Singapore CII (Critical Information Infrastructure) CCOP v2 Overview
Disclaimer: All views presented here, in this newsletter, are my own.
Author or the newsletter are not liable for any actions taken by an individual or an organization / business / entity. The information provided is for education and awareness and is not specific to any business or situation.
Table of Contents
For those of you who are based in Singapore (SG) or serve clients (either tech/security vendors or a service providers) and work for any organization in SG that is classified as CIIO (definition below) are (/ should be) very well aware of existence and importance of Cyber-security Act 2018 and CCOP requirements for CIIO and need for compliance.
Goal of this article is to raise awareness and provide brief overview and guidance on the CCOPv2 requirements for CIIO and the major changes that have been introduced and its impact to stakeholders (IT and OT professionals & executives) that are charged to bringing their organisation in compliance with new requirements in tough timelines.
Securing Things Academy: (coming soon)
Singapore CCOP Master Class course is designed for IT and OT cybersecurity practitioners. Join the wait-list → here.
Checkout a short teaser below:
Background & Introduction
Cybersecurity Act 2018 (Act. 9 of 2018) (the Act), which was passed by the Singapore Parliament on 5 February 2018, came into force on 31 August 2018. Noticeable hacks around the time were, WannaCry Ransomware 2017, MINDEF got hacked in 2017, SingHealth got hacked in 2018 (1.5 million patient records of SG residents with stolen) to name a few.
CSA Cybersecurity Act 2018 - Overview
Key goals for Cybersecurity Act 2018 by Cybersecurity Agency of Singapore are:
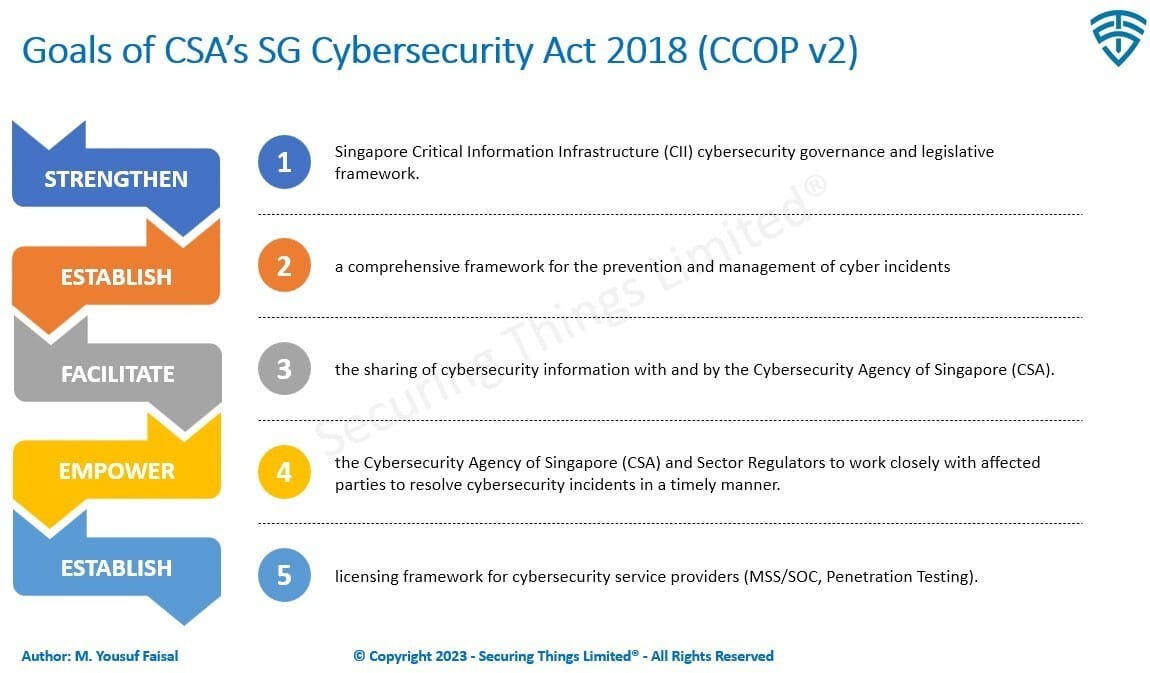
SG CSA's Goals
Key Definitions and Timelines
Below slide outlines some key terms and definitions along with important timelines for compliance with CCOP v2.
