Disclaimer: All views presented here, in this newsletter, are my own.
Author or the newsletter are not liable for any actions taken by any individual or any organization / business / entity. The information provided is for education and awareness purposes only and is not specific to any business and or situation.
Table of Contents
Hi Securing Things Community,
📢 Welcome to ITDR (Identity Threat Detection & Response) crash course! 🛡️
If you've ever been curious about what the heck is ITDR and or if you are reading about it the first time, then you are in the right place. It could be misinterpreted with other terminologies that we’ve been used to, as evident from my LinkedIn Poll. Almost 50% guessed it right, while rest got it wrong and mixed it with other terminologies that we’ve been used to hearing.
In this newsletter, I'll cover ITDR's background, foundational concepts, and its role in identity security, IAM, and cybersecurity. Will outline its relation to XDR, industry insights, key software vendors, and provide reference materials. Additionally, I'll share some of my academy initiatives updates, popular social media posts, ways I can assist, and requests.
Special Message:
Before we begin, do me a favour and make sure you hit the “Subscribe” button to let me know that you care and keep me motivated to publish more. Thanks!
Securing Things Academy: (coming soon)
IT & OT CySEAT (Cyber Security Education And Transformation) course is designed for IT and OT cybersecurity practitioners. Join the wait-list → here.
Checkout a brief overview below:
What is ITDR?
ITDR (Identity Threat Detection and Response) is a specialised category or an approach within cybersecurity, that focuses on and or designed to detect, identify, detect and respond to threats targeting identities (whether humans identities or non-human identities i.e. machines). It encompasses tools and best practices that enhance existing Identity Access Management (IAM) systems by adding detection and response capabilities. ITDR aims to provide comprehensive visibility into identity-related threats across hybrid and multi-cloud environments, ensuring rapid response to potential breaches.
Gartner, which first defined ITDR in 2021, views it as distinct cybersecurity category and a necessary evolution to address gaps left by IAM (identity and access management) and PAM (privilege access management) solutions, in order to combat advanced identity-based threats in increasingly hybrid and distributed environments.
Expert Insight: “ITDR is not just a tool; it’s a paradigm shift. It empowers organizations to respond faster and more effectively to identity-based attacks.” – CISO, Fortune 500 Company.
Security Issues: Why is ITDR important?
The rise of identity-related breaches like the most famous ones in 2024 are, Snowflake data breach, Cloudflare, Hugging face and AWS breaches, highlighting the vulnerabilities and limitations in traditional identity management systems. Attackers do prioritise credential theft over exploiting hardware vulnerabilities.
Addresses an essential controls gap: ITDR have the potential to solve problems that are currently unsolvable by other IAM, PAM and XDR solutions due to their different focus and functionality.
Stay updated on Cybersecurity of Things with specialized content, industry insights, career guidance, best practices, market analysis, tools, and training to enhance your skills for a smarter, safer society!
ITDR Explained
Here's a quick crash course on ITDR, covering its fundamental concepts, role in identity security solutions, and key differences. This guide provides all the essentials for those curious or eager to learn more.
Background and Introduction to ITDR
Goal: Understand the origins of ITDR, threat landscape that creates the demand and how it differs from XDR solutions.
The cybersecurity landscape is constantly evolving, with identity threats increasing as attackers target identities to bypass defenses. ITDR has become crucial in combating these challenges, especially as organizations adopt zero trust and identity-centric strategies.
Identity Security Ecosystem & ITDR play
Goal: Understand how and where ITDR positioning is within the broader Identity security ecosystem.
Identities can be divided into 2 types:
Human Identities (HI) - our digital identities. Can be internal or external to organization.
Non-Human Identities (NHI) - machine related (processes, services or devices). These are all over the place, everywhere, in our workloads, devices, CI/CD pipelines, on-prem or cloud infrastructure, SaaS, code, our IOT, M2M, RPA and more.

Source: Cyberhut
Several terms we need to be familiar with and their roles within identity security solution ecosystem per the diagram below:
IAM (Identity Access Management) = solutions focused on providing access control and management of identities in real-time for access to applications and data through user authentication, authorization and accounting.
CIAM (Customer Identity & Access Management) = Same as above, but more focused on external users, citizens, consumers, customers and or guest access control.
PAM (Privilege Access Management) = solutions that protects privileged accounts with administrative rights or extensive access across an enterprise.
