Disclaimer: All views presented here, in this newsletter, are my own.
Author or the newsletter are not liable for any actions taken by any individual or any organization / business / entity. The information provided is for education and awareness purposes only and is not specific to any business and or situation.
Hey, Yousuf here.
Hope you are doing well.
I’ve been busy with some travel and lately some other personal issues and hence missed reaching out to you all.
🔐📘- A CISO recently asked, as part of the OT Secure remote access project, whether to put the jump servers in a workgroup and or join them as part of IT Active Directory (AD) domain or OT AD domains. Given the environment have no specific / separate OT Active Directory domain.
So let’s examine few pros and cons on each of the scenarios.🚨🔥
♻️if you know someone in your professional circle who will benefit from this guidance and or are interested in learning. Thanks 🌟
So let’s dig in.
Yours truly.
— Yousuf.
I see many of you visit the newsletter site, consume the content, however, a low percentage of you actually registers.
So before we begin, do me a favour and make sure you hit the “Subscribe” button to let me know that you care or liked what you’ve read and keep me motivated to publish more. Thanks!
Together with:
Organizations that need security choose Proton Pass
Proton Pass Business is the secure, streamlined way to manage team credentials. Trusted by over 50,000 businesses worldwide, Pass was developed by the creators of Proton Mail and SimpleLogin and featured in TechCrunch and The Verge.
From startups to nonprofits, teams rely on Proton Pass to:
Share passwords safely with end-to-end encryption
Manage access with admin controls and activity logs
Enforce strong password policies with built-in 2FA
Revoke access instantly during employee turnover
Simplify onboarding and offboarding across departments
Whether you're running IT for a global team or just want Daryl in accounting to stop using “password123,” Proton Pass helps you stay compliant, efficient, and secure — no training required.
Join the 50,000+ businesses who already trust Proton.
Jump Servers - Domain or Workgroup📜
When deciding whether to use a workgroup computer, an IT domain-joined computer, or an OT-specific Active Directory domain for a jump server in the specialized OT secure remote access solution architecture for secure remote access, it's important to consider the security implications, operational challenges, and feasibility of each option.
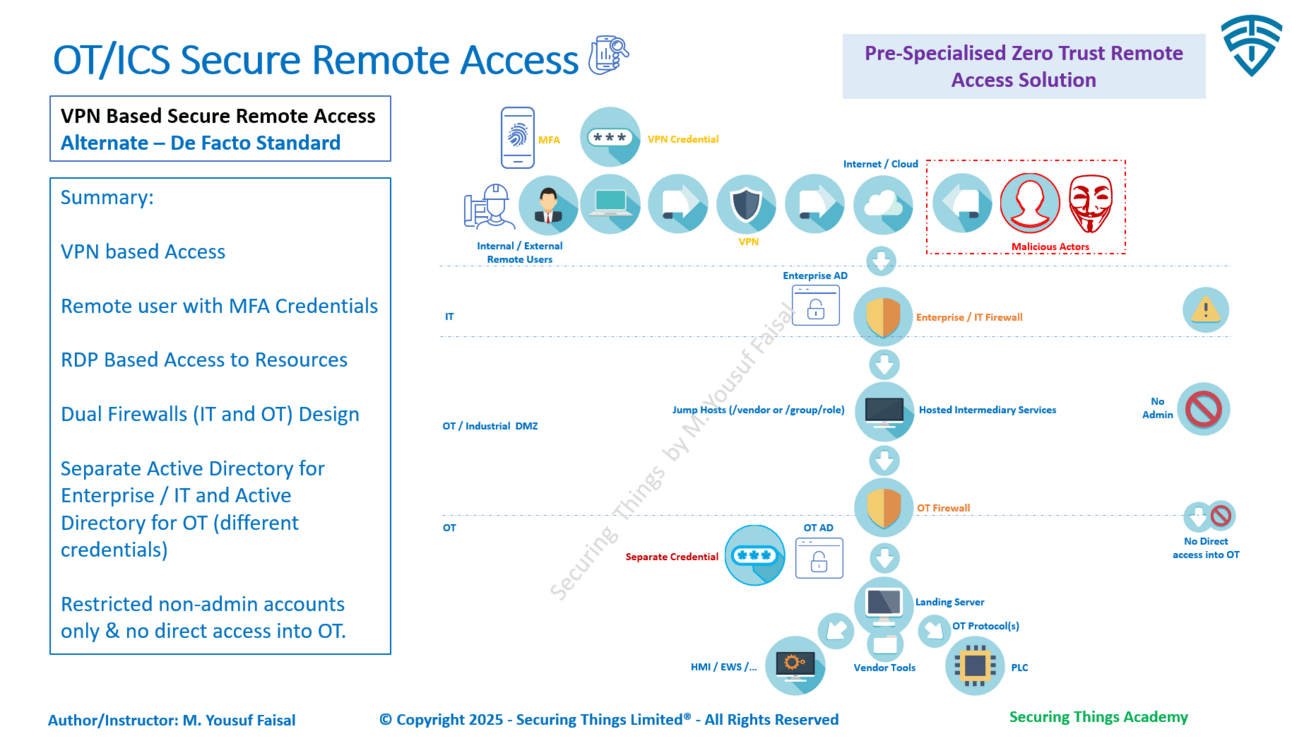
STA - Secure Remote Access
Workgroup Computer
Pros:
Isolation A workgroup is not connected to a central domain, which can reduce the risk of lateral movement in case of a compromise. If the jump server is compromised, attackers may not be able to easily access other domain resources.
