contracts That Have Real Teeth
Contracts are your most powerful procurement tool, yet I regularly review water utility contracts with no substantive security language at all or vague wording that is essentially unenforceable.
Water-specific clauses to include:
Vulnerability disclosure: Require vendors to notify you of any security weaknesses or flaws affecting your systems within a specific timeframe (I recommend 15 days of discovery).
Patch management: Establish SLAs (Service Level Agreements—contractual commitments specifying timeframes and quality standards) for security updates to critical control systems, particularly for internet-connected components. For instance, "The vendor must provide security patches for critical vulnerabilities within 30 days of their discovery."
Access management: Define contractor remote access protocols, including how vendor credentials are issued, tracked, and revoked.
Indemnification: Include language holding vendors accountable for security incidents resulting from their negligence.
Learn from this mistake: A mid-sized water treatment plant I consulted had a major SCADA component breached through the vendor's remote access tool.
The contract had no security provisions, leaving the utility solely responsible for the remediation costs and regulatory fallout.
Their next contract included detailed security requirements, 24-hour breach notification, and shared remediation responsibilities.
3. Focus on Lifecycle Security, Not Just Installation
Water systems are built to last decades, but control system technology becomes obsolete much faster, creating a dangerous security gap.
Water-specific approach:
End-of-life planning: The EPA now expects utilities to account for cybersecurity across the entire system lifecycle. During procurement, ask vendors to provide their product support timelines and security patch commitments.
Documentation requirements: Specify that vendors must deliver comprehensive documentation, including network diagrams, security configurations, and hardening guides.
Ongoing assessments: Require periodic security assessments as part of maintenance contracts.
Real-world implementation: The City of Fresno Water Division provides an excellent case study here. They prioritized lifecycle security by deliberately planning SCADA upgrades before their existing system reached end-of-support, avoiding the vulnerability gap that occurs when running unsupported software that cannot receive security patches.
4. Secure the Supply Chain Like Your Water Quality Depends on It (Because It Does)
In water treatment, we rigorously evaluate chemical supplies for quality and purity. We need to apply that same diligence to our digital supply chain.
Water-specific approach:
Component verification: For critical operational technology like PLCs that control chemical dosing or filtration, require verification of firmware integrity and documentation of the hardware supply chain.
Software transparency: Request SBOMs (Software Bills of Materials, inventories that list all components and libraries in a software product) for SCADA systems and control software to quickly identify vulnerability exposure when new threats emerge.
Risk assessment: Evaluate not just your immediate vendors but also their suppliers, especially for critical control components.
A growing risk to watch: Many water utilities use specialized analytical instruments and sensors that communicate directly with control systems.
These devices are increasingly connected but often overlooked in security assessments.
Make sure your procurement process includes specific security requirements for these components, especially sensors that influence automated treatment decisions.
5. Implement Comprehensive Vendor Assessment Tailored to Water Operations
Generic vendor security questionnaires aren't enough for water system integrity.
Water-specific approach:
Certifications that matter: Look for vendors with IEC 62443 certifications, which validate their industrial control system security capabilities.
Water sector experience: Assess vendors' experience with water-specific regulations and standards like AWWA cybersecurity guidance.
Penetration testing records: Request evidence that their products have undergone water-specific scenario testing (e.g., chemical control system manipulation).
What works in practice: Some forward-thinking water utilities have developed scoring systems for OT vendors, with extra points awarded for those who can demonstrate compliance with AWWA cybersecurity controls and has experience handling security incidents in water environments, specifically.
Watch out for: I frequently see procurement teams accept generic SOC 2 reports (Service Organization Control reports, audit documents that assess a service provider's security controls) as sufficient evidence of security capability.
While valuable, these rarely cover industrial control system security. Request evidence specific to OT environments.
6. Foster Genuine Cross-Functional Collaboration (Not Just Meeting Invites)
Water utilities present unique collaboration challenges, with operations staff often working in distributed facilities and IT and security teams potentially centralized.
