Disclaimer: All views presented here, in this newsletter, are my own.
Author or the newsletter are not liable for any actions taken by any individual or any organization / business / entity. The information provided is for education and awareness purposes only and is not specific to any business and or situation.
Table of Contents
Hi Securing Things Community,
In this newsletter edition, I’ll be sharing at a very high-level the use of AI within Cybersecurity - some insights, interesting links, guides, posts etc. In addition, some of my most viewed social media posts (in case you’ve not seen), sponsors message and my asks.
In case you are here for the 1st time, I’d humbly request you to have a look at all the previous 25+ editions in which I have focused on different IT and OT cybersecurity, and AI insights, topics, concepts, quarterly reports and more.
Special Message:
Before we begin, do me a favour and make sure you hit the “Subscribe” button to let me know that you care and keep me motivated to publish more. Thanks!
Note: remember to validate your email address to ensure that you don’t miss any future newsletter editions.
Use of AI in Cybersecurity
As with any other industry or business, the proliferation and the use of AI capabilities within the Cybersecurity industry cannot be overlooked as the rising cybersecurity concerns with the use of AI and AI related cybersecurity threats.
Cybersecurity automation using AI has become critical as businesses struggle with security skills and budget shortage. Benefits that’s driving the industry is new forms of AI born cyber attack surface, threats & risks, limiting human error, cost efficiency, automation of processes and better decision making.
Industry is seeing the use of AI in almost all domains across IT & OT cybersecurity, ranging from but not limited to the following:
Governance
Risk identification, Assessment and Risk Management
Security Awareness Program
Secure Software Development
Vulnerability Management
Protection solutions (e.g. use of password EDR tools etc.)
Security Operations
Intrusion Detection solutions
Threat Detection, Hunting, and Intelligence
Incident Response, malware reverse engineering and forensics.
Supplement understaffed security teams.
and more…
Cybersecurity Tools Market using AI
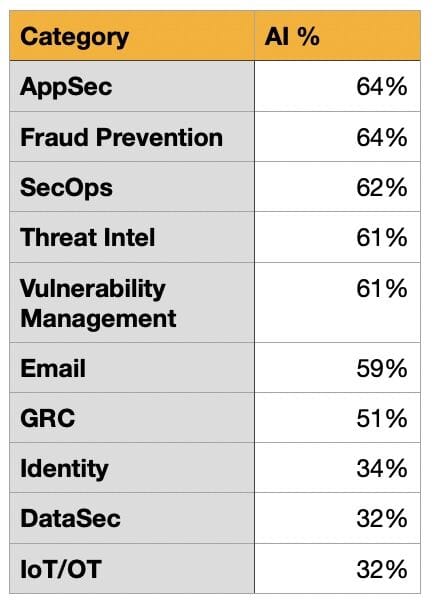
Phil Alape, founder of Cyber Symposiums in his recent LinkedIn post and Richard Stiennon LinkedIn post highlighted the results of the survey from >3000 vendors (who have an AI component in place) across 10 market segments as below:
AI Conference & Bake-Off - Don’t miss the chance for registering for the 10 week online program for AI in Cybersecurity brought to us by Cyber Symposiums + Cloud Security Alliance on Sep 17 - Dec 18, 2024.
I’ve previously shared insights on the list of standards and guidance available that serves around the governing the use of AI. Checkout the following:
AI Cybersecurity Policy & Reference Guidance - which covers; AI cybersecurity policy construction (key elements), steps for a policy build execution project and several reference standards, frameworks and guidance documents.
OWASP notably provides key resources such as their AI security and OWASP AI Exchange, Periodic Table of AI Security, AI Security and Privacy Guide and LLM Top 10. Recently, the group released its LLM AI Cybersecurity & Governance Checklist.
OpenAI recently released a guidance on Optimizing LLMs for Accuracy, with super useful chart below. It’s a reminder for all that this process is not linear, and can reference this chart to shape what techniques to use for individual LLM use case.
Horizontal axis: LLM optimization - how the model needs to act → increase how consistent the behaviour is.
Vertical axis: Context optimization - what the model needs to know → increase accuracy of responses.
Google have SAIF - Secure AI Framework. SAIF is designed to address top-of-mind concerns for security professionals, such as AI/ML model risk management, security, and privacy — helping to ensure that when AI models are implemented, they are secure-by-default.