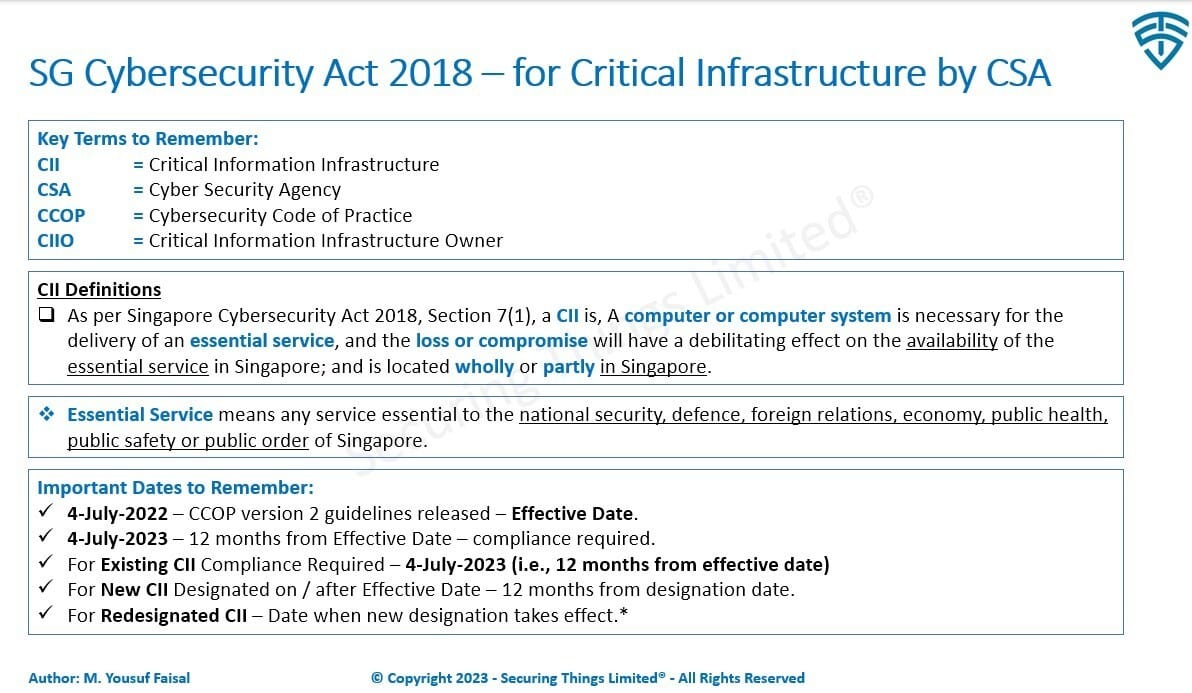
CSA CCOP v2 for CII - Definitions and Timelines
CCOP v2 for CII takes effect from 4 July 2022, superseding previous versions. The objective is to specify "minimum security requirements" that CIIO organizations shall implement as part of their overall security program. In addition, its expected from CIIO organizations to have additional controls in place for further enhancing cybersecurity measures based on CIIO's risk profile.
Singapore (SG) CII Designation Process Matrix

CSA SG CII Designation Process Matrix (not an exhaustive list)
The above slide highlights a very high-level view of the key entities / stakeholder's involvement, their relationships, the designation process and their role & responsibilities for identifying, designating, operating/complying and supporting certain required activities related to CCOP. Note: this is not an exhaustive list of activities on what each stakeholder involved, does.
SG CII Industry Sectors Identified
CSA have identified 11 sectors to be classified as CII and they are:
Note: Any Singapore based organization within any of these sectors would likely be a CIIO (CII owner).
