Disclaimer: All views presented here, in this newsletter, are my own.
Author or the newsletter are not liable for any actions taken by any individual or any organization / business / entity. The information provided is for education and awareness purposes only and is not specific to any business and or situation.
Hey there,
Hope you are doing well.
Ready to master "OT Cybersecurity Procurement Process & Practices" and safeguard your industrial environment and critical infrastructure in the era of Industry 3.0 and Industry 4.0?
🚨 Attention: IT-OT Tech, Cybersecurity & Industrial Procurement Professionals! 🚨
🔐 Introducing an exclusive Multi-Part Series on " OT Cybersecurity Procurement Process & Practices (OTCS PPP) - ultimate guide"- for procuring industrial solutions / services that protect industrial operations across water/wastewater utilities, manufacturing plants, and beyond.
Whether you’re a cybersecurity expert or a procurement pro in industrial sectors, this series will equip you with knowledge to make smarter & safer buying decisions.
🚨Anyone in Cybersecurity involved with establishing these processes and practices - this is going to be an exciting MUST READ!🔐
💡 Don’t miss out on securing your OT environment against rising cyber threats - this is part 1 of a special multi-part series on OTCS PPP.
🔥 I am excited and glad to be partnering on this series with an expert from the field "Alana Murray", bringing decades of industry experience and focused guidance for Water & Wastewater Utilities sector, alongside my limited experience from manufacturing and other critical infrastructure sector.
Welcome Alana Murray to Securing Things community.
For sector-specific expertise, I reached out to Alana, who shares valuable insights on LinkedIn. She agreed to discuss effective OT Cybersecurity procurement strategies for the water and wastewater sector in Part 2 of this series with an intro in Part 1.
So let’s dig in.
Yours truly.
— Yousuf.
PS: Please submit the poll at the end or write to newsletter[at]securingthings[.]com and let us know your feedback (anything from what you like, if its helpful in your work, anything you don’t like, to what topic you’d be interested to read in future).
But before we begin, do me a favour and make sure you hit the “Subscribe” button to let me know that you care or liked and keep me motivated to publish more. Thanks!
Together with:
Start learning AI in 2025
Keeping up with AI is hard – we get it!
That’s why over 1M professionals read Superhuman AI to stay ahead.
Get daily AI news, tools, and tutorials
Learn new AI skills you can use at work in 3 mins a day
Become 10X more productive
OTCS PPP - an introduction📜
By Written By M. Yousuf Faisal (Advice | Consult Cyber & business leaders in their journey on Securing Things (IT, OT/ICS, IIOT, digital transformation, Industry 4.0, & AI) & share everything I learn on this Newsletter | and upcoming Academy).
🔥 What you’ll learn in this series:
Part 1 - Foundations & best practices for OT cybersecurity procurement
Part 2 - Tailored strategies for the Water & Wastewater Utility sector
Part 3 - Procurement insights for the Manufacturing industry
Part 4 - Industry 4.0 supply chain security dos & don’ts every buyer must know
What would you like us to add more to it? Let us know in the comments below.
As industrial environments become increasingly digitized and interconnected, the stakes for securing these industrial / critical systems have never been higher.
By following this series, readers will gain a strategic framework to select resilient, secure OT products that protect their infrastructure today and adapt to evolving threats tomorrow.
This series is tailored specifically for OT owners and operators, procurement managers, cybersecurity officers, and technical decision-makers across sectors such as energy, manufacturing, water and wastewater utilities, transportation, and critical infrastructure.
OTCS PPP series is designed to empower procurement professionals, OT security leaders, and executives responsible for safeguarding industrial control systems with the knowledge and best practices to embed cybersecurity into every stage of the OT procurement process.
Whether you are a CISO overseeing enterprise-wide security or a plant manager responsible for day-to-day OT operations, this guide will provide actionable insights to navigate the complex intersection of cybersecurity and procurement in OT environments.
By the end of this three-part series, you will be equipped to transform your OT procurement practices from reactive and fragmented to proactive and security-driven.
You will understand foundational concepts, international standards, and sector-specific challenges and frameworks to address those challenges with suggested approaches, enabling you to build a robust cybersecurity posture that minimizes risk, ensures compliance, and supports operational continuity.
