Disclaimer: All views presented here, in this newsletter, are my own.
Author or the newsletter are not liable for any actions taken by any individual or any organization / business / entity. The information provided is for education and awareness purposes only and is not specific to any business and or situation.
Table of Contents
Welcome
Hey Securing Things Community,
I am taking a slightly different approach for this edition, i.e., instead of covering a single cybersecurity topic - this one is all about you, me and the cybersecurity industry - the ups and the downs - regardless of wherever we are in our professional or personal journey. I am sharing mine, and I’d love to read yours. Hope to see some in comments below as:
Big or small wins/achievements/progress
Setbacks and experiences - are all valuable lessons to help us grow
What’s in for 2024 - the plan and hope for something better.
I’ll also be covering few industry insights from 2023, and of course, “Transient Assets in OT/ICS”, as the topic of the day.
Stepping into the second month of 2024, I am thrilled to present the first newsletter of the year. Hope you’ve enjoyed what you’ve seen so far and it helped some of you in your professional / personal capacity. If you are new, I encourage you to take a look at the previous posts.
Reflecting on 2023 & aim for better 2024
On Professional Journey:
Small wins / achievements / progress - Despite feeling like things have progressed slow, much happened in 2023:
IT & OT Cybersecurity consulting gigs (big and small), bootstrapping Securing Things, made small progress (see few announcements below).
Joined global communities (e.g. ISASecure as supporting member, ISA, ICS, Cx forums, founders, mastermind & whatsapp groups).
Passed 5 exams, including #62443 Cybersecurity Expert certification from ISA and Nuclear Cybersecurity Professional certification.
Posted organic content throughout 2023, though challenging and time consuming (my respect for those that share knowledge online has grown 10x, kudos all). Also, gained 3500+ newsletter subscribers, 1000+ followers on Securing Things company LinkedIn page and 15.6K+ on my personal Linkedin (happy to connect) along the way.
Published guides & toolkits e.g. OTCBPRS (see announcement section below), IT/OT EDR Implementations, Cybersecurity toolkit for SMBs, DCom vulnerability etc.).
Attended GITEX Dubai 2023 conference (for the first time) - first and only professional event attended since Nov. 2019. Yeah i know it’s crazy!
House hunt and move - reminded me of a number things around project management (timing, risks, negotiations, expenses, people etc.) and indeed it’s a stressful feat.
Found some industry experts and got to know few of them (perhaps a separate post on that later).
Setbacks and experiences - 2023 was no short of a struggle as a professional and mostly as a new solopreneur. With occasional feelings of uncertainty and self-doubts, few lost opportunities, mistakes and errors along the way, I realized:
how difficult it is to sell, how little that I know; a humbling experience.
relying on personal contact list only, may not yield better results.
its challenging out there with shrinking client budgets (& or just the excuse of), deals getting delayed and in turn drying pipeline.
selling time do have its upsides, but more downsides, as one can’t scale and there’s high risks of burnout running multiple streams with almost no holidays, no weekends off for most part of 2023.
it can be time consuming for founders / solopreneurs to select the right technology stack and building systems and processes of business.
the need to get use to taking risks and making decisions on a daily basis.
being an introvert made this all even more challenging.
Looking forward to 2024: Setting ambitious goals
Wish to add value to many in their cybersecurity careers, through sharing knowledge and several businesses professionally.
Read at-least 5 books in 2024 (comment below to share your list).
Complete at-least 5 different courses/tracks (enrolled in few already).
Gain new and improve current skills (technical and professional skills).
Continue with the activities on below announcements.
Focus on finding and adding more value in all engagements.
build new connections and keeping up with old ones - am bad at both.
build new partnerships and participate in few groups/forums or tribes.
Find more time for self and family.
Do share yours in the comments below. Looking forward to reading some inspirational stories and or thoughtful guidance.
Announcements & Offers
Below highlights few announcements I made end of 2023 for 2024:
Launched an MVP-Beta as a digital download for Asset Owners - STL’s OT Cybersecurity Best Practices Requirements Specification OTCBPRS Toolkit including free IT & OT CySEAT (see announcement below), as a launch offer for a limited seats.
A new additional home for Securing Things Newsletter was selected and launched - checkout the LinkedIn announcement here. Have some new plans in play for 2024. So stay tuned and be sure subscribe at the link above to avail the discounts.