Water-specific approach:
Establish an ICS Cybersecurity Governance Committee that includes representatives from:
Operations (plant managers, SCADA technicians)
Engineering (process engineers, control system specialists)
IT / Security (CISO, systems / network administrators)
Executive leadership (Chief Technology Officer / operations director)
Safety / compliance personnel.
Collaborative risk assessment: Before any major OT procurement, conduct joint operational and cybersecurity risk assessments that consider both process safety and digital security.
Real success story: One mid-sized wastewater utility I worked with established a monthly "Security Operations Sync" where SCADA technicians, IT staff, and security personnel reviewed upcoming projects and system changes.
This simple practice transformed their procurement process.
When a new project for automating the pump station came up, the cross-functional team had already established common language and trust, making it easy to develop comprehensive security requirements that everyone understood and supported.
7. Apply a Risk-Based Approach Grounded in Water System Realities
Not all assets in water systems carry equal risk. A control system for chemical dosing presents different risks than a billing system or a simple level monitor.
Water-specific approach:
Process impact analysis: Evaluate control system components based on their direct impact on water quality and service continuity.
Regulatory risk: Prioritize security for systems that, if compromised, could lead to EPA violations or public health alerts.
Defense-in-depth strategy: Apply more stringent procurement requirements to critical systems like chemical control while maintaining baseline security for all OT assets. Defense-in-depth means implementing multiple layers of security controls throughout your system, rather than relying on a single protective measure.
A practical framework: Several water utilities have adapted the AWWA Cybersecurity Risk Assessment tool to create a "security tier" system for procurement. For example:
Tier 1 (highest security): Chemical dosing systems, filtration controls, SCADA master stations.
Tier 2: Pump controls, pressure monitoring, remote site RTUs.
Tier 3: Energy management systems, historical data collectors.
Each tier has a corresponding set of procurement requirements, with the most stringent controls reserved for Tier 1 systems.
Written by Alana Murray is an industrial controls expert with 35+ years of experience in critical infrastructure sectors, including water/wastewater utilities. She writes on operational technology security and just about everything else in the industrial control system industry.
Real-World Implementation: Putting These Steps into Action
Let me share how one water utility successfully applied these principles. A large municipal water utility with over 500,000 customers undertook a major SCADA upgrade project with security as a primary consideration.
Their approach included:
Comprehensive requirements: They developed detailed security specifications based on the NIST (National Institute of Standards and Technology) Cybersecurity Framework and AWWA guidance, embedding these directly in their RFP.
Contract protections: Their vendor contract included vulnerability disclosure requirements, patch management SLAs, and security testing provisions.
Collaboration: An integrated team of OT engineers, IT security professionals, and compliance staff jointly evaluated vendor proposals.
Verification: They conducted factory acceptance testing with specific security scenarios (like attempted unauthorized access).
Post-implementation: Regular security assessments were built into the maintenance agreement.
The project not only produced a more functional SCADA system, but it also successfully passed a subsequent EPA inspection and demonstrated resilience against attempted intrusions.
Next Steps: Building Your OT Security Procurement Process
If you're wondering where to start, I recommend:
Assess your current state: Utilize the EPA's Cybersecurity Checklist or AWWA's Cybersecurity Assessment Tool to identify gaps.
Develop templates: Create standardized security requirements templates for distinct types of OT procurements (e.g., PLCs, network equipment, SCADA software).
Train your team: Ensure procurement staff understand basic OT security concepts and why these requirements matter.
Start small if needed: Begin with one critical project to implement these principles, then expand based on lessons learned.
Remember, securing water systems is a continuous journey, not a one-time project. Every procurement decision either strengthens or weakens your security posture for years to come. In my over three decades of industrial controls experience, I have never seen a security retrofit that was cheaper or more effective than building security in from the start.
Written by Alana Murray is an industrial controls expert with 35+ years of experience in critical infrastructure sectors, including water/wastewater utilities. She writes on operational technology security and just about everything else in the industrial control system industry.