Call out for expert insights:
Also, if you are an expert in Power, Transportation (Airport and Railway) and Oil & Gas sectors and want to contribute to this series ✍ me a DM 📥 / drop a comment 👇 for guest posts and a shout out! 📢
♻️if you know someone in your professional circle who will benefit from this guidance and or are interested in learning. Thanks 🌟
Written By M. Yousuf Faisal (Advice | Consult Cyber & business leaders in their journey on Securing Things (IT, OT/ICS, IIOT, digital transformation, Industry 4.0, & AI) & share everything I learn on this Newsletter | and upcoming Academy).
The Fundamentals📜
OT systems procurement differ from traditional IT system procurement due to their long lifecycles, safety-critical functions, complexity and need for continuous availability.
Many OT products historically lack built-in security features, making them vulnerable to threats such as weak authentication, insecure default settings, limited logging, and legacy protocols.
Cyber adversaries exploit these weaknesses to disrupt physical processes, as seen in ransomware attacks targeting pipelines and utilities.
On the other hand, there’s vendor lock-ins, and many emerging OT products coming out in the market with built in security features now (both certified and non-certified). This presents varying level of risks for asset owners and their operations.
To address these challenges, procurement processes must prioritize "secure by 3Ds" principles (see below), ensuring security is integrated from the earliest stages of product selection and acquisition to implementation.
This includes demanding products that support open architecture (avoiding vendor lock-ins), secure configuration management, comprehensive logging, strong authentication, and secure communication protocols.
In an earlier edition, Secure by 3Ds (Demand | Design | Default), outlines essential concepts on OTCS PPP where I covered ✅ The trifecta reshaping IT & OT cybersecurity industry! Discover what these mean, why they matter, and how they protect critical infrastructure.

Secure by The 3D Trifecta by M. Yousuf Faisal
International Best Practices / Standards
You’ll find fragmented industry guidance or international best practices around OTCS PPP and or some guidance which is out-dated.
This drove the need for the International cybersecurity agencies, including the US Cybersecurity and Infrastructure Security Agency (CISA), European Commission, and national cybersecurity centres from Australia, Canada, Germany, the Netherlands, New Zealand, and the UK, have collaborated to define 12 essential security elements for OT procurement.
And other similar international best practice guidance (see related resources below).
These elements cover areas such as ownership autonomy, data protection, vulnerability management, patching capabilities and others.
Adopting these internationally recognized best practices helps organizations build resilient OT systems that can withstand evolving cyber threats and comply with regulatory requirements.
Such procurement best practices are increasingly adopted in critical infrastructure sectors such as power, oil & gas, transportation, and water utilities, where operational disruptions can have severe societal impacts. But lacks in several types of manufacturing organizations in general.
For example, water and wastewater utilities face unique challenges due to legacy systems and regulatory compliance demands, making secure procurement vital to protect public health and safety.
Despite these advances, gaps remain. Many OT products still lack comprehensive security features out of the box, and backward compatibility requirements can lead to security features being disabled by default to maintain legacy interoperability.
Furthermore, vendor dependencies and limited operator autonomy can hinder timely patching and incident response.
These shortcomings underscore the need for continuous improvement in procurement policies and collaboration between buyers, vendors, and regulators.
In an earlier edition, IT & OT Cybersecurity Requirements Specifications - Don’ts & Do’s! — I covered few ✅ Deadly Sins (Common Mistakes) & Quick Wins (recommended fixes) for Cybersecurity requirements specification for Industrial environments 🚨- You Can’t Afford to Ignore!
Therefore, as one of the foundational steps of Secure by 3Ds, i.e. secure by demand; its essential to build and document enhanced OT-specific cybersecurity procurement language supported by OT cybersecurity requirements specification as part of the procurement process.
My OTCBPRs toolkit is tailored for asset owners in manufacturing sector, however, most of it can be applied in other sectors as well.
Written By M. Yousuf Faisal (Advice | Consult Cyber & business leaders in their journey on Securing Things (IT, OT/ICS, IIOT, digital transformation, Industry 4.0, & AI) & share everything I learn on this Newsletter | and upcoming Academy).
