Disclaimer: All views presented here, in this newsletter, are my own.
Author or the newsletter are not liable for any actions taken by any individual or any organization / business / entity. The information provided is for education and awareness purposes only and is not specific to any business and or situation.
Hi there,
Hope you are doing well.
In this edition, I’ll be sharing some:
✍️Common Issues I’ve observed across OT/ICS Network Architectures.
📘 Recommended fixes to uplift OT/ICS Network Security without heavy $$.
↪️ CISO’s queries on the use of Managed vs. Un-Managed switches.
📲Updates - Recent & upcoming OT virtual conferences.
✍️ Upcoming newsletters & call for expert input & shares.😉
But before we begin, do me a favour and make sure you “Subscribe” to let me know that you care and keep me motivated to publish more. Thanks!
Ready? let’s dig in.
Yours truly.
— Yousuf.
Securing Things Academy:
IT & OT CySEAT (Cyber Security Education And Transformation) course is designed for IT and OT cybersecurity practitioners. Join the wait-list → here.
Checkout a brief overview below:
OT / ICS Network Security - Don’ts & Do’s!
I have reviewed and or looked at a few IT and OT network architectures for critical infrastructure sectors e.g. power/utility, energy, and in particular manufacturing sector specific industrial environments; and there’s a common set of issues, mistakes and errors I have observed that a typical manufacturing organisation makes, whether big or small. Here’s a list of few issues that are often observed:

STL IT OT Network Security Dos & Don’ts by M Yousuf Faisal
Don’ts / Sins
Here are few example list of common issues I’ve observed across manufacturing sector when it comes to IT and OT / ICS Networks (in no particular order):
Flat IT/OT network - no separation or segmentation between IT & OT.
Direct Internet Access from OT Assets / devices - all OT assets are allowed outbound access to / can reach internet directly.
Dual homed devices - assets (windows, PLCs etc.) with one interface connected to IT and other to OT network and or multiple zones/subnets.
Insecure Remote Access - direct remote access from internet to internal assets bypassing firewall and other security controls.
No OT DMZ - no intermediary zones and or sub-zones between IT and OT.
Open rules on firewalls b/w IT & OT - firewall with all ports / traffic allowed, to/from, arguing that at-least firewall is doing packet inspection. ;-)
Misconfigured VLANs Limited segmentation using firewall and VLANs - often misconfigured. Same VLANs traversing IT and OT network subnets. Mis configured and or misplaced IT / OT assets in wrong VLANs, e.g., OT assets with IT VLANs assigned and vice versa.
Direct Wireless connections - wireless networks connected to OT networks and not firewalled off.
No edge driven architecture - missing design the architecture where only edge driven architecture is allowed.
Shared Active Directory - another classic one is having a shared Active Directory b/w IT and OT networks, but on top all traffic from AD to machines in OT network is allowed on all ports.
Patching directly from the internet - most common form of this issue is directly related to point #2 earlier, most end points are allowed to go online to directly fetch patches, firmware’s and or signature updates from the internet.
No Time source used / Direct use of External Time source - time is fetched from internet sources - no use of stratum hierarchy.
So how do we address these issues? while not the intent of this article to go into details on how to fix each of these problems, here’s a brief overview of what you should be doing instead.
Do’s / Wins
Here are the associated Do’s or Wins or fixes to the above list of common issues without spending too much $$$$ to uplift security state of IT and OT / ICS Networks for industrial / manufacturing environment (in no particular order):
Segment IT & OT Networks - Let’s say you are just starting out on this journey and a brownfield (exiting old setup) environment; begin with identifying assets on both IT and OT sides that needs to communicate with each other along with identifying specific ports, next use whatever options you have available in the current technology stack, e.g. you’d usually have an IT firewall with unused interfaces, some layer 3 devices (switches / routers) with unused ports and ACLs functionality; start utilizing those interfaces to separating IT & OT networks into separate zones - one internal interface used for your IT/enterprise network, one for external interface for internet, and than one DMZ interface for a zone hosting assets with shared services between IT and OT and lastly an OT/ICS zone (most secure internal zone) for your production environment. Until you get the required $$$ budget for big fully network security re-architecture project.