Related Resources
I figured it might be helpful to save you some research time by sharing a few industry references that Alana mentioned in her 7-step framework above, along with some other handy resources, industry guidance and references. So, checkout the resources below that you may find useful (especially if you are working in and or supporting water/wastewater utility organizations):
EPA's (Environmental Protection Agency) Cybersecurity for the Water Sector.
Guidance for Evaluating Cybersecurity During Public Water System Sanitary Surveys. This guidance supports implementation of the U.S. Environmental Protection Agency (EPA) memorandum (memo), Addressing PWS Cybersecurity in Sanitary Surveys or an Alternate Process.
American Water Works Association (AWWA) - Cybersecurity & Guidance and related technical resources.
American Water Works Association (AWWA) - Water Sector Cybersecurity Risk Management Tool. designed to support systems in developing their cybersecurity risk management strategy while also facilitating compliance with the cybersecurity provisions in §2013 of America's Water Infrastructure Act (AWIA) of 2018. The risk and resilience assessment must consider malevolent and natural hazards that may impact critical assets, including the following that may be vulnerable to cyber threats:
electronic, computer, or other automated systems;
the monitoring practices of the system; and,
the financial infrastructure of the system.
American Water Works Association (AWWA) - Process Control System Security Guidance for the Water Sector
Utility Risk & Resilience Certificate Program - eLearning program with free/paid courses by AWWA. This certificate program will provide a foundation for supporting a water utility’s development of an all-hazards approach to risk and resilience management. Facilitates compliance with America’s Water Infrastructure Act of 2018 (EL260).
Quick Start Guide: An Overview of ISASecure Certification - A certification scheme based on ISA/IEC 62443 Security for Industrial Automation and Control Systems - ISA/IEC 62443 Conformance Certifications ISA/IEC 62443-4-1, ISA/IEC 62443-4-2 and ISA/IEC 62443-3-3 - Specify conformance to IEC 62443 standards (international standards for industrial automation and control systems security) when procuring control system components.
Water ISAC, the international security network created by and for the water & wastewater sector. Alerts, Reports, Best Practices and more.
12 Cybersecurity Fundamentals for Water and Wastewater Utilities. Recommended Practices to Reduce Exploitable Weaknesses and Consequences of Attacks. A very useful guide to read.
The Water Research Foundation - Guidelines and Forms.
Report CRITICAL INFRASTRUCTURE PROTECTION EPA - Urgently Needs a Strategy to Address Cybersecurity Risks to Water and Wastewater Systems - by GAO.
Cybersecurity Risk & Responsibility in the Water Sector - Prepared by Judith H. Germano.
Next on the OTCS PPP series - Part 3 📜
In part 3 of the "OT Cybersecurity Procurement Process & Practices" Part 3 - Procurement insights for the Manufacturing industry - I’ll be covering the topic based on my observations from the field (having worked for several different manufacturing organizations across different regions globally), to:
💡Understand traditional / legacy challenges and observation for the sector.
💡Identify current state of OT procurement process and practices, set target goals to mature these processes.
💡mature OTCS PPP, including addressing the pre-requisites and related supply chain elements.
Anyone in Cybersecurity involved in deal with establishing these processes and practices - this is going to be an exciting MUST READ!.