Together with:
Learn AI in 5 minutes a day
This is the easiest way for a busy person wanting to learn AI in as little time as possible:
Sign up for The Rundown AI newsletter
They send you 5-minute email updates on the latest AI news and how to use it
You learn how to become 2x more productive by leveraging AI
Why Procurement Decisions Matter More Than Ever for Water Security📜
By Alana Murray (an industrial controls expert with 35+ years of experience in critical infrastructure sectors, including water/wastewater utilities. She writes on operational technology security and just about everything else in the industrial control system industry).
After spending over three decades in industrial controls, I've watched the water and wastewater sector transform from simple mechanical systems to complex digital environments.
With this evolution come new vulnerabilities, ones that can't be addressed with traditional security approaches alone.
Recent incidents have made these facts painfully clear.
The breach at the water treatment facility in Oldsmar, Florida, in 2021 wasn't just a wake-up call; it was a stark reminder that poorly secured operational technology (OT), the hardware and software that controls physical equipment and processes, can put public health directly at risk.
An attacker gained access to control systems through outdated remote access software and attempted to increase sodium 1 hydroxide to dangerous levels in the drinking water supply.
Thankfully, an alert operator spotted the change and reversed it before harm occurred.
But we can't rely on lucky catches. We need systematic approaches to security, starting with how we procure OT systems, components, and services.
In part 2 of this series, I’ll dive deeper into the 7 critical steps on OTCS PPP, with specific applications for water and wastewater utilities.
Written by Alana Murray (ICS/OT Enterprise Architect | SCADA/OT Expert | OT Cybersecurity Leader | Water Leadership Innovator | Driving Industry Transformation).
Next Up:
Stay tuned for Part 2 of this series (coming this weekend), where we will dive deep into sector-specific procurement strategies and challenges for Water and Wastewater Utility sector – expert perspective by Alana Murray, directly from her 3+ decades of industry experience, offering tailored guidance to secure these vital services against cyber threats.
Related Resources (Industry Best Practice Guidance)
Here are some interesting references to the guidance and other resources.
Secure by Demand: Priority Considerations for Operational Technology Owners and Operators when Selecting Digital Products by CISA along with U.S. National Security Agency (NSA) U.S. Federal Bureau of Investigation (FBI) U.S. Environmental Protection Agency (EPA) U.S. Transportation Security Administration (TSA) Australian Signals Directorate’s Australian Cyber Security Centre (ASD’s ACSC) Canadian Centre for Cyber Security (CCCS) Directorate General for Communications Networks, Content and Technology (DG CONNECT), European Commission Germany’s Federal Office for Information Security (BSI) Netherlands’ National Cyber Security Centre (NCSC-NL) New Zealand’s National Cyber Security Centre (NCSC-NZ) United Kingdom’s National Cyber Security Centre (NCSC-UK).
Cybersecurity Considerations for Procurement Process by Federal Energy Management Program (FEMP) developed the decision tree to provide a high-level overview of key questions to consider regarding when agency cybersecurity experts should be consulted by facility staff in the procurement of new equipment, systems, or services. They have a “Guide on Cybersecurity Procurement Language in Task Order Requests for Proposals for Federal Facilities” and other related documents. Ensuring cybersecurity from the onset of the process is an important step in protecting federal facility assets, systems, and sites and can help reduce the number of weaknesses or vulnerabilities that must be remediated after the fact. Download the Cybersecurity Considerations for Procurement Process decision tree.

Decision Tree by FEMP
Guidelines for procurement and outsourcing by Australian Signals Directive (ASD) - provides guidance on: Cyber supply chain risk management | Supplier relationship management | Sourcing applications, IT equipment, OT equipment and services | Delivery of applications, IT equipment, OT equipment and services | Cloud & Managed Services | and Contractual security requirements with service providers.