No internet access from OT assets - Deny all outgoing traffic from all OT assets (specially windows/Linux based devices as a starting point immediately) to the internet.
Restrict use of dual homed assets/devices – must not connect to IT & OT network at the same time.
Use Secure Remote Access methods only – avoid using insecure methods (e.g. direct RDP, no MFA, web based) bypassing enterprise control. Instead of traditional VPNs, use more advanced secure remote access solution supporting Zero trust. If budget is a constraints, at-least using VPNs with MFA.
Create a DMZ b/w IT & OT – define an intermediary zone (and ideally sub-zones) for separation between IT and OT networks, restricting all access coming from IT to be terminated at DMZ with no direct internet or IT assets accessing assets in OT directly.
Wireless connections firewalled – Avoid connecting Wireless connections directly to IT LAN and especially OT LAN / zone. Make sure there’s a firewall and ideally an IDS/IPS on top of all wireless based access and restrict traffic for what is required only.
Restricted firewall rules b/w IT & OT – Often overlooked, ensure to avoid open (any-to-any) and or zone to zone full open access rules in firewall. Ensure that even if you have to allow some traffic from IT to OT due to existing design limitations, it is restricted to specific IPs and ports numbers only to start with, while in longer term adjusted according to a proper rules once network is re-architected later.
Misconfigured VLANs - Ensure VLANs are not traversing across IT & OT networks and correct VLAN assignments.
Edge driven network architecture – put that as a principle or policy to only use edge driven network architectures.
Shared Active Directory - start with planning for separating IT and OT shared active directory to separate AD instances. For immediate action, until done, try restricting traffic from AD traffic required to work in OT based on specific AD IP addresses instead of allowing entire AD zone.
Patch OT systems through intermediaries instead of internet or at-least restrict the traffic source/destinations - Ideally, a best practice is to ensure that you have not setup OT assets to directly fetch OS, firmware and or other signature updates directly from internet and instead use management systems to be placed either in DMZ to receive updates from IT/internet from specific designated IP addresses and than push them to OT zones. Same for getting updates on systems in IT.
Design & Use of Stratum Hierarchy - fetch time from dedicated internal sources for OT assets instead from internet. If change requires time, start with limiting the NTP port with a dedicated external time source IP address.
Security risks using unmanaged switches in OT networks
Few weeks ago a global CISO queried about managed vs. un-managed switches. This was the second time within a year’s or so when a CISO reached out, going through OT security projects, inquiring about this. He asked the following (para-phrasing here):
“Hi Yousuf, what are pros/cons on using managed vs. un-managed switches? Is the understanding correct that it should be Managed layer 3 switches. Do you know if Unmanaged industrial switches will not support port span, traffic capture and monitoring functions? Understand that unmanaged switches can have security issues as they can not be configured. I am checking this both from an OT Policy and OT network visibility / monitoring”.
So I thought of summarizing my responses for other Security Practitioners and or CISOs / CIOs that are going through similar projects to help build some understanding around this.