Launched Security Awareness Training & Phishing Awareness Portal target for SMBs - LinkedIn announcement here and provides:
- Security Awareness Training✅ (Free, Lite and Pro offerings)
- Awareness Material Posters✅ (free added value as subscriber)
- Phishing Simulation✅ (part of pro offerings, not included in Lite)
- Security Policy Templates✅(free added value as subscriber)
- Cyber Health Checks/Reviews✅(free added value as subscriber).
Soon to be launched - Securing Things Academy (STA) - however here’s a new announcement. Building 2 digital products highlighted below:
#CySEAT

Securing Things Academy (Online Training) - IT & OT CySEAT
Am looking for at-least 10-15 companies / Asset Owners from manufacturing and other critical infrastructure sector for the beta launch. Please DM or reach out to me if you are an asset owner and interested to participate in the discounted beta offer coming soon. Will be reaching out to some of you. Know any asset owners that may be planning (starting or struggling with) OT Cybersecurity program journey and or simply looking to uplift staff skills sets?, without breaking the budget, please share this post, it’ll be of an enormous help.
Ideal candidates for CySEAT training program are practitioners both from IT/ICT Team (CISO/CIO/CDO orgs) and OT/ICS production or plant teams (industrial IT, engineering, operations etc.) that are responsible for building, managing and or part of executing OT cybersecurity program activities designed to improve OT/ICS cybersecurity hygiene for small and medium-sized manufacturers.
And the OT Security Dozen series for a more in-depth OT/ICS cybersecurity training, covering each of the controls mentioned in OT security dozen (and related topics from ISA/IEC 62443 and SANS GCISP certs).

Securing Things Academy (Online Training) - OT/ICS Security Dozen Series
Also hope to record & publish few short courses as well (STA or other platforms). So stay tuned…Do register your interest, please subscribe to the newsletter here.
On Industry
2023 - A Year of AI, Ransomware, Attacks, Cybersecurity Trends & more
Here are some interesting highlights:
1. Artificial Intelligence (AI), Guidance & Regulations
Start of 2023, our digital world was struck with OpenAI’s ChatGPT free offering, since than AI, AGI, LLMs, prompt engineering and other lingos were added to our dictionaries globally and was undoubtedly the most talked about topic. And we all saw accelerated growth for AI / Generative AI based softwares or platforms and their usage steadily creeping into our daily lives, in almost all forms of industry segment, making us more productive (and for some, arguably perhaps, somewhat dumb and lazy at the same time).
This increased usage and reliance on this tech, opened up new avenues of AI or large learning models (LLMs) related attacks (e.g., adversarial attacks, backdoors and data poisoning attacks, prompt injections, jailbreaks, data extraction privacy issues, data reconstruction, denial of services, escalation, evasion malicious code, cross-model, multimodal, model theft, and automation). NCSC assessment, focusing on near-term impact of AI on the cyber threat concluded that AI will almost certainly increase the volume and heighten the impact of cyber attacks over the next two years. However, the impact maybe uneven; both in terms of its use by cyber threat actors and in terms of uplift in capability. Read the assessments here.
A very recent example of a phishing scam where deepfakes are used, resulted in a Hong Kong company losing millions of dollars.
All these in turn, derived the need for defenders to bring to market the much needed detective tools and techniques, practices, policies, laws and legal regulations against the growing risks of new form of attacks (more on this specific topic in future posts). Below is a list of few select important reads:
Global AI Legislation Tracker by IAPP Research and Insights - great reference resource to bookmark.
Guidelines for secure AI system development became Global AI security guidelines endorsed by 18 countries listed (/22 countries).
2023 ended with the release of ISO 42001 (ISO standard for AI) - an international management system standard that provides guidelines for managing AI systems within organizations.
Cybersecurity of AI and Standardisation, guidance by ENISA.
OWASP LLM Top 10 published in 2023, documents Top 10 risks and recommendations on how to mitigate those risks, for LLM systems.
And many more to cover.
2. Ransomware Attacks & Data breaches
Just like 2022, 2023 was no short of news related to ransomware attacks and data breaches with millions of records stolen or leaked from all over the world. Here’s a link to website that maintains the list of World's Biggest Data Breaches & Hacks.