SG CII Industry Sectors
From CCOP v1.1 to CCOP v2 - Major Changes Overview
There are major changes in this revision. The requirements have been increased significantly compared to the prevision version (roughly if there were 102 requirements in 1.1, they are now around 220 approx.). CCOP v 2 provides enhanced clarity in new, amended and existing clauses and have incorporated guidance:
from SingHealth Committee of Inquiry (COI) recommendations
from Public Sector Data Security Review Committee (PSDSRC)
from NIST 800-53 Rev. 5 for measures around IT and OT systems
from Secure PLC Coding Practices Top 10 v1 for OT systems.
in Annex A for strengthening organizational cybersecurity posture.
SG CII CCOP v2 IT & OT Topics Summarized
CCOP v2 covers quite a number of requirements covering domains and topics both from IT and OT cybersecurity controls perspective.
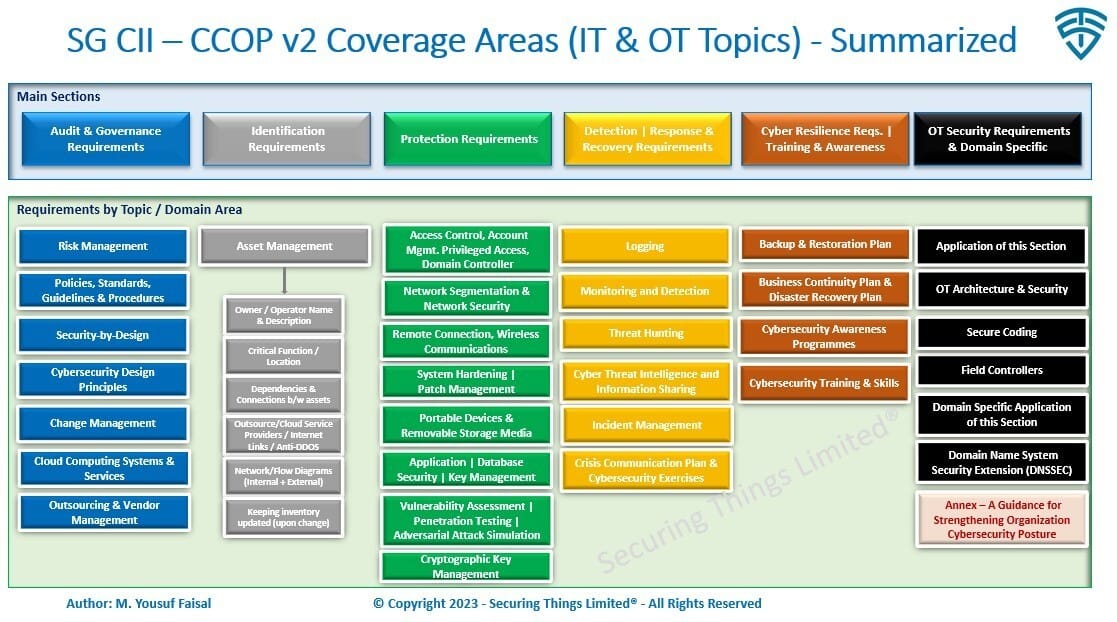
SG CII CCOP v2 Requirements Summary
Recurring Requirements / Control Activities & their Frequency
Several clauses in CCOP v2 requires certain actions to be performed (e.g., reviews) at fixed intervals (e.g., at-least once every 12 months) referred to as "Recurring Requirement". These relevant clauses prescribe the deadline for the first instance of the act and subsequent instances are from the date when previous instance was performed.
There are other requirements around "actions" (including new) to be conducted, in both IT and OT at-least every 12 months and or every 24 months.
Yearly Review Requirements (Recurring)

Yearly Review Requirements (Recurring)
Recurring Action Requirements
To conduct Vulnerability Assessment of CII for IT (within 12 months) and OT (within every 24 months - first instance 12 months after compliance date)
To conduct Penetration Testing of CII for IT (within 12 months) and OT (within every 24 months - first instance 12 months after compliance date) (New Update for OT CIIs)
To conduct Red Teaming or Purple Teaming attack simulation (within every 24 months - first instance 12 months after compliance date)
To conduct Threat Hunting for CII (within every 24 months - first instance 12 months after compliance date) (New Update)
To conduct Scenario-based cybersecurity exercises (within every 12 months - first instance 12 months after compliance date) (New Update)
To measure effectiveness of cybersecurity awareness program through means such as quizzes and surveys (within every 12 months - first instance 12 months after compliance date) (New Update).