Simplicity Workgroups are simpler to set up and manage than domains, as they don't require a domain controller or complex configurations.
Cons:
Management Overhead Managing user accounts, permissions, and security policies on each workgroup computer can be time-consuming and difficult to scale.
Security Risks Workgroups lack centralized security controls, making them more vulnerable to attacks. It's harder to enforce strong password policies, multi-factor authentication, and other security measures.
Limited Auditability Auditing and monitoring user activity on workgroup computers can be challenging due to the lack of centralized logging and reporting.
Operational Challenges:
Credential Management Managing separate credentials for each workgroup computer can be a burden for both users and administrators.
Software Updates Ensuring that all workgroup computers have the latest security patches and software updates can be difficult without centralized management tools.
IT Domain-Joined Computer
Pros:
Centralized Management IT domains provide centralized management of user accounts, permissions, and security policies, simplifying administration and improving security.
Improved Security IT domains offer advanced security features such as Group Policy, which can be used to enforce strong password policies, restrict software installation, and configure security settings.
Simplified Auditing IT domains provide centralized logging and reporting, making it easier to audit and monitor user activity.
Cons:
Increased Risk of Lateral Movement If the jump server is compromised, attackers may be able to use the domain credentials to access other resources in the IT domain.
Potential for Conflicts IT domain policies and configurations may conflict with the security requirements of the OT environment.
Trust Relationship Risks: A direct trust between the IT and OT domains can create a path for attackers to move from one environment to the other.
Operational Challenges:
Compliance Issues Connecting the jump server to the IT domain may violate compliance regulations that require strict separation of IT and OT environments.
Maintenance coordination IT-driven updates or policy changes could inadvertently impact OT operations, requiring careful coordination and testing.
OT-Specific Active Directory Domain
Pros:
Centralized Management for OT An OT-specific Active Directory domain provides centralized management of user accounts, permissions, and security policies tailored to the OT environment.
Improved Security for OT An OT-specific Active Directory domain allows you to implement security controls that are specific to the OT environment, such as restricting access to critical systems and monitoring user activity.
Reduced Risk of Lateral Movement By keeping the OT Active Directory domain separate from the IT domain, you can reduce the risk of lateral movement in case of a compromise.
Cons:
Increased Complexity Setting up and managing a separate Active Directory domain for the OT environment adds complexity to the overall infrastructure.
Resource Requirements An OT-specific Active Directory domain requires dedicated hardware and software resources, which can increase costs.
Expertise Required Managing an Active Directory domain requires specialized knowledge and skills, which may not be readily available in the OT environment.
Operational Challenges:
Synchronization Maintaining consistent user accounts and permissions between the IT and OT Active Directory domains can be challenging and require additional tools and processes.
Training OT staff may need additional training to manage and maintain the OT Active Directory domain.
Recommendation
Given the pros and cons of each option, using an OT-specific Active Directory domain is generally the most feasible option for the jump server in the OT secure remote access solution architecture. While it introduces additional complexity and resource requirements, it provides the best balance of security, manageability, and compliance for the OT environment.
By isolating the OT Active Directory domain from the IT domain, you can reduce the risk of lateral movement and implement security controls tailored to the specific needs of the OT environment.
However, if an OT-specific Active Directory domain is not feasible due to resource constraints or lack of expertise, an IT domain-joined computer may be a viable alternative, provided that appropriate security measures are taken to mitigate the risks of lateral movement and conflicts with OT security requirements. These measures may include:
Implementing strong network segmentation to isolate the jump server from other resources in the IT domain.
Using separate accounts for IT and OT administration.
Enforcing multi-factor authentication for all users accessing the jump server.
Regularly monitoring the jump server for suspicious activity.
A workgroup computer should only be considered as a last resort, as it lacks the centralized management and security controls necessary to protect the OT environment from cyber threats.
If a workgroup computer is used, it is essential to implement compensating controls such as:
Using strong, unique passwords for all user accounts.