IGA (Identity Governance & Administration) = solutions responsible for aggregating and managing digital identities, roles and access rights across enterprise systems.
In an industrial environment, these HI and NHIs exists at each layer of industrial automation stack from cloud to the factory floor. Part of the above solutions also operate at all layers as well. However, some of these solutions are more commonly used across cloud and enterprise layers and or in case of CIAM for serving external customers only.
Solutions like ITDR are important for the cloud and enterprise levels, but they are not commonly used in the lower levels of automation, except in a few advanced settings (which I haven't personally seen). However, as industries move towards Industry 4.0 and beyond, we will likely see these solutions being adopted as part of cybersecurity programs with advance maturity levels.
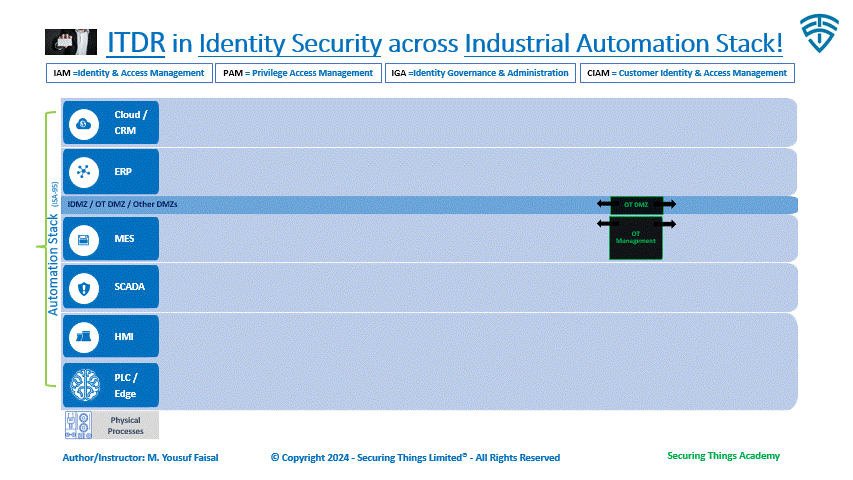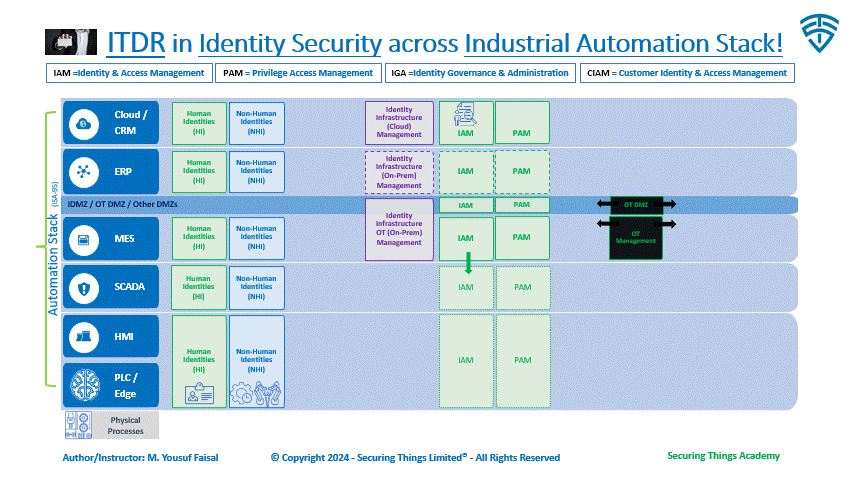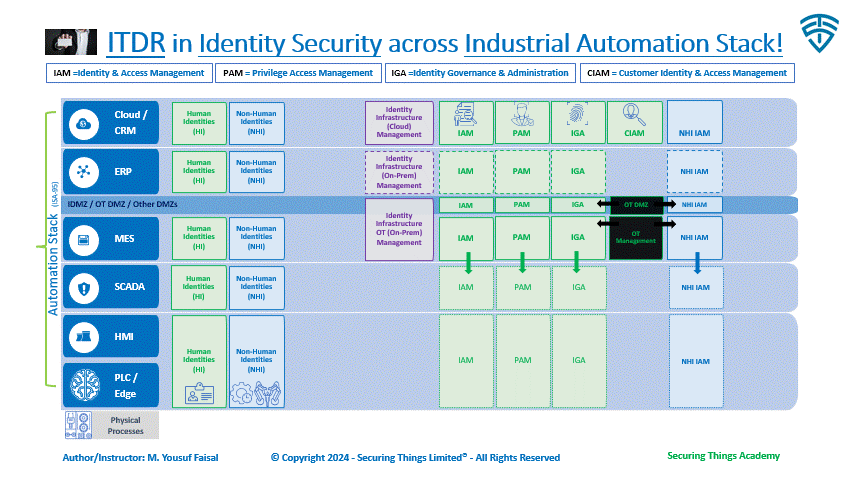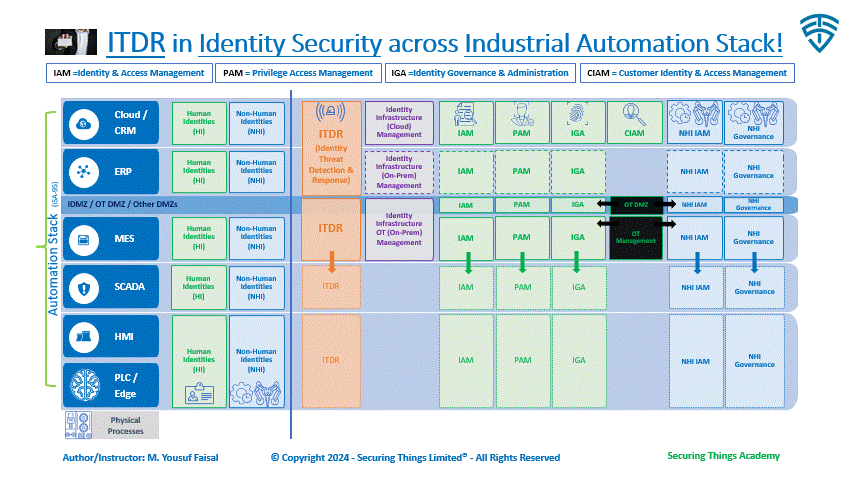
ITDR within Identity Security across Industrial Environments
ITDR fits into the broader cybersecurity ecosystem as part of a defense-in-depth strategy. It serves as an additional layer of security that complements IAM solutions like PAM and IGA. By focusing on identity-centric threats, ITDR enhances an organization's overall security posture within a Zero Trust framework.
With drive towards Zero Trust, we’d likely going to see more adoption on the industrial side as well.