Key Differences:
Here’s a base summary on the key differences in terms of features, functionality and or capabilities:
Aspect | Unmanaged Switch | Layer 2 Managed Switch | Layer 3 Managed Switch |
|---|---|---|---|
Features | |||
Configuration & Control | None, fixed configuration | VLANs, SPAN, QoS | Full control, port mirroring, VLANs, SPAN, QoS, Routing, ACLs |
Network Segmentation | No | Yes (within VLANs) | Yes (inter-VLAN routing) |
Traffic Monitoring (SPAN) | No | Yes | Yes |
Security Controls | None | Limited | Advanced (port security, authentication, ACLs, routing policies) |
Network Visibility | No visibility | monitoring and diagnostics | Comprehensive monitoring and diagnostics |
Traffic Management | No traffic management | Prioritization, traffic shaping | |
Physical Environment Suitability | Limited (depends on model) | Industrial-grade options available | Industrial-grade options available |
Remote Management | Not supported | Supported | Supported |
Redundancy & Failover | Not supported | Supported (STP, RSTP) | Supported (STP, RSTP) |
Cost | Lower cost | Higher upfront and operational cost | Higher upfront and operational cost |
Complexity | Simple plug-and-play | Requires switching skills for setup and ongoing management | Requires skilled setup and ongoing management |
Suitability | Large, complex, secure, and critical OT networks | Small, simple, low-risk networks | Cross-zone routing, large plants |
Risk Level | High | Moderate | Low (with proper configuration) |
Use Case Comparison and Recommendations
Use Case / Network Size | Managed Industrial Switches | Unmanaged Industrial Switches |
|---|---|---|
Large, complex OT networks | Essential for segmentation, security, monitoring, and remote management | Not suitable due to lack of control and visibility |
Critical production control systems | Required to ensure uptime, security, and deterministic traffic handling | Not recommended due to risk of downtime and attacks |
Small, simple or temporary setups | May be overkill and cost-prohibitive | Suitable for basic connectivity and low-risk segments |
Environments requiring compliance | Needed to meet ISA/IEC 62443 and other industrial cybersecurity standards | Insufficient for compliance and security requirements |
Networks requiring remote management | Enables remote troubleshooting and configuration | No remote management capabilities |
Risks & Risks Mitigation for unmanaged switches
Below are a list of potential risks using unmanaged switches.
Unauthorized network access via physical ports: Unmanaged switches cannot restrict or disable ports, so anyone with physical access can plug in a device (e.g., a laptop or rogue Wi-FI) and gain network access, potentially bypassing other security layers.
Man-in-the-Middle (MiTM) attacks: Unmanaged switches lack monitoring and control features, allowing attackers to intercept or alter communications between devices unnoticed, risking data theft and manipulation.
MAC spoofing and reconnaissance: Attackers can imitate legitimate MAC addresses to bypass security, and unmanaged switches provide no means to detect or prevent such spoofing activities.
Lack of traffic segmentation and visibility: Without VLANs or monitoring, unmanaged switches cannot isolate critical OT devices or provide network visibility, making it difficult to detect intrusions or contain threats.
Bypassing organizational defenses: A malicious device connected behind an unmanaged switch can create a hidden link to the internet or IT infrastructure, circumventing firewalls and other protections.
Increased risk despite physical security: Even in controlled environments like substations, physical security can be breached, and unmanaged switches offer no network-level controls to mitigate this risk.
In summary, unmanaged switches expose OT networks to unauthorized access, data interception, spoofing, and lack of network control, making them unsuitable for secure OT environments.
To mitigate risks (as listed above) associated with unmanaged switches in OT networks, consider these measures:
Physical security: Restrict physical access to switch locations to prevent unauthorized device connections, since unmanaged switches rely heavily on physical security.
Network segmentation: Use managed switches or routers to segment the network into VLANs, isolating critical OT devices from less secure areas, limiting lateral movement by attackers. Need extra caution not to disrupt operations, so careful planning is required.
Deploy managed switches where possible: Replace unmanaged switches with managed ones that support port security, VLANs, and access controls for better monitoring and control.
Monitoring and alerting: Implement network monitoring tools and intrusion detection systems to detect unusual traffic or unauthorized devices connected via unmanaged switches.
Disable unused ports: Where managed switches are used, disable unused ports to prevent unauthorized connections; for unmanaged switches, physically block or secure unused ports if possible.
Use network access control (NAC) and 802.1X authentication: Enforce device authentication before network access, reducing risk from rogue devices connected to unmanaged switches. Use caution: May not be feasible within the lower levels of OT zone.
Regular audits and vulnerability scanning: Continuously assess the network for unauthorized devices and vulnerabilities introduced by unmanaged switches. Use caution: do not use IT style scanning profiles and be selective on what traffic to send to what OT devices, use maintenance windows to perform such scans.