Disabling unnecessary services and applications.
Regularly patching the operating system and applications.
Implementing host-based intrusion detection and prevention systems.
My Recent Most Viewed Social Posts:
In case you’ve missed - here are some of my recent most viewed social posts.
📰[ST # 69] 🗞️ OT Cybersecurity Procurement Process & Practices (OTCS PPP) an ultimate guide - Part 2 ✅Tailored strategies for the Water & Wastewater Utility sector by Alana Murray, related resources, upcoming part & webinar etc. ✍️[Securing Things by M. Yousuf Faisal].
📰[ST # 68] 🗞️ OT Cybersecurity Procurement Process & Practices (OTCS PPP) an ultimate guide - Part 1 ✅The foundations & international best practices for OT cybersecurity procurement with Alana Murray, reference resources and more ✍️ [Securing Things by M. Yousuf Faisal]
📰[ST # 67] The Real Security Risks - Divide between Cyber & Physical ✅Guest Post by Jamie Williams on Modern Cyber-Physical Threats and What Does Good Security Look Like Today? plus my views on the same ✍️ [Securing Things by M. Yousuf Faisal]
📰ISA/IEC 62443 Standards - Part 6 ✅62443-2-2:2025 IACS Security Protection Scheme, ISASecure Certification Standards, upcoming sessions & newsletters✍️ [Securing Things by M. Yousuf Faisal]
📰[ST # 65] Cybersecurity and AI Across IT-OT Automation Stack - Monthly Digest # 2 ✅ Competence Framework for Solutions Architects and Security Architects on industry 4.0, cybersecurity and AI across the automation stack (Cloud, ERP, DMZ, MES, SCADA, HMI, PLC/Edge), physical devices & more.🚀 [Securing Things by M. Yousuf Faisal]
📰[ST#64] IT & OT Cybersecurity Requirements Specifications - Do’s & Don’ts ✅ Deadly Sins (Common Mistakes) & Quick Wins (recommended fixes) for Cybersecurity requirements specification for Industrial environments 🚨- You Can’t Afford to Ignore! Plus🚨Announcement on OT Cybersecurity Procurement Process & Practices Series - an ultimate guide for IT-OT Tech, Cybersecurity & Procurement Professionals. [Securing Things by M. Yousuf Faisal]
📰[ST # 63] IT & OT Network Security - Example Do's & Don'ts ✅ Deadly Sins (Common Mistakes) & Quick Wins (recommended fixes) for Industrial / Manufacturing environments. Plus CISO's query and my response on Managed vs. Unmanaged switches for production environment🚀 [Securing Things by M. Yousuf Faisal]
📰[ST # 61] ✅My list of IT-OT & Cybersecurity, Leadership, Productivity, Personal Development, and Money/Business books - must read for Cyber Leaders and Practitioners. Few updates on OT Security conference, & more.🚀 [Securing Things by M. Yousuf Faisal] 📰
📢 [ST #60] All Series Index - Securing Things 📢✅IT, OT & AI Cybersecurity – Program, Digital Factory, Guides, Standards, Crash Courses, Quarterly Insights & more.🚀 [Securing Things by M. Yousuf Faisal] 🗞️🗞️🗞️
Ways in which I can help?
Whenever you are ready - I can help you with:
A - IT & OT Cybersecurity Advisory / Consulting services - for securing your business and or its digital transformation journey.
B - Security Awareness Training & Phishing Awareness Portal - Train your staff and build a Security awareness program through our subscription based service.
C - Securing Things Academy (STA) - Security trainings for IT & OT practitioners.
Visit the newsletter website for Links to above services and or reach out at info[at]securingthings[dot]com or DM me via LinkedIn.
D - Securing Things Newsletter - Sponsor this newsletter to showcase your brand globally, or subscribe to simply Get Smarter at Securing Things.
Reach out at newsletter[at]securingthings[dot]com or DM me via LinkedIn.
How are we doing?
I invite you as part of #SecuringThings community to share your feedback.
Rate the newsletter content
Your feedback and input is invaluable to me as we work together to strengthen our cybersecurity defenses and create a safer and smarter digital society.
Let us know how we can improve this and or what you’d like to see in future?
Thank you for your trust and continued support.
Do register, validate your email, and request login link to submit poll to be able to enter a chance to win a future course giveaway.
Thanks for reading - until the next edition!
It’s a Great Day to Start Securing Things for a Smart & Safer Society.
Take care and Best Regards,
M. Yousuf Faisal (Advice | Consult Cyber & business leaders in their journey on Securing Things (IT, OT/ICS, IIOT, digital transformation, Industry 4.0, & AI) & share everything I learn on this Newsletter | and upcoming Academy).