Securing Things (Sponsor)
OT CBPRS (Cybersecurity Best Practices Requirements Specification) Toolkit!
The Solution (For Asset Owners Only) - Toolkit to get a head start for your OT/ICS Cybersecurity journey for SMB/SME industrial environment. Bonus - comes with limited complimentary seats for IT & OT CySEAT offering.
Below is a brief walkthrough on the OT-CBPRS toolkit:
(Note: Next iteration would include the ISA/IEC 62443-2-1 Security Program related requirements).
Note: I might update this or add more information to this in future versions.
Continue to read more on this after subscribing below.
Read more about ITDR → from Industry analyst perspective, cyber threats driving its needs with example of attack scenarios and ITDR mechanism on addressing them, real-world use cases, capabilities, comparison between ITDR vs. EDR vs. XDR, ITDR vendor insights etc.
ITDR from industry analysts perspective
Goal: Discover the real-world applications and industries that will benefit from ITDR.
Definition by Analysts - Gartner defines ITDR as a necessary evolution in cybersecurity that addresses the growing risk associated with identity attacks. Other analysts emphasize its role in complementing IAM systems by providing deeper insights into user behavior and access patterns, thus enabling organizations to proactively mitigate risks associated with compromised identities
Cyber Threats driving need to ITDR
Goal: Understand the key security benefits ITDR provides and the potential solutions.