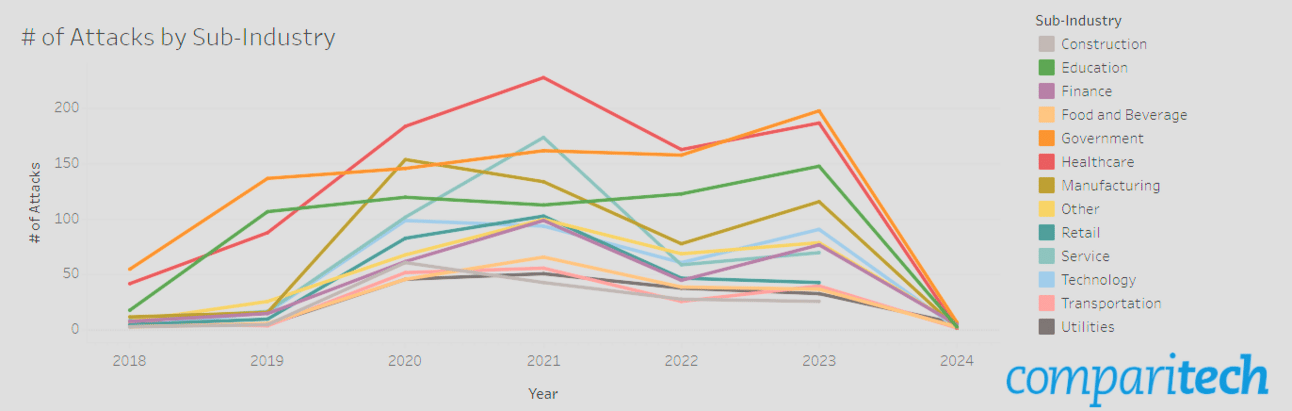
Another great resource that maintains Map of worldwide ransomware attacks (updated daily) by Comparitech and also provides breakdown by industry vertical.
3. Cybersecurity Market Trends and Regulations
Trends & Predictions
2023, saw a number of layoffs, tech moves and several mergers & acquisitions, continued skills shortage, and more. Interested in knowing what happened in cybersec industry in 2023 - check-out:
“A Year of Disruption and Resilience: The Cybersecurity Market in 2023”, by Mike Privette, an excellent post - must read.
Global Cybersecurity Outlook 2024 by World Economic forum.
SANS ICS/OT 2023 survey report - checkout post here with brief summary including link to the original source.
OT/ICS Predictions 2024 by Kaspersky.
What was your best reads? type in comments below.
Notable Regulations
2023 also saw governments globally, announcing new laws, regulations around critical infrastructure. Similarly, several new cybersecurity industry best practices guidelines, and standards were published. Below is a just a sample list (in no particular order / classification):
Final SEC US cybersecurity rules released - checkout post here with brief summary including link to the original source.
The NIS2 Directive: A EU-wide legislation on cybersecurity, with specific aim was to achieve a high common level of cybersecurity across the member states. It has to be noted that, by 17 October 2024, after which member states have to transpose NIS2 into National Legislative System. ENISA published guidance and a visual NIS Directive tool. NCSC also released a good quick reference guide for NIS2.
CCOP v2 and upcoming enforcement deadlines from Singapore CSA.
What other important regulations you’ve seen in 2023? comment below.
5. Industry 4.0 / Digital Transformation / IIOT:
Industry saw more adoption of 4.0 concepts like, Unified Namespace based digital transformations program in manufacturing sector, with increased adoption and or use of MQTT, Sparkplug B, DataOps and other technologies for several IIOT based implementations. This trend is going to grow as manufacturers see stiff competition ahead, on producing more goods with less and have started realizing the benefits of a true real-time unified view of the plant floor. Checkout an insightful article by several experts predicting what lies ahead for the industrial transformation space in 2024 - IIoT World’s Board of Advisors Envisioning 2024’s Industrial Transformation.
6. Content Economy & SaaS:
2024 will be battle ground for quality content, as the usage of AI assisted content grows exponentially, with many SaaS based offerings available. I believe Micro-SaaS (targeted for small, industry, or task-specific software as a service solutions) will be on the rise for 2024. Several cybersecurity solutions to surface the market using the power of this model to address specific niche problems e.g. SMB market and or CISO or risk management - all in one - type solutions.
OT/ICS Cybersecurity Topic of the Day
Enough about reflections, now onto the OT/ICS Cybersecurity topic of the day:
Transient Assets in OT/ICS

Transient Assets in OT/ICS - Credit AI: Dalle/Bing, Prompt: myself :-)
Transient assets are generally portable devices that are not permanently connected to OT/ICS network, do not reside within the operational environment, moves in and out of an OT/ICS environment for troubleshooting or for network traffic capture and analysis. Example of such devices are (but not limited to):
laptops (operational) or backup workstations
engineering system calibration tools
vulnerability scanning and packet capture tools, and
other equipment (portal hard drives, USBs, any data transfer devices etc.)