OT CNI Supply Chain Standards
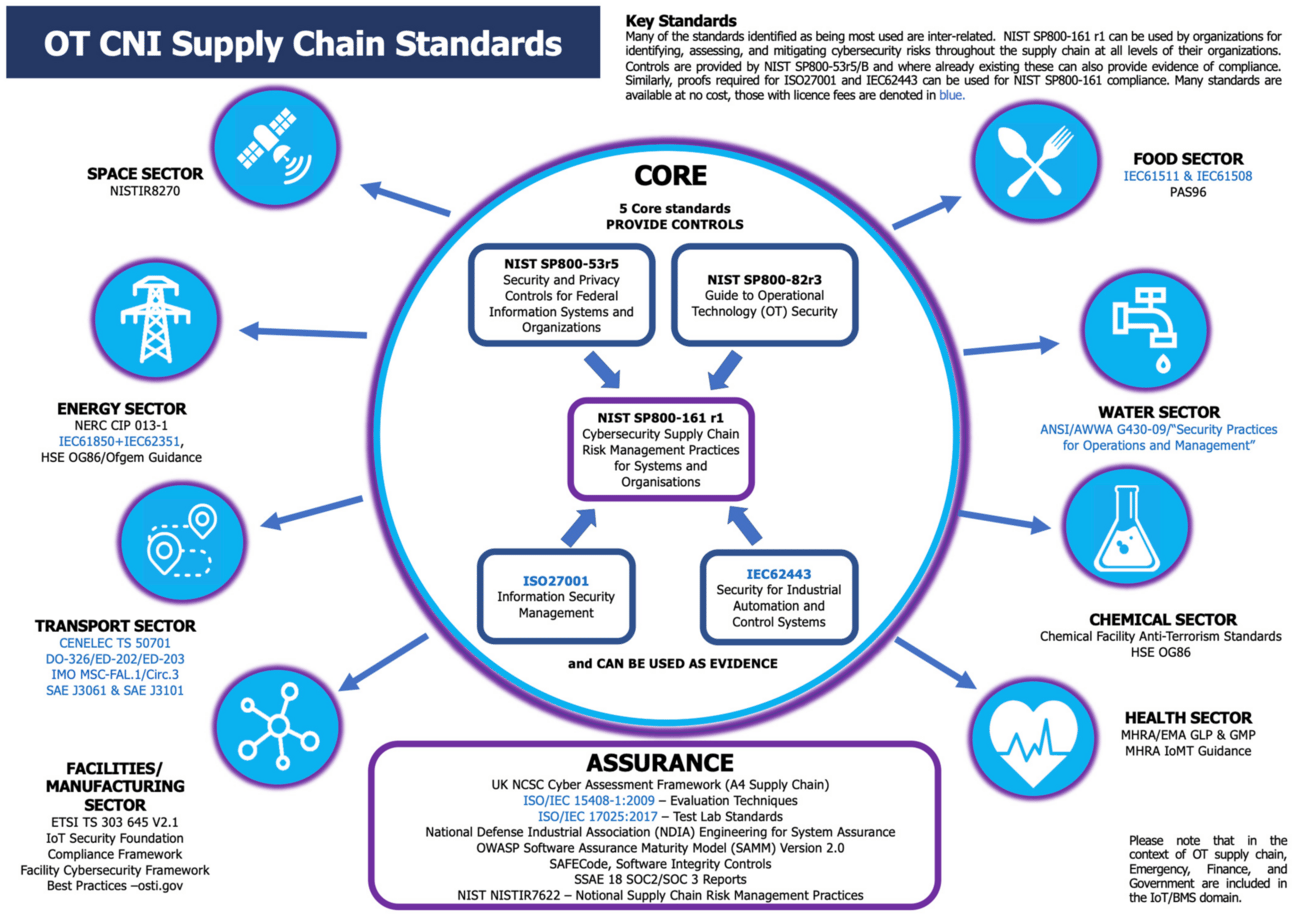
OT CNI Supply Chain Standards
Secure-by-Design: Shifting the Balance of Cybersecurity Risk: Principles and Approaches for Secure by Design Software
Secure by Demand Guide: How Software Customers Can Drive a Secure Technology Ecosystem by CISA.
Sample Cybersecurity Clauses for EV Charging Infrastructure Procurements.
Collaboration Practices for the Cybersecurity of Supply Chains to Critical Infrastructure - by Tania Wallis and Paul Dorey.
Practical guidelines on cybersecurity: Requirements in tendering - by UITP for transportation sector.