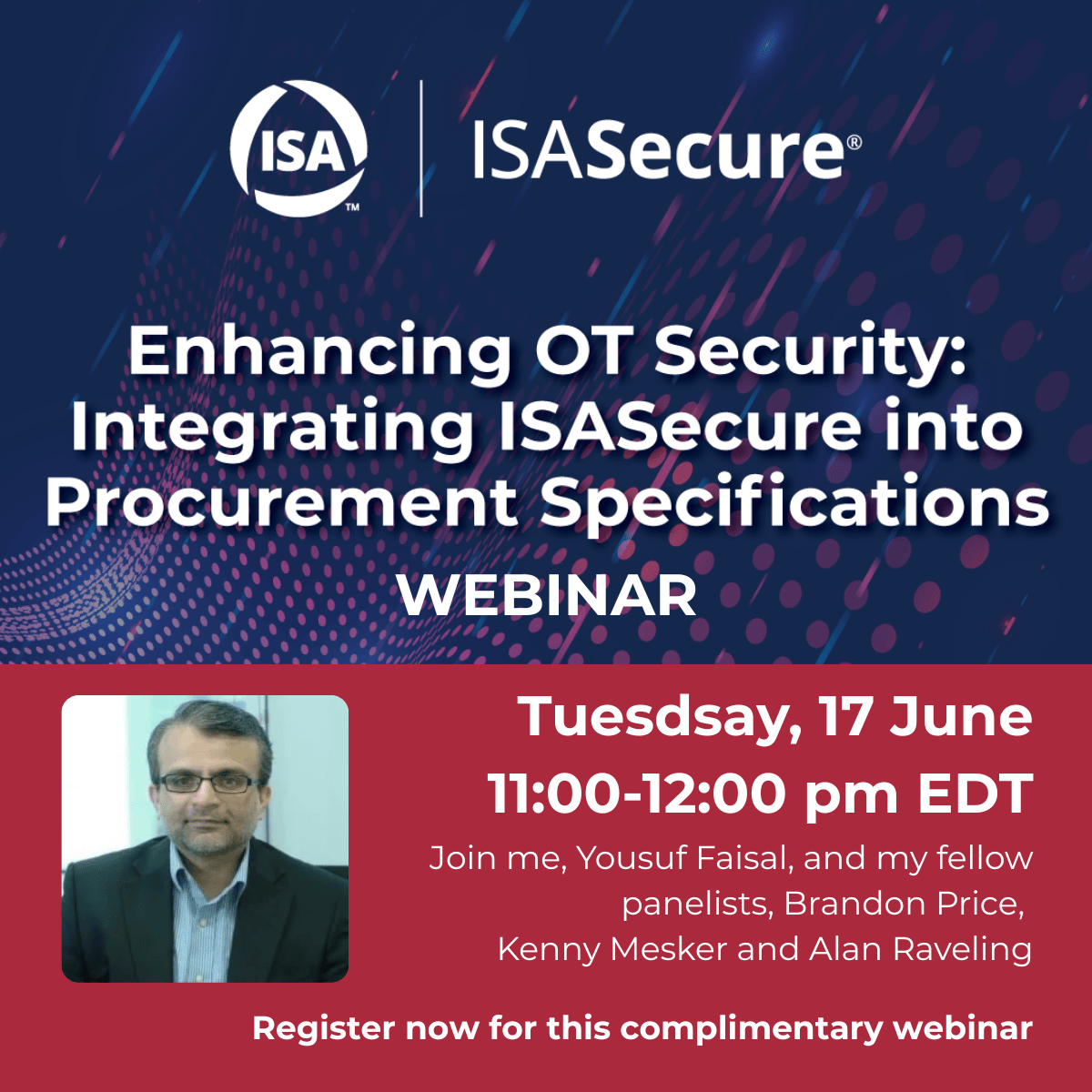
Upcoming webinar by ISA Secure
Join me on this complimentary Webinar hosted by ISA Secure.
I’ll be joining the above exclusive complimentary panel discussion featuring industry leaders from ExxonMobil, Chevron, Interstates, & Securing Things as we share industry insights on industry challenges and different strategies for operationalizing conformance to ISA/IEC 62443 standards through ISASecure certifications and smart procurement strategies.
My Recent Most Viewed Social Posts:
In case you’ve missed - here are some of my recent most viewed social posts.