Use Cases:
Physically brought into OT/ICS environment when remote access to production is not feasible, possible, or advisable when performing (but not limited to):
General system maintenance / device updates
Configuration (implementation and or re-programming of PLCs, and or other field devices)
Troubleshooting engineering and or network problems.
Typical Users:
Internal Staff (Engineering, shift maintenance, technicians & others)
System Integrators and or Maintenance Service Providers
External Contractors.
Cyber Risks & Risk Reduction Means for Transient Assets
Cyber Risks:
Such transient devices introduces risks to OT/ICS environments, as they can be compromised assets and may introduce contamination unintentionally and or may be targeted by an adversary, in the likely event to be brought into network environment physically, bypassing all the layered security controls and be directly attached to the core of production control network.
Recommended industry standards and or best practices could be adapted as part of an OT/ICS cybersecurity program. Use a combination of both administrative & technical controls needs to be adapted to reduce the risks of transient devices, such as (but not limited to):
keep devices up-to-date, with malware & other security controls enabled.
Use only dedicated (/trusted & authorized) device(s), and
whenever possible, ensure such devices are configured to boot from a read-only media, single-use virtual machines, and or embedded OS. Minimizing the risks of malware infections and ensures a protected operating system.
Mitre ICS Att&ck (ID:T0864), is specific to transient cyber assets.
Cybersecurity literacy in 2024
As we embark on 2024, I invite each member of the #Securing Things community to share their insights, feedback, and wish list for the year on:
any industry specific pain points & potential resolutions of keen interest?
what did you like about this and previous edition?
what could be improved?
what you’d like to see in future editions?
Your feedback and input is invaluable as we work together to strengthen our cybersecurity defenses and create a safer digital future. Thank you for your trust and continued support.
Here's to Securing Things in 2024! Take care and Best Regards,
Securing Things Academy:
IT & OT CySEAT (Cyber Security Education And Transformation) course is designed for IT and OT cybersecurity practitioners. Join the wait-list → here.
Checkout a brief overview below:
Ways in which I can help?
Whenever you are ready - I can help you with:
A - IT & OT Cybersecurity Advisory / Consulting services - for securing your business and or its digital transformation journey.
B - Security Awareness Training & Phishing Awareness Portal - Train your staff and build a Security awareness program subscription based service.
C - Securing Things Academy (STA) - Security trainings for IT & OT practitioners.
Visit the newsletter website for Links to above services and or reach out at info[at]securingthings[dot]com or DM me via LinkedIn.
D - Securing Things Newsletter - Sponsor this newsletter to showcase your brand globally, or subscribe to simply Get Smarter at Securing Things.
Reach out at newsletter[at]securingthings[dot]com or DM me via LinkedIn.
How are we doing?
I invite you as part of #SecuringThings community to share your feedback.
Rate the newsletter content
Your feedback and input is invaluable to me as we work together to strengthen our cybersecurity defenses and create a safer and smarter digital society.
Let us know how we can improve this and or what you’d like to see in future?
Thank you for your trust and continued support.
Do register, validate your email, and request login link to submit poll to be able to enter a chance to win a future course giveaway.
Thanks for reading - until the next edition!
It’s a Great Day to Start Securing Things for a Smart & Safer Society.
Take care and Best Regards,
M. Yousuf Faisal. (Advice | Consult Cyber & business leaders in their journey on Securing Things (IT, OT/ICS, IIOT, digital transformation, Industry 4.0, & AI) & share everything I learn on this Newsletter | and upcoming Academy).
The Newsletter Platform Built for Growth
When starting a newsletter, there are plenty of choices. But there’s only one publishing tool built to help you grow your publications as quickly and sustainably as possible.
Beehiiv was founded by some of the earliest employees of the Morning Brew, and they know what it takes to grow a newsletter from zero to millions.
The all-in-one publishing suite comes with built-in growth tools, customization, and best-in-class analytics that actually move the needle - all in an easy-to-use interface.
Not to mention—responsive audience polls, a custom referral program, SEO-optimized webpage’s, and so much more.
If you’ve considered starting a newsletter, there’s no better place to get started and no better time than now.