Endpoint Detection & Response (EDR) Solutions for IT & OT/ICS
Disclaimer: All views presented here, in this newsletter, are my own.
Author or the newsletter are not liable for any actions taken by any individual or any organization / business / entity. The information provided is for education and awareness and is not specific to any business or situation.
Table of Contents
Introduction
Endpoint Detection and Response (EDR) solution, in addition to an essential security controls within an enterprise/IT on endpoints (servers, laptops, desktops), are now becoming also a critical need for securing endpoints within the critical infrastructure Operational Technology (OT) / industrial Control systems ICS environments, to provide adequate protection against growing and sophisticated cyber threats like Ransomware and other forms of malware or malware-less attacks on the IT, OT/ICS or factory or automation or production control networks (all these terms are used).
However, implementing such EDR solution requires careful planning and execution to avoid any downtime or disruptions both to enterprise applications environment (in IT) and to production operations (in OT/ICS).
Caution: Such projects are heavy in terms of time and resource requirements, lots of planning, coordination, discovery, getting multiple approvals, as well as Pre & Post deployment related administrative and technical activities. Note: EDR solutions are not like Endpoint protection solutions which uses antivirus features, inspection of files for corruption, or analyse for suspicious behaviour, against known signatures database, detect, and prevent mostly known attacks. EDR solutions uses (typically cloud based) Machine Learning (ML), Artificial intelligence (AI), behaviour analytics and threat intelligence (TI) to detect threats and take the additional step of acting to eradicate threats and neutralize existing attacks by actively blocking and or isolating endpoints.
Threat Landscape & Business Needs
Ransomware attacks have surged since last few years and 2023 is no exceptions, rather seen a rise in such attacks. We've all seen some significant supply chain disruptions due to global ransomware attacks on small to large enterprise organizations. One (of the many) very recent example is highlighted below:
Businesses wants to minimize the number of endpoint security control solutions deployed for ease of management and for minimizing the impact on performance (especially the number of agents running on any given endpoint) and ultimately the production environment. The typical control requirements from such solutions are (but not limited to):
Note: cloud native/containers and other special purpose endpoint detection and response controls may exists (/need to have) as well - (not included here).
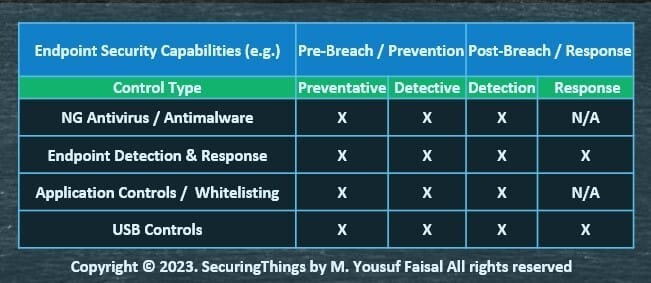
Pre/Post Breach Endpoint Security Solutions Capabilities/Use case needs
A Critical Telemetry source
EDR solutions are at the heart of, and one of the main, telemetry / log source (critical) as part of any broader XDR/MDR cyber-security monitoring strategy.
EDR Solution Selection:
Feature comparison
Mapping your business requirements both in IT and OT ensures that required telemetry is provided by your selected EDR tool is a required activity. This can be achieved using feature comparison and requirements analysis and or running a Proof of Concept exercise. Industry analyst reports could be another source for understanding products capabilities, strengths/weaknesses and company direction.
Another useful/interesting GitHub project by @kostastsale @ateixei to keep tabs on for reference is:
IT/OT EDR Project Execution Strategy
For details on executing such complex deployment or implementation projects, both in IT & OT/ICS environments please refer to #SecuringThings whitepaper by M. Yousuf Faisal here:
Documentation
Documentation of such implementation is critical, both in terms of guidance for IT users and Plant Users as well as guidance for implementation, back-end operations and maintenance teams (e.g., or plant project engineering team).

Example IT & OT EDR Deployment & Maintenance Guide Document
Relying on EDRs only
EDR solutions are one part of an IT & OT/ICS environments defense-in-depth layered model and not an all protection/detection solutions for all your cybersecurity needs. Solely relying on EDRs will expose your IT & OT environments for potential bypass/tampers and related attacks of such EDR solutions. Few reference examples below:
A good write-up for a story about tempering EDRs here by Daniel Feichter from redops--> A story about tampering EDRs - RedOps - English
Lessons Learned (an actual implementation)
Below outlines few key examples of potential outcomes/benefits and Pitfalls/Don'ts from an actual global IT/OT EDR implementation.

Example list of Benefits/Outcomes & Pitfalls from IT/OT EDR Implementations
Feel free to reach out or get in touch at info[@]securingthings[dot]com for any business needs, project support, discussions and or simply information sharing.
Securing Things Academy:
IT & OT CySEAT (Cyber Security Education And Transformation) course is designed for IT and OT cybersecurity practitioners. Join the wait-list → here.
Checkout a brief overview below:
Ways in which I can help?
Whenever you are ready - I can help you with:
A - IT & OT Cybersecurity Advisory / Consulting services - for securing your business and or its digital transformation journey.
B - Security Awareness Training & Phishing Awareness Portal - Train your staff and build a Security awareness progsubscription based service.
C - Securing Things Academy (STA) - Security trainings for IT & OT practitioners.
Visit the newsletter website for Links to above services and or reach out at info[at]securingthings[dot]com or DM me via LinkedIn.
D - Securing Things Newsletter - Sponsor this newsletter to showcase your brand globally, or subscribe to simply Get Smarter at Securing Things.
Reach out at newsletter[at]securingthings[dot]com or DM me via LinkedIn.
How are we doing?
I invite you as part of #SecuringThings community to share your feedback.
Rate the newsletter content
Your feedback and input is invaluable to me as we work together to strengthen our cybersecurity defenses and create a safer and smarter digital society.
Let us know how we can improve this and or what you’d like to see in future?
Thank you for your trust and continued support.
Do register, validate your email, and request login link to submit poll to be able to enter a chance to win a future course giveaway.
Thanks for reading - until the next edition!
It’s a Great Day to Start Securing Things for a Smart & Safer Society.
Take care and Best Regards,
M. Yousuf Faisal. (Advice | Consult Cyber & business leaders in their journey on Securing Things (IT, OT/ICS, IIOT, digital transformation, Industry 4.0, & AI) & share everything I learn on this Newsletter | and upcoming Academy).
The Newsletter Platform Built for Growth
When starting a newsletter, there are plenty of choices. But there’s only one publishing tool built to help you grow your publications as quickly and sustainably as possible.
beehiiv was founded by some of the earliest employees of the Morning Brew, annow what it takes to grow a newsletter from zero to millions.
The all-in-one publishing suite comes with built-in growth tools, customization, and best-in-clanals that actually move the needle - all in an easy-to-use interface.
Not to mention—responsive audience polls, a custom referral program, SEO-optimized webpages, and so much more.
If you’ve considered starting a newsletter, there’s no better place to get started and no better time than now.