ITDR specializes in detecting a variety of identity-based threats that pose significant risks to organizations. Here are the specific types of threats that ITDR is designed to identify and mitigate:
Attack Types / Scenario | ITDR Mechanism |
|---|---|
Account Takeover Attacks Description: Cyber criminals gain unauthorized access to user accounts, often using stolen credentials. | Keeps an eye on user activity for anything unusual, like logging in from new places or devices, and can automatically lock accounts if they seem to be taken over. |
Phishing Attacks Description: Attackers use deceptive emails or messages to trick users into providing sensitive information, such as login credentials. | can analyze email traffic and user interactions to identify and quarantine phishing attempts before they reach the target. |
Insider Threats Description: Employees or contractors misuse their access privileges to steal data or commit fraud. | keeps an eye on user actions to spot unusual activities, like accessing important data in unexpected ways, so we can step in early. |
Credential Misuse Description: This includes the use of stolen or compromised credentials to access systems without authorization. | uses behavioural analysis to spot unusual activity and identify possible misuse of login details. |
Privilege Escalation Description: Attackers exploit vulnerabilities to gain elevated access rights within a system. | Monitors changes in user permissions and notifies security teams if an account unexpectedly gets access to important resources that it usually doesn't use. |
MFA Bombing Description: Attackers try to get around multi-factor authentication by sending (bombarding) the victim with a lot of simultaneous login requests. | Can spot signs of MFA bombing attempts and react by either temporarily locking accounts or warning users. |
Ransomware and Data Exfiltration Description: These attacks might not only focus on identities, but they often use hacked accounts to start the attack. | Can detect unusual data access patterns that may indicate an attempt to exfiltrate sensitive information or deploy ransomware. |
According to NIST below outlines the impact of ITDR to common identity based attacks.
ITDR Real-World Use Case Examples
Use Case | Scenario | ITDR In Action |
|---|---|---|
Detecting Insider Threats | A trusted employee’s credentials are compromised, leading to unauthorized access to sensitive systems. | - Behavioural analytics identifies anomalies in login patterns (e.g., unusual time or location). - Automated policies trigger an alert and block the account. - Integration with PAM ensures no escalation to privileged accounts. |
Mitigating Credential Theft | A phishing attack compromises a C-level executive’s email credentials. | - AI detects login from an unrecognized device or suspicious IP address. - Multi-factor authentication (MFA) re-prompt prevents access. - Incident response tools disable access and alert the security team. |
Preventing Lateral Movement. | Attackers use stolen credentials to move between systems undetected. | - ITDR monitors abnormal lateral access attempts across multiple systems. - Threat hunting identifies the root cause and isolates affected endpoints. - Logs are sent to SIEM for correlation with other threat vectors. |
Enhancing Zero Trust Implementation. | A manufacturing company deploys a zero trust framework but struggles with identity verification at scale. | - Continuously validates user identities with behavioural monitoring. - Automates identity governance workflows for compliance. - Ensures only verified identities access sensitive OT environments. |
ITDR Capabilities / Functionalities
Goal: Learn about the capabilities ITDR offers to withstand identity based attacks.
Threat Detection: By using information from IAM and PAM systems, ITDR can spot many types of identity attacks, like Identify suspicious login attempts, account takeover, lateral movements, privilege escalations and spot anomalies in identity usage. It achieves this by examining login tries, access habits, and changes in settings as they happen.
Behavioural Analytics: Track and baseline user behaviours & activities to detect deviations. Uses machine learning and user behavior analysis to understand what normal activity looks like for users. If something unusual happens, like logging in at a strange time or place, ITDR can send alerts for further checking.
Automated Response: Enable real-time containment and automate remediation of identity threats by integrating with incident response frameworks. For example, if an anomaly is detected, ITDR can initiate workflows that might include temporarily revoking access or escalating the issue to security analysts for further review.
Integration: Works alongside IAM, PAM, IGA systems and security orchestration tools for end-to-end coverage. This’ll provide following benefits:
improved security posture by enhancing the overall security framework by closing gaps that traditional systems might leave open. This is particularly important in environments utilizing cloud services where identity risks are more pronounced due to shared security models.
continuous monitoring of user activities across various platforms (cloud services, on-premises systems) for signs of suspicious behavior, thereby reducing the attack surface available to potential intruders.
proactive risk management by identifying misconfigurations and excessive permissions early on, organizations can proactively manage risks associated with identity threats before they lead to significant breaches or incidents.
ITDR vs. EDR and XDR
ITDR is often compared to Extended Detection and Response (XDR), but there are key distinctions:
Features | ITDR | EDR | XDR |
|---|---|---|---|
Primary Focus | User identities and access management | Endpoint activities | Cross-domain security incidents |
Data Collection | User activity logs, authentication patterns | System logs, file access | Data from endpoints, networks, cloud |
Type of Analysis | Behavioral analysis focused on identities | Behavioral analysis focused on endpoints | Correlates behaviours across multiple layers |
Anomaly Detection | Identifies deviations in user behavior | Detects suspicious endpoint activities | Identifies complex attack patterns |
Response Mechanism | Identity-focused incident response | Endpoint isolation and malware removal | Unified response across security domains |
In summary, ITDR is all about analyzing user behavior to find identity-based threats. On the other hand, EDR and XDR focus more on protecting devices and providing a wide view across different areas. Understanding this difference is crucial for organizations that want a strong cybersecurity strategy to handle both device weaknesses and identity risks.