ISACA have released an AI Governance Toolkit - it’s a paid resource but you can find some description here. The toolkit is a list of checks for assessing governance and controls over the AI system in an enterprise. It provide assistance to auditors in verifying that AI systems adhere to the highest standards of governance and ethical responsibility.
There’s certainly a lot that I didn’t cover above. I’ll be populating the list below in future, so make sure to bookmark this.
Comment below to add anything critical that I have not yet included.
Here’s a Comparison of Top 25 AI Governance Tools - Vendor Benchmark in 2024.
31 Companies to Know in AI Cybersecurity - by Built-In written by Alyssa Schroer covers a list of companies using AI in their cybersecurity tools / solutions offerings.
Governance
List of solutions to be added in future.
Provide your tools/solutions in comment below.
Identification
List of solutions to be added in future.
Provide your tools/solutions in comment below.
Protection
List of solutions to be added in future.
Provide your tools/solutions in comment below.
Detection
List of solutions to be added in future.
Provide your tools/solutions in comment below.
Response
List of solutions to be added in future.
Provide your tools/solutions in comment below.
Recovery
List of solutions to be added in future.
Provide your tools/solutions in comment below.
Do subscribe to ensure that you don’t miss out future posts.
My Recent Most Viewed Posts:
In case you’ve missed - here are some of my recent most viewed social posts.
2 years of Independent Cybersecurity Consulting - Progress, Challenges and lessons learned.
Poll on Crowdstrike / Microsoft BSOD incident causing widespread disruption to businesses worldwide on 19th July 2024.
Chronicles of Cybersecurity Consulting - Shortest Consulting Engagement Ever - 2nd in series.
Getting started in IT & OT Cybersecurity - a blueprint / framework to 2x / 5x / 10x your cybersecurity career. Links in comments of the above post.
Internal Audit and IT & OT Cybersecurity Program - suggested approach for an internal audit team towards building their knowledge / skill base and be able to ask relevant questions towards an IT & OT Cybersecurity / transformation programs activities.
Securing Things Academy Promo released or download below.
Securing Things Academy:
IT & OT CySEAT (Cyber Security Education And Transformation) course is designed for IT and OT cybersecurity practitioners. Join the wait-list → here.
Checkout a brief overview below:
Ways in which I can help?
Whenever you are ready - I can help you with:
A - IT & OT Cybersecurity Advisory / Consulting services - for securing your business and or its digital transformation journey.
B - Security Awareness Training & Phishing Awareness Portal - Train your staff and build a Security awareness program subscription based service.
C - Securing Things Academy (STA) - Security trainings for IT & OT practitioners.
Visit the newsletter website for Links to above services and or reach out at info[at]securingthings[dot]com or DM me via LinkedIn.
D - Securing Things Newsletter - Sponsor this newsletter to showcase your brand globally, or subscribe to simply Get Smarter at Securing Things.
Reach out at newsletter[at]securingthings[dot]com or DM me via LinkedIn.
How are we doing?
I invite you as part of #SecuringThings community to share your feedback.
Rate the newsletter content
Your feedback and input is invaluable to me as we work together to strengthen our cybersecurity defenses and create a safer and smarter digital society.
Let us know how we can improve this and or what you’d like to see in future?
Thank you for your trust and continued support.
Do register, validate your email, and request login link to submit poll to be able to enter a chance to win a future course giveaway.
Thanks for reading - until the next edition!
It’s a Great Day to Start Securing Things for a Smart & Safer Society.
Take care and Best Regards,
M. Yousuf Faisal. (Advice | Consult Cyber & business leaders in their journey on Securing Things (IT, OT/ICS, IIOT, digital transformation, Industry 4.0, & AI) & share everything I learn on this Newsletter | and upcoming Academy).
The Newsletter Platform Built for Growth
When starting a newsletter, there are plenty of choices. But there’s only one publishing tool built to help you grow your publications as quickly and sustainably as possible.
Beehiiv was founded by some of the earliest employees of the Morning Brew, and they know what it takes to grow a newsletter from zero to millions.
The all-in-one publishing suite comes with built-in growth tools, customization, and best-in-class analytics that actually move the needle - all in an easy-to-use interface.
Not to mention—responsive audience polls, a custom referral program, SEO-optimized webpage’s, and so much more.
If you’ve considered starting a newsletter, there’s no better place to get started and no better time than now.