IT Cybersecurity Toolkit for Small/Medium Businesses
Disclaimer: All views presented here, in this newsletter, are my own.
Author or the newsletter are not liable for any actions taken by an individual or an organization / business / entity. The information provided is for education and awareness and is not specific to any business or situation.
Please note: Intent here is purely educational and is to simplify the journey (free style) and does not necessarily dictate detailed / exhaustive set of step-by-step activities. Let's make your next local SMBs/SMEs more secure.
Table of Contents
First things first - Accept Cybersecurity as a Business Risks
Let's face it - every industry has recognized cybersecurity as a business risk; discussed often now, as one of the major business concerns by top executives/board members (especially by businesses that are more technology dependent) and there's increased awareness. However, still, many are not advanced enough in their maturity roadmap or putting cybersecurity as a lower priority (either intentionally or unintentionally). To reinstate the importance, as an example, World Economic Forum (WEF) in their recent global risks report for 2023 (18th edition) - highlight #Cybersecurity #Cybercrime as one of the top 10 risks categories.
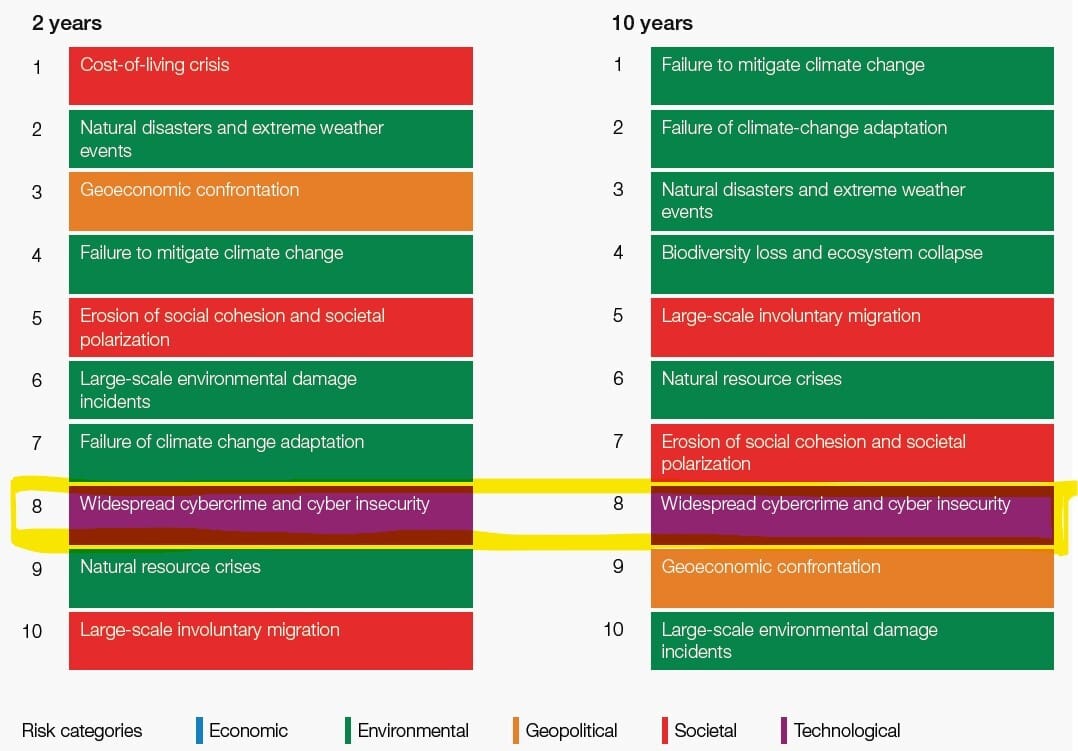
Source: World Economic Forum (WEF) Global Risk Report 2023
Technology will exacerbate inequalities while risks from cybersecurity will remain a constant concern. (Source: World Economic Forum (WEF) Global Risk Report 2023)
Also, in addition, see SecuringThings Cybersecurity SMB Toolkit slide # 2 & # 3.
Starting Cybersecurity Journey for your Business:
Start with using business related information at your disposal - business processes and data flows (follow your data). Identify and draw table for each key business process outlining - type of data handled (stored, processed or transmitted), mechanism used for data exchange between systems / business units / entities / partners / customers, sensitivity of data types/elements, risks around confidentiality, its integrity and availability needs. List any local or sector specific regulatory compliance requirements that is required to be adhered to. Understand the business goals and objectives; and from that lense, start building a plan of action.