📰[ST # 68] 🗞️ OT Cybersecurity Procurement Process & Practices (OTCS PPP) an ultimate guide - Part 1 ✅The foundations & international best practices for OT cybersecurity procurement with Alana Murray, reference resources and more ✍️ [Securing Things by M. Yousuf Faisal]
📰[ST # 67] The Real Security Risks - Divide between Cyber & Physical ✅Guest Post by Jamie Williams on Modern Cyber-Physical Threats and What Does Good Security Look Like Today? plus my views on the same ✍️ [Securing Things by M. Yousuf Faisal]
📰ISA/IEC 62443 Standards - Part 6 ✅62443-2-2:2025 IACS Security Protection Scheme, ISASecure Certification Standards, upcoming sessions & newsletters✍️ [Securing Things by M. Yousuf Faisal]
📰[ST # 65] Cybersecurity and AI Across IT-OT Automation Stack - Monthly Digest # 2 ✅ Competence Framework for Solutions Architects and Security Architects on industry 4.0, cybersecurity and AI across the automation stack (Cloud, ERP, DMZ, MES, SCADA, HMI, PLC/Edge), physical devices & more.🚀 [Securing Things by M. Yousuf Faisal]
📰[ST#64] IT & OT Cybersecurity Requirements Specifications - Do’s & Don’ts ✅ Deadly Sins (Common Mistakes) & Quick Wins (recommended fixes) for Cybersecurity requirements specification for Industrial environments 🚨- You Can’t Afford to Ignore! Plus🚨Announcement on OT Cybersecurity Procurement Process & Practices Series - an ultimate guide for IT-OT Tech, Cybersecurity & Procurement Professionals. [Securing Things by M. Yousuf Faisal]
📰[ST # 63] IT & OT Network Security - Example Do's & Don'ts ✅ Deadly Sins (Common Mistakes) & Quick Wins (recommended fixes) for Industrial / Manufacturing environments. Plus CISO's query and my response on Managed vs. Unmanaged switches for production environment🚀 [Securing Things by M. Yousuf Faisal]
📰[ST # 61] ✅My list of IT-OT & Cybersecurity, Leadership, Productivity, Personal Development, and Money/Business books - must read for Cyber Leaders and Practitioners. Few updates on OT Security conference, & more.🚀 [Securing Things by M. Yousuf Faisal] 📰
📢 [ST #60] All Series Index - Securing Things 📢✅IT, OT & AI Cybersecurity – Program, Digital Factory, Guides, Standards, Crash Courses, Quarterly Insights & more.🚀 [Securing Things by M. Yousuf Faisal] 🗞️🗞️🗞️
Ways in which I can help?
Whenever you are ready - I can help you with:
A - IT & OT Cybersecurity Advisory / Consulting services - for securing your business and or its digital transformation journey.
B - Security Awareness Training & Phishing Awareness Portal - Train your staff and build a Security awareness program through our subscription based service.
C - Securing Things Academy (STA) - Security trainings for IT & OT practitioners.
Visit the newsletter website for Links to above services and or reach out at info[at]securingthings[dot]com or DM me via LinkedIn.
D - Securing Things Newsletter - Sponsor this newsletter to showcase your brand globally, or subscribe to simply Get Smarter at Securing Things.
Reach out at newsletter[at]securingthings[dot]com or DM me via LinkedIn.
How are we doing?
I invite you as part of #SecuringThings community to share your feedback.
Rate the newsletter content
Your feedback and input is invaluable to me as we work together to strengthen our cybersecurity defenses and create a safer and smarter digital society.
Let us know how we can improve this and or what you’d like to see in future?
Thank you for your trust and continued support.
Do register, validate your email, and request login link to submit poll to be able to enter a chance to win a future course giveaway.
Thanks for reading - until the next edition!
It’s a Great Day to Start Securing Things for a Smart & Safer Society.
Take care and Best Regards,
M. Yousuf Faisal (Advice | Consult Cyber & business leaders in their journey on Securing Things (IT, OT/ICS, IIOT, digital transformation, Industry 4.0, & AI) & share everything I learn on this Newsletter | and upcoming Academy).