Note: there are two other recurring Action requirements that are not explicitly mentioned in CCOP v2 document, but are required to be done by CIIO:
Cybersecurity Risk Assessment (frequency = 12 months) (1st instance = 6 months upon designation) - (Relevant Clause = Cybersecurity Act 15 (b))
CII Compliance Audit (frequency = 24 months) (1st instance = 24 months upon designation) - (Relevant Clause = Cybersecurity Act 15 (a)).
Audit & Governance Requirements (+ What's New):
Below are example lists of key changes for Audit (previously used word Compliance) & Governance requirements.
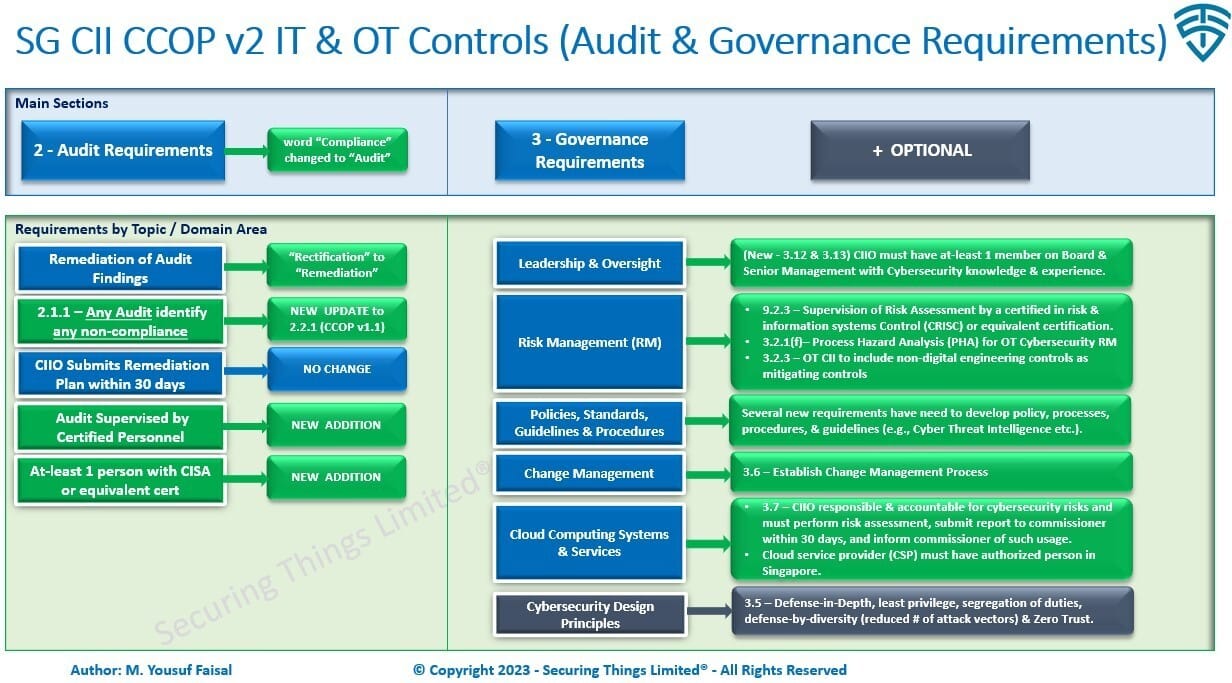
SG CII CCOP v2 Audit & Governance Requirements
See my #OTSecurityDozen series Part 2 OT / ICS Cyber security Policy & Governance on #SecuringThings newsletter for guidance on OT governance / policy.