Plan and Execute your Cybersecurity Journey
A general starting point is to identify a person, who will own cybersecurity responsibilities (in case of resource constraints; a non-technical business leader would need to assume this responsibility). Second step is to perform a business impact analysis (BIA) for your business environment and document your business risk thresholds; business leaders should answer - "what is the level of risk that is acceptable for my business?" - beyond which survival of the business would be at stake. Or else perform a cyber risk assessment / review.
Discuss & list (all possible activities across 5 stages outlined below) —> Agree —> Document —> Enforce —> Check —> Improve —> Rinse —> Repeat.
Stage 1 - Know What you've and Why You need to Protect it - IDENTIFY:
Start building a list of all major asset types. Define, agree, enforce a simple Data (Confidential | Private | Public) and Systems (Critical | Essential | Important | Others) Classification levels for your assets. Next step is to discover all possible asset types (both through automated and manual means).
People - Identify Cybersecurity Leader (CISO / vCISO / other security leader), formally assign responsibilities. Educate staff with continuous tips/alerts and regular awareness trainings. Use reward programs to encourage a cyber secure culture.
Process - Document Standards / Procedures for identify assets and risks - supporting goals listed out in Security policies and ensure clear/concise guidance for staff for support adherence to compliance.
Technology - Use tools to automate discovery of assets (hardware/software/data/web services), vulnerabilities, threats and risks and store all in central and secure repository (usually an Intranet portal or specialized tools e.g., vulnerability scans, asset management or CMD etc.).
See cybersecurity annual planner provided below for annual activities example within this stage. In addition, see SecuringThings Cybersecurity SMB Toolkit slide # 4.
Stage 2 - Know What and How you need to Protect it - PROTECT:
Identify, select and deploy protection controls (administrative and technical) across data, users, apps, devices, networks, and cloud).
People - Policies, procedures and awareness around Do's & Don'ts (both for general cybersecurity awareness and role-based trainings).
Process - Defined workflows, operational security guidelines (OSGs) (for each critical protection tool/solution) and procedures around the protective controls / tools employed.
Technology - Secure all layers of your technology stack - look for security solutions for digital realm (Cloud, Web, Email, Network, Endpoints and Data etc.) and physical world (printouts, office facility and equipment etc.).
See cybersecurity annual planner provided below for annual activities example within this stage. In addition, see SecuringThings Cybersecurity SMB Toolkit slide # 5.
Stage 3 - Know What's Happening within your Environment - DETECT:
Enable auditing and recording all key digital and physical activities across your business. Look at the retention needs for your local/regional/international regulatory requirements and plan for storing these logs. Build a mechanism for daily monitoring using internal or external resources. In addition, put a program in place to monitor contractual compliance of all suppliers (vendors, service providers, 3rd parties) that could impact the security of your business operations.
People - regularly (daily) monitor logs / activities by internal technical staff or external third-party service provider.
Process - Decouple/minimize false positives and false negatives to validate incidents using technology and expertise. Establish a supplier compliance monitoring program to manage suppliers related risks.
Technology - All key technology solution has built-in audit logging capabilities - use that. Once enabled, try collecting, centralizing logs in log management / SIEM solution (cloud based ideally), and perform daily/continuous monitoring using internal resources or a contracted 3rd party MSSP and or a combination of both.
See cybersecurity annual planner provided below for annual activities example within this stage. In addition, see SecuringThings Cybersecurity SMB Toolkit slide # 6.
Stage 4 - Know how to react to incidents - RESPOND:
Timely incident response (IR) is crucial to every business in order to minimize and contain damages cause by unwanted events/incidents.
People - reporting incidents (all staff/contractors), incident responders (IT / internal virtual IR team, and or IR SMEs from 3rd party consultants, service providers / MSSPs)
Process - Follow IR best practices: (a) prepare team, systems, & procedures; (b) identify security incidents; (c) containment (d) eradication of threats and possible recurrence options (e) recovery activities (f) record lessons learned, educate and improve IR efforts. Work towards minimizing Mean-time-to-Detect (MTTD) and Mean-time-to-Respond (MTTR).
Technology - Use detection, alerting and response solutions across your endpoints, networks & cloud environments.