Backup and patch management: For managed devices, keep firmware updated and configurations backed up to reduce risks from known vulnerabilities.
In summary, while unmanaged switches lack inherent security features, risks can be reduced by strong physical security, network segmentation, monitoring, and gradually replacing unmanaged switches with managed ones for critical OT network segments.
Securing Things (sponsor)
🚨Manufacturers: Struggling to Protect Your IT & OT Systems?🚨
🚀 Start Your Cybersecurity Journey Today!🔒🚀Unlock Your Manufacturing Potential.
👉 Are you a small to medium-sized (local | regional | global) manufacturing operations and feeling overwhelmed by cybersecurity challenges?
👉 If tight budgets, limited resources, or skill gaps are holding you back from starting your Security Program journey or securing your operations, it's time to take action! 🔐💡
You're not alone—and we have the solution!
🌟 Introducing - Securing Things Cybersecurity Rapid Check (ST CRC)! 🌟
Designed just for 👉 you.
👉 Ideally suited for manufacturers with one or more plants, that have either never gone through an assessment before and or have done it ages ago.
👉 You don’t need a massive team or a huge budget.
👉 Imagine a tailored cybersecurity program that fits your unique needs without breaking the budget.
👉 Securing Things' Cybersecurity Rapid Check (ST CRC) can be conducted remotely, with onsite support from your trusted plant floor team.
Do-IT-With-You:
With remote guidance and on-site support from your plant floor personnel, we’ll help you:
✅ Identify/discover business inventory across the stack
✅ Pinpoint crown jewel assets, and potential vulnerabilities
✅ Identify quick wins - across people | process | technology
✅ Build a plan that fits your reality.
Yes we've been doing some of these for a while now - several sites have been done remotely.
Why Choose CRC?
👉 Cost-Effective: Get the insights you need without hefty investments.
👉 Expert Guidance: we work alongside your team to identify vulnerabilities and create a roadmap for improvement.
👉 Quick Turnaround: It’s fast, efficient, and doesn't break the bank. Gain actionable insights quickly, enabling you to bolster your defenses swiftly.
Empower your manufacturing operation with the knowledge and tools to protect against threats.
🔧 Take the First Step Towards a Secure Future! Don’t let cybersecurity concerns hold you back. Get ahead of cyber threats without the headache!
👉 DM or contact us to schedule your Cybersecurity Strategy session and get started!
Secure your manufacturing future without disrupting production operations!
✅ Book Early! For finding available bookings - DM or Contact us at
👉 info[@]securingthings[.]com or newsletter[@]securingthings[.]com!
It's a great day to start 🔒🚀Securing Things for your Digital Factory 🔒🚀
Few Updates (Sharing and Conference)
My thoughts along with leading experts, Mike & Tim, was published - here.
It was good to participate in any conference after a very long time at-least virtually, and also got the chance to present Industrial Cyber Days for Manufacturing for US time zone → US. (the last time I was in any conference in person was in Nov. 2019 in Malaysia).
Am running the same presentation in EMEA and APAC - register for your respective region below:
Title of my talk is → “Securing the Digital Factory: Lessons from the Field on Security Challenges from Industry 3.0 to 4.0 and Beyond”.
This session explores the challenges of securing manufacturing operations during the transition from Industry 3.0 to Industry 4.0. Drawing from experiences across three different manufacturers, the discussion highlights the limitations of traditional security approaches and their applicability in modern manufacturing environments that incorporate UNS and IIoT-based architectures.
Additionally, this session serves as a mini-course introduction to the Securing Things IT-OT CySEAT (Cyber Security Education and Transformation) program, providing insights into securing digital factories.
Key Learning Objectives:
Understanding Industry 4.0, the manufacturing lifecycle, automation stack, and digital transformation Exploring secure UNS-based architecture and the lack of industry-specific security guidance. Developing a strategic approach for securing the digital factory.
If you haven’t checked out yet - do join IT-OT CySEAT waiting List before the launch discount closes.