Identification Requirements (+ What's New):
Identification requirements include the most fundamental elements of any security program and tops the list of major international standards and industry best practices guidance - i.e., building and maintaining an accurate Asset Inventory and the whole process of Asset Management. This is a fundamental and common requirement for both IT and OT CIIOs. Below slide highlights the main requirements under Asset Management with no changes and the newly added requirements as well.

Identification Requirements
See my #OTSecurityDozen series Part 4 Asset, Vulnerabilities, Risk Discovery & Threat Detection on #SecuringThings newsletter for guidance on OT asset discovery, inventory and management for CIIOs with CII OT networks.
Protection Requirements (+ What's New):
Below are example lists of key changes for Protection requirements:

Protection Requirements
See my #OTSecurityDozen "The OT Security Dozen" – A 12 Part Series on Building an OT / ICS Cyber Security Program series Part 3 on OT/ICS Network Security Architecture & Segmentation on #SecuringThings newsletter for guidance on OT network security and segmentation for CIIOs with CII OT networks. More on these requirements in future posts.
Detection, Response & Recovery Requirements (+ What's New):
Below are example lists of key changes for detection, response and recovery requirements:

Detection, Response & Recovery Requirements
Also, see my Endpoint Detection & Response (EDR) Solutions for IT & OT/ICS and Part 4 Asset, Vulnerabilities, Risk Discovery & Threat Detection posts on #SecuringThings newsletter for guidance on deploying endpoint security solutions for CIIOs with CII IT and OT networks.
Cyber Resilience Requirements & Training/Awareness (+ What's New):
Unlike CCOP v1.1 with 4 auditable clauses; CCOP v2.0 have 7 auditable clauses.

Cyber Resilience, Cybersecurity Training & Awareness Requirements
OT Security Requirements & Domain Specific (+ What's New):
Below are example lists of key changes for OT Security requirements (previously Annex A, version 1.1) and domain specific practices:
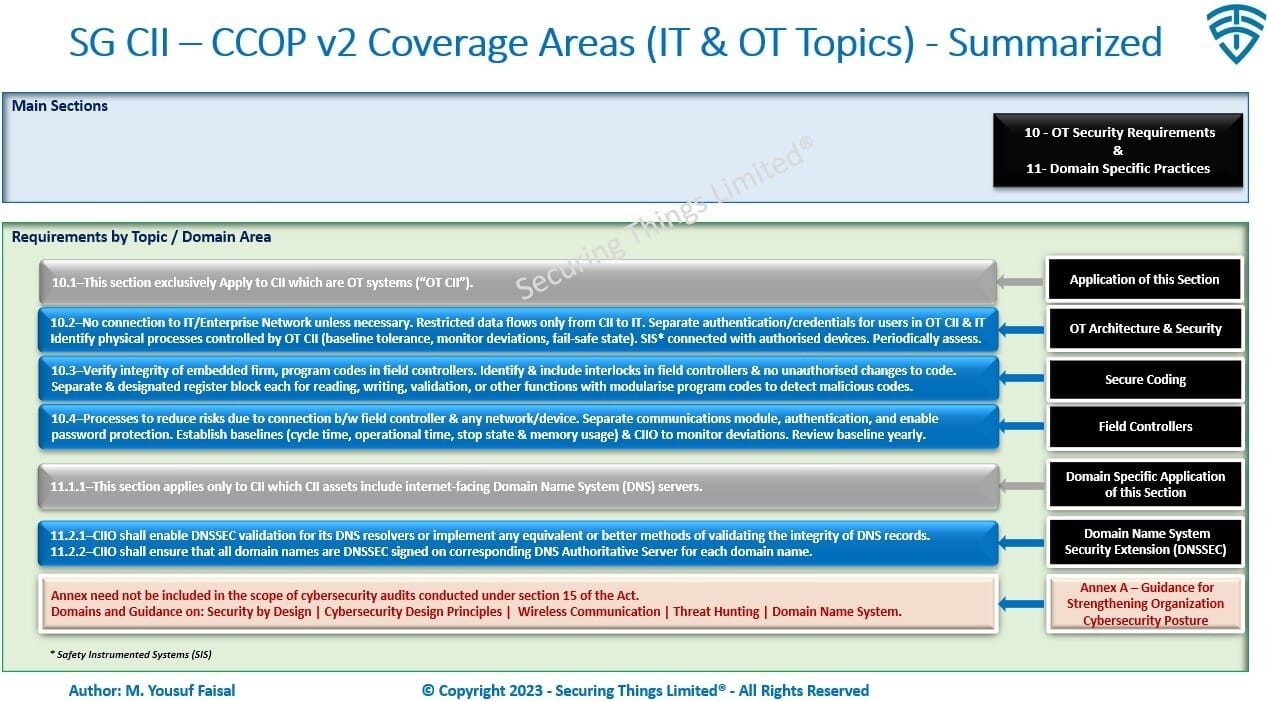
OT Security Requirements & Domain Specific Practices
See my #OTSecurityDozen "The OT Security Dozen" – A 12 Part Series on Building an OT / ICS Cyber Security Program series and other posts for OT specific requirements.