See cybersecurity annual planner provided below for annual activities example within this stage. In addition, see SecuringThings Cybersecurity SMB Toolkit slide # 7.
Stage 5 - Know how to bring things back to normal operations - RECOVER:
It's all about being prepared for an unexpected / expected event/incident, where recovering from a disaster is inevitable. Without preparation and testing, you'll never be sure if the people (who are involved), technology (that is used) relied upon and processes (utilized) defined are effective in ensuring that business can resume normal operations. Therefore, ensure regular backups are made (ideally multiple copies using an industry wide best practice methodology known as the 3-2-1 rule) and are routinely tested for recovery.
People - Technical Team (IT department/sys admins, service providers/MS) and system owners and business users for verification.
Process - Backup & recovery procedures for each critical / essential system, while ensuring meeting SLAs, per agreed, recovery time objective (RTO) / recovery point objective (RPO). Perform tests and disaster recovery exercises.
Technology - backup solutions (on-prem or cloud based), native recovery commands, testing technology specific restoration procedures / backup data set.
See cybersecurity annual planner provided below for annual activities example within this stage. In addition, see SecuringThings Cybersecurity SMB Toolkit slide # 7.
Do we need to follow the above stage-wise sequence?
Perhaps - "not necessarily" - e.g., you may already have a backup solution and associated recovery process in place, while you have just identified/classified sensitive data and critical systems. However, this is a general sequence. Based on business priorities, hopefully agreed at the start of your cybersecurity journey; do whatever is practically possible (given business/technical constraints) simultaneously and or sequentially, to move towards the target maturity state.
In addition, see SecuringThings Cybersecurity SMB Toolkit slide # 5-to-7.
Recommendations & Key Takeaways
People - know that technical security is not everyone's responsibility - however, each individual staff, is a low hanging fruit (an attack path), so staying vigilant for potential cybersecurity threats and keeping business information secure must be everyone's goal and responsibility.
Process - technical staff and leadership to establish, document and update secure business processes regularly. While rest of the staff should adhere to such guidelines/procedures. Continue monitor and measure maturity and progress.
Technology - Keep it up to date, change all vendor defaults, follow secure guidelines (industry/vendor specific), don't set once and forget it. Practice regular reviews, testing and monitoring tools/solutions for optimal use. Where possible, automate and integrate.
Example - Annual Cybersecurity Activities Planner (with frequency):
Below is an example reference list (non-exhaustive) of annual cybersecurity activities (to be performed through-out the year) as an extension of SecuringThings Cybersecurity SMB Toolkit. Modify, expand & adjust according to your business needs.
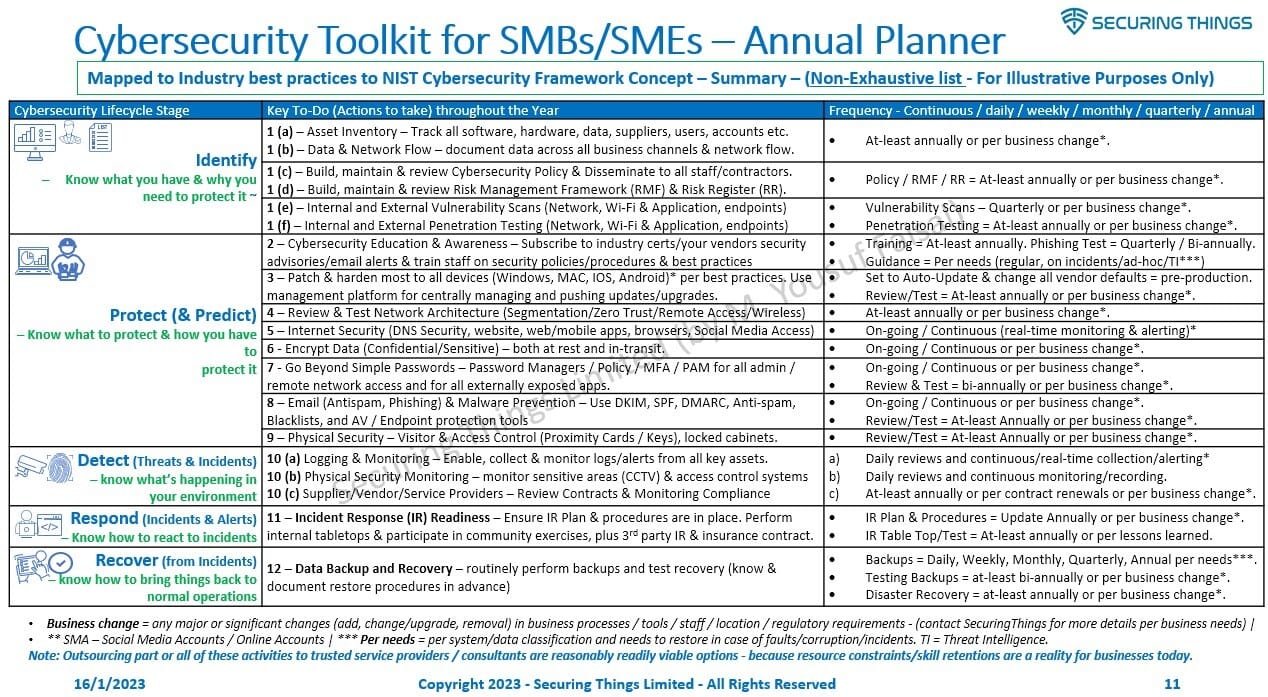
Securing Things - Cybersecurity Toolkit for SMBs (Small & Medium Businesses) / SMEs (Small & Medium Enterprises) - Annual Activity Planner Example