What’s coming?
Beside the below, I am excited to work with 2 guest writers to publish some upcoming newsletter versions. More on this in the next edition.
I have been juggling with few things lately, in addition to newsletters publishing, social posts/interactions, some volunteering time, and trying to wrap up few project assignments while figuring out what’s next later in store for me in Q2/Q3.
Have been working on few upcoming Part 3 of The Digital Factory series:
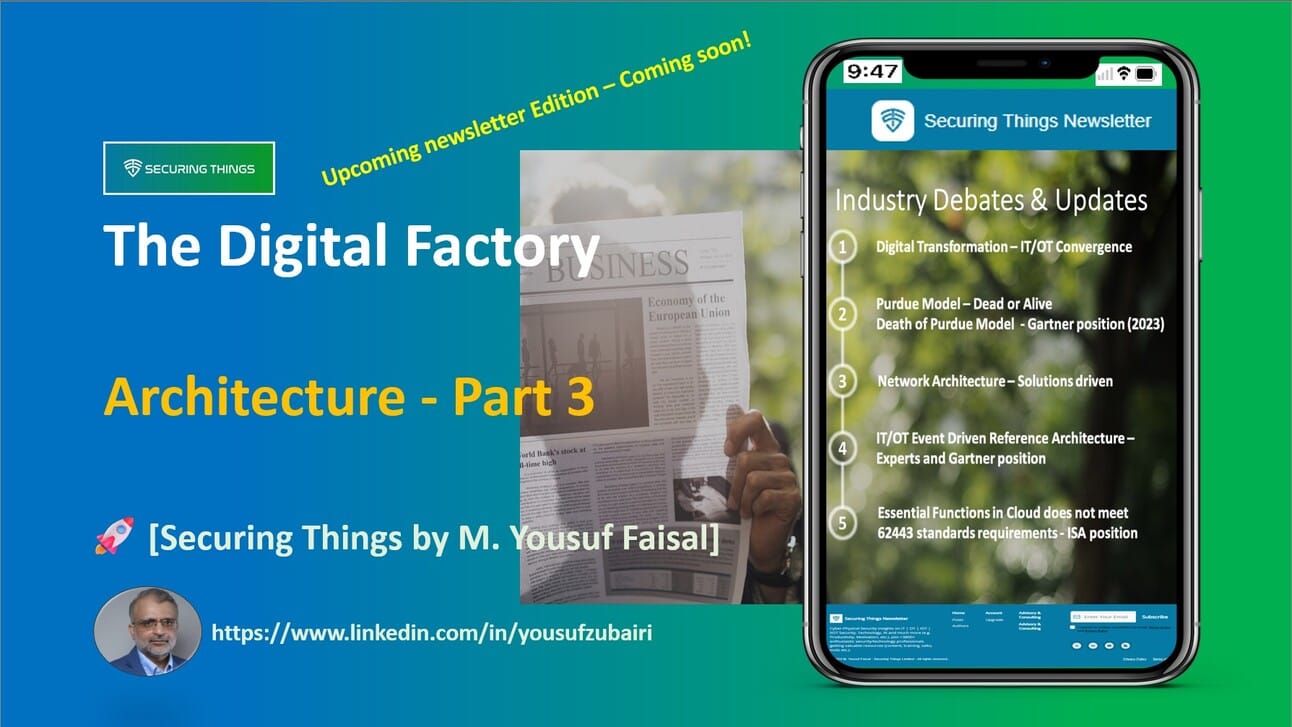
ST Newsletter coming soon!
Call 🤙 out to all OT/ICS experts out here 📢
I need your input - on "Industry Debates and Updates in/ OT / ICS - The Digital Factory - Architecture - Part 3"! 🗞️
In my upcoming newsletter edition, I'm trying to cover few industry debates;
👉 Digital Transformation - a project or a strategy?
👉 IT/OT Convergence - is it or is it not converging? :-p
👉 Purdue Model – Dead or Alive? | For Security or no Security?!