ITDR Vendors and Market Insights
The ITDR market accelerated in 2024. With Cisco and Delinea, entering this space, acquiring Oort and Authomize, respectively and cybersecurity solution leaders like BeyondTrust, CrowdStrike, and SentinelOne are heavily investing in ITDR. Microsoft is also continuing to enhance ITDR capabilities by merging features from its Entra and Defender XDR product offerings. Other providers like Gurucul, Securonix, and Sharelock are also innovating and redefining ITDR.

Source: Microsoft ITDR Strategy
Conclusion:
For CISOs designing strategy, architects aligning tools, and engineers deploying systems, ITDR offers a proactive approach to securing identities. Attackers are evolving—so must we. Equip yourself with ITDR knowledge, latest approaches and the tools to stay ahead.
Exploring identity-related threats and securing them with an ITDR approach is a fascinating journey. This carefully crafted learning path is here to help you grasp the basics of ITDR, discover its potential applications and use cases, understand the security risks it tackles, and see how it fits into a comprehensive cybersecurity resilience strategy. Whether you're just starting out or have years of experience, these resources are designed to provide you with valuable insights and keep you ahead in the world of identity threat detection and response.
What are your best reads? videos? courses? - do type in comments below and enrich this resource.
My Recent Most Viewed Social Posts:
In case you’ve missed - here are some of my recent most viewed social posts.
IT & OT/ICS Cybersecurity Policy(/ies) - Deciding on the Policy Route for your industrial environments.
Digital Manufacturing at Risk - Start with Cybersecurity and Digital Transformation Maturity Assessment Reviews Now!
Cybersecurity (IT, OT/ICS, AI, Open source) - Insights from Q3 2024 [Securing Things by M. Yousuf Faisal]
Quantum Computing Cybersecurity Crash Course - the Future Security Concerns.
"Boost Your Defense Game - IT & OT/ICS Cybersecurity Training [Securing Things by M. Yousuf Faisal]"
IT & OT/ICS CySEAT - only on Securing Things Academy (40% off) - Training course brief introduction.
Getting OT/ICS visibility for industrial, data centre or smart buildings environments.
IT & OT Security Dozen framework for building, executing & managing a Cybersecurity & Resilience Transformation Program.
Ways in which I can help?
Whenever you are ready - I can help you / your organization / your customers with:
A - IT & OT Cybersecurity Advisory / Consulting services - for securing your organisation’s or client’s digital transformation journey.
B - Security Awareness Training & Phishing Awareness Portal - Train your staff.
C - Securing Things Academy (STA) - Security trainings for IT & OT practitioners.
D - Securing Things Newsletter - Get your brand (personal / business) in front of global audience by sponsoring this newsletter. And or simply subscribe to Get smarter at Securing Things.
Reach out at info[at]securingthings[dot]com or DM me via LinkedIn.
My Ask
I invite #SecuringThings community to share their feedback.
Your feedback and input is invaluable to me as we work together to strengthen our cybersecurity defenses and create a safer and smarter digital society. Thank you for your trust and continued support.
Do register, validate your email, and request login link to submit poll to be able to enter a chance to win a future course giveaway.
Rate the newsletter content
Thanks for reading - until the next edition!
It’s a Great Day to Start Securing Things for a Smart & Safer Society.
Take care and Best Regards,
M. Yousuf Faisal. (Advice | Consult Cyber & business leaders in their journey on Securing Things (IT, OT/ICS, IIOT, digital transformation, Industry 4.0, & AI) & share everything I learn on this Newsletter | and upcoming Academy).
The Newsletter Platform Built for Growth
When starting a newsletter, there are plenty of choices. But there’s only one publishing tool built to help you grow your publications as quickly and sustainably as possible.
Beehiiv was founded by some of the earliest employees of the Morning Brew, and they know what it takes to grow a newsletter from zero to millions.
The all-in-one publishing suite comes with built-in growth tools, customization, and best-in-class analytics that actually move the needle - all in an easy-to-use interface.
Not to mention—responsive audience polls, a custom referral program, SEO-optimized webpage’s, and so much more.
If you’ve considered starting a newsletter, there’s no better place to get started and no better time than now.