Procurement and Cybersecurity: Enhancing Confidence - by Jared Marcotte, published on NASCA Institute website.
NIST 800-161 Cyber Supply Chain Risk Management Practices for Systems and Organisations.
Free Supply Chain Risk Management course.
Vendor Supply Chain Risk Management (SCRM) Template.
CISA Supply Chain Risk Management (SCRM).
‘
CISA Supply Chain Risk Management (SCRM) Essentials.
American Petroleum Institute Oil and Gas Industry Preparedness Handbook.
What Secure By Design Aspects Should You Prioritize? - by Matthew Rogers at S4 conference.
Re-evaluating ICS/OT Procurement Language - SANS ICS Security Summit 2021 - by Sarah Freeman.
My Recent Most Viewed Social Posts:
In case you’ve missed - here are some of my recent most viewed social posts.
📰[ST # 67] The Real Security Risks - Divide between Cyber & Physical ✅Guest Post by Jamie Williams on Modern Cyber-Physical Threats and What Does Good Security Look Like Today? plus my views on the same ✍️ [Securing Things by M. Yousuf Faisal]
📰[ST # 66] ISA/IEC 62443 Standards - Part 6 ✅62443-2-2:2025 IACS Security Protection Scheme, ISASecure Certification Standards, upcoming sessions & newsletters✍️ [Securing Things by M. Yousuf Faisal]
📰[ST # 65] Cybersecurity and AI Across IT-OT Automation Stack - Monthly Digest # 2 ✅ Competence Framework for Solutions Architects and Security Architects on industry 4.0, cybersecurity and AI across the automation stack (Cloud, ERP, DMZ, MES, SCADA, HMI, PLC/Edge), physical devices & more.🚀 [Securing Things by M. Yousuf Faisal]
📰[ST # 63] IT & OT Network Security - Example Do's & Don'ts ✅ Deadly Sins (Common Mistakes) & Quick Wins (recommended fixes) for Industrial / Manufacturing environments. Plus CISO's query and my response on Managed vs. Unmanaged switches for production environment🚀 [Securing Things by M. Yousuf Faisal]
📰 [ST # 62] ✅Cybersecurity Insights from Q1 2025 - ✅ IT, OT, AI Cybersecurity Market Insights, M&As, Incidents, breaches, ransomware, threats and changing regulatory landscape🚀 [Securing Things by M. Yousuf Faisal]
📰[ST # 61] ✅My list of IT-OT & Cybersecurity, Leadership, Productivity, Personal Development, and Money/Business books - must read for Cyber Leaders and Practitioners. Few updates on OT Security conference, & more.🚀 [Securing Things by M. Yousuf Faisal] 📰
📢 [ST #60] All Series Index - Securing Things 📢✅IT, OT & AI Cybersecurity – Program, Digital Factory, Guides, Standards, Crash Courses, Quarterly Insights & more.🚀 [Securing Things by M. Yousuf Faisal] 🗞️🗞️🗞️
Ways in which I can help?
Whenever you are ready - I can help you with:
A - IT & OT Cybersecurity Advisory / Consulting services - for securing your business and or its digital transformation journey.
B - Security Awareness Training & Phishing Awareness Portal - Train your staff and build a Security awareness program through our subscription based service.
C - Securing Things Academy (STA) - Security trainings for IT & OT practitioners.
Visit the newsletter website for Links to above services and or reach out at info[at]securingthings[dot]com or DM me via LinkedIn.
D - Securing Things Newsletter - Sponsor this newsletter to showcase your brand globally, or subscribe to simply Get Smarter at Securing Things.
Reach out at newsletter[at]securingthings[dot]com or DM me via LinkedIn.
Feedback
I invite #SecuringThings community to share their feedback.
Your feedback and input is invaluable to me as we work together to strengthen our cybersecurity defenses and create a safer and smarter digital society. Thank you for your trust and continued support.
Do register, validate your email, and request login link to submit poll to be able to enter a chance to win a future course giveaway. Also:
Rate the newsletter content
Thanks for reading - until the next edition!
It’s a Great Day to Start Securing Things for a Smart & Safer Society.
Take care and Best Regards,