👉 🙋♂️ any other suggestions?
and few Industry updates: (well not so known but not new)
👉 Death of Purdue Model - Gartner position (2023)
👉 Network Architecture – Solutions driven
👉 IT/OT Event Driven Reference Architecture –
👉 62443 standards requirements for Cloud - ISA's position
💁♂️ 💁♀️ I've got some references to interesting debates from socials (LinkedIn) but want to see if you guys have some spicy ones at your disposal that you can share.
Also, if you want to contribute? ✍ send me a DM 📥 / drop a comment👇
Will add yours with attribution and a shout out! 📢
♻️ if you know someone be interested.
Thanks 🌟
My Recent Most Viewed Social Posts
In case you’ve missed - here are some of my recent most viewed social posts.
📰 [ST # 62] ✅Cybersecurity Insights from Q1 2025 - ✅ IT, OT, AI Cybersecurity Market Insights, M&As, Incidents, breaches, ransomware, threats and changing regulatory landscape🚀 [Securing Things by M. Yousuf Faisal]
📰 [ST # 61] ✅My list of IT-OT & Cybersecurity, Leadership, Productivity, Personal Development, and Money/Business books - must read for Cyber Leaders and Practitioners. Few updates on OT Security conference, & more.🚀 [Securing Things by M. Yousuf Faisal] 📰
📢 [ST #60] All Series Index - Securing Things 📢✅IT, OT & AI Cybersecurity – Program, Digital Factory, Guides, Standards, Crash Courses, Quarterly Insights & more.🚀 [Securing Things by M. Yousuf Faisal] 🗞️🗞️🗞️
Cybersecurity and AI Across the Industrial Automation Stack - Monthly Digest # 1 - ✅ Industry Trends, Market Insights on cybersecurity and AI across the layers of industrial automation stack (Cloud, ERP, DMZ, MES, SCADA, HMI, PLC/Edge), physical devices & more.🚀 [Securing Things by M. Yousuf Faisal].
ISA/IEC 62443 Standards - Part 5 - Security Program Elements (SPEs) for 62443-2-1:2024, Upcoming Asset Owner ACS Security Assurance (ACSSA) Certification Scheme to ISA/IEC 62443-2-1, 2-4, 3-2, 3-3 by ISCI, CISO's role, other interesting reads.
The Digital Factory (Data Flow) - Part 2 Industry 4.0 data/event driven data flows and security considerations and how's CISO's role is evolved in OT security.
Cybersecurity & Data Privacy for Hong Kong - HK Cybersecurity Market, upcoming Critical Infrastructure Bill 2024 regulations, Data Privacy Program Core elements, HK markets and more.
Ways in which I can help?
Whenever you are ready - I can help you with:
A - IT & OT Cybersecurity Advisory / Consulting services - for securing your business and or its digital transformation journey.
B - Security Awareness Training & Phishing Awareness Portal - Train your staff and build a Security awareness program through our subscription based service.
C - Securing Things Academy (STA) - Security trainings for IT & OT practitioners.
Visit the newsletter website for Links to above services and or reach out at info[at]securingthings[dot]com or DM me via LinkedIn.
D - Securing Things Newsletter - Sponsor this newsletter to showcase your brand globally, or subscribe to simply Get Smarter at Securing Things.
Reach out at newsletter[at]securingthings[dot]com or DM me via LinkedIn.
✉️ Wrapping Up
Have questions, comments, or feedback? Just reply directly, I’d love to hear from you.
Also, if you find this or previous newsletter edition(s) useful and know other people who would too, I'd really appreciate if you'd forward it to them. Thanks a ton.
Thanks for reading - until the next edition!
It’s a Great Day to Start Securing Things for a Smart & Safer Society.
Take care and Best Regards,
Rate the newsletter content
If you are reading this online don’t forget to register; validate your email, and request a login link to submit the poll.
Your feedback and input is invaluable to me as we work together to strengthen our cybersecurity defenses and create a safer and smarter digital society. Thank you for your trust and continued support.