Resources At your Disposal
Internal & External Security SMEs (consultants, third-party service providers / MSS).
Free vendor neutral (regulatory / government / community) and vendor specific guidance,
Open source / commercial security tools/solutions across Identify, Detect, Respond, Recover stages. (Look for tool automation and integrated capabilities for scalability).
In addition, see SecuringThings Cybersecurity SMB Toolkit slide # 9 for links to few free resources to get you started.
EDUCATE --> EDUCATE --> EDUCATE --> TRANSFORM --> STAY ON THE PATH (consistency is key) --> an on-going journey and not an end goal.
Hey there 'my local small and medium business leaders, owners / operators and SMEs' - remember it's never too late - as always ---> It's a great day to start "Securing:Things".🙂
All the best for rest of 2023 & coming year 2024 - towards a Smart and Safer Society - one step at a time.
Take care. Love & Peace!
Ways in which I can help?
Whenever you are ready - I can help you with:
A - IT & OT Cybersecurity Advisory / Consulting services - for securing your business and or its digital transformation journey.
B - Security Awareness Training & Phishing Awareness Portal - Train your staff and build a Security awareness program through our subscription based service.
C - Securing Things Academy (STA) - Security trainings for IT & OT practitioners.
Visit the newsletter website for Links to above services and or reach out at info[at]securingthings[dot]com or DM me via LinkedIn.
D - Securing Things Newsletter - Sponsor this newsletter to showcase your brand globally, or subscribe to simply Get Smarter at Securing Things.
Reach out at newsletter[at]securingthings[dot]com or DM me via LinkedIn.
How are we doing?
I invite you as part of #SecuringThings community to share your feedback.
Rate the newsletter content
Your feedback and input is invaluable to me as we work together to strengthen our cybersecurity defenses and create a safer and smarter digital society.
Let us know how we can improve this and or what you’d like to see in future?
Thank you for your trust and continued support.
Do register, validate your email, and request login link to submit poll to be able to enter a chance to win a future course giveaway.
Thanks for reading - until the next edition!
It’s a Great Day to Start Securing Things for a Smart & Safer Society.
Take care and Best Regards,
M. Yousuf Faisal. (Advice | Consult Cyber & business leaders in their journey on Securing Things (IT, OT/ICS, IIOT, digital transformation, Industry 4.0, & AI) & share everything I learn on this Newsletter | and upcoming Academy).
The Newsletter Platform Built for Growth
When starting a newsletter, there are plenty of choices. But there’s only one publishing tool built to help you grow your publications as quickly and sustainably as possible.
beehiiv was founded by some of the earliest employees of the Morning Brew, and they know what it takes to grow a newsletter from zero to millions.
The all-in-one publishing suite comes with built-in growth tools, customization, and best-in-class analytics that actually move the needle - all in an easy-to-use interface.
Not to mention—responsive audience polls, a custom referral program, SEO-optimized webpages, and so much more.
If you’ve considered starting a newsletter, there’s no better place to get started and no better time than now.