Conclusions & Next Steps:
It's time now that CIIO's have:
identified all applicable clauses for their specific CII environment and ensure document enough evidence for clauses that are considered to be not applicable.
clarified any clauses with CSA early, on guidance to comply and for any clauses for which seeking waiver (apply earlier) or identify mitigating controls prior.
conducted gap assessment and have plans in place for remediation.
scheduled recurring activities/actions to meet required timelines per CCOP.
documented evidence for CII compliance audit and response to auditor's RFI.
References:
https://www.csa.gov.sg/docs/default-source/csa/documents/legislation/ccop_second-edition.pdf?sfvrsn=b2ab666a_0
https://www.csa.gov.sg/Legislation/Cybersecurity-Act
https://www.csa.gov.sg/Tips-Resource/publications/2021/overview-of-legislations
https://www.csa.gov.sg/docs/default-source/csa/cybersecurity_bill/cybersecurity-act---explanatory-statement.pdf?sfvrsn=65ec5bc7_0
https://www.csa.gov.sg/our-programmes/support-for-enterprises/sg-cyber-safe-programme/cybersecurity-certification-scheme-for-organisation
https://www.csa.gov.sg/our-programmes/support-for-enterprises/sg-cyber-safe-programme/cybersecurity-certification-scheme-for-organisation/cybersecurity-health-plan
https://www.csa.gov.sg/Tips-Resource/publications/2022/cii-supply-chain-programme-paper
Good luck for your security journey while keeping up with compliance mandates.
Take care. Love & Peace!
Follow me M. Yousuf Faisal and #securingthings @securingthings on twitter.
& Subscribe to SecuringThings Newsletter on LinkedIn.
#energysecurity #maritimesecurity #healthcarecybersecurity #watersecurity #landtransportsecurity #aviationsecurity #mediasecurity #informationcommunicationsecurity #bankingfinancesecurity #governmentsecurity #cybersecurity #itsecurity #otsecurity #criticalinfrastructuresecurity #criticalinfrastructureprotection #smbcybersecurity #businessrisk #digitalrisk #digitaltransformation #securedigitaltransformation #security #cyberawareness #securityawareness #riskmanagement #cybersecurityprogram #securityeducation #cyberrisk #compliance #securitycompliance #risk #energyindustry #maritime #securitycompliance #transportsectors #aviationsector #railsector #mediasector #finance #banking #watersector #singapore #csa #sgcsa #government
The Newsletter Platform Built for Growth
When starting a newsletter, there are plenty of choices. But there’s only one publishing tool built to help you grow your publications as quickly and sustainably as possible.
beehiiv was founded by some of the earliest employees of the Morning Brew, and they know what it takes to grow a newsletter from zero to millions.
The all-in-one publishing suite comes with built-in growth tools, customization, and best-in-class analytics that actually move the needle - all in an easy-to-use interface.
Not to mention—responsive audience polls, a custom referral program, SEO-optimized webpages, and so much more.
If you’ve considered starting a newsletter, there’s no better place to get started and no better time than now.



