Disclaimer: All views presented here, in this newsletter, are my own.
Author or the newsletter are not liable for any actions taken by any individual or any organization / business / entity. The information provided is for education and awareness purposes only and is not specific to any business and or situation.
Hey there,
Hope you are doing well.
Here are some key IT, OT, AI - Cybersecurity insights from Q2 2025 related to:
✍️ Cybersecurity M&As, fundings, and Start-ups.
‼️ Cyber Incidents, Ransomware Attacks & Data breaches.
📘 Notable Updates - Guidance, Standards & Regulations!.
📘 Artificial Intelligence (AI), Guidance & Regulations.
↪️ How CISO’s role is evolving in Q2 2025.
↪️ References used.
Why read this? Lots have happened in Q2 2025.
If you're seeking insights on any of the above topics, you'll find valuable information that can shorten your search quest.
In case you missed previous quarterly updates you’ll find it here → Q1 2025.
But before we begin, do me a favour and make sure you “Subscribe” to let me know that you care and keep me motivated to publish more. Thanks!
Ready? let’s dig in.
Yours truly.
— Yousuf.
♻️if you know someone in your professional circle who will benefit from these resources and interested in learning. Thanks 🌟
Together with (Sponsor):
Is your social strategy ready for what's next in 2025?
HubSpot Media's latest Social Playbook reveals what's actually working for over 1,000 global marketing leaders across TikTok, Instagram, LinkedIn, Pinterest, Facebook, and YouTube.
Inside this comprehensive report, you’ll discover:
Which platforms are delivering the highest ROI in 2025
Content formats driving the most engagement across industries
How AI is transforming social content creation and analytics
Tactical recommendations you can implement immediately
Unlock the playbook—free when you subscribe to the Masters in Marketing newsletter.
Get cutting-edge insights, twice a week, from the marketing leaders shaping the future.
Cybersecurity M&As, fundings, and Start-ups
According to pinpoint search group: There’s an increased Funding Rounds & Stable investments levels; despite a slight decline in total funding raised, the cybersecurity sector remains attractive.
Cybersecurity investments surged by 25% in Q2 2025 compared to Q2 2024, with average deal sizes climbing too — a strong sign of market confidence and acceleration in innovation.
A total of 118 cybersecurity vendor transactions, including 100 funding rounds and 18 merger and acquisition (M&A) events.
A total of $4.2 billion was raised across the 100 funding rounds.
The funding for the quarter represents almost double the $2.2 billion raised in Q1 2025 and takes the total funding for the year to date (YTD) up to $6.4 billion.
Seed and Series-A start-ups led the funding landscape, accounting for 55% of all funding rounds in Q2 2025, a 6% decline since Q1 2025.
Security budgets surge: According to AGC's Q2 2025 Cybersecurity Market Update - Organizations increased cybersecurity spending and raising security budgets by an average of 27% in 2025, driven by escalating threats projected to cost $10.3 trillion in 2025 globally. With every sector under sustained assault, cybersecurity has become a board-level imperative. If cybercrime were a country, it would be the third-largest economy on Earth, right behind the U.S. and China. AGC Partners closed 7 cyber deals in 18 months, targeting cloud/identity security and AI-native threat detection.
M&A acceleration: According to security week - 28 cybersecurity deals announced in February 2025, including CyberArk’s $165M acquisition of identity governance firm Zilla Security and Turn/River Capital’s $4.4B takeover of SolarWinds.
Sector interest shifts: DeepTech/Robotics (6.7%) overtook AI/ML (6.3%) as the top VC investment category, signalling confidence in hardware-centric solutions.
Venture challenges: Geopolitical uncertainty (7.5%) and cyber threats (6.0%) topped VC concerns, though AI tools streamlined due diligence and portfolio monitoring.
Public valuations: Market rewarded top operators with premium multiples, though IPO activity remained subdued.
Emerging players: Orchid Security hired ex-Wiz channel leader Trish Cagliostro to drive identity-security orchestration.
Alphabet’s Acquisition of Wiz: Alphabet’s bold move to acquire Wiz for over $20B signals the growing platformization of AI security and the consolidation of cloud-native security vendors.
1Password’s Blue Ocean Strategy: 1Password’s massive Series C funding and strategic pivot highlight the increasing value of identity management in a password less future.
Palo Alto Networks & Protect AI: The acquisition of Protect AI by Palo Alto Networks showcases the rush to integrate AI security into mainstream cybersecurity platforms.
Record Funding Rounds & Late-stage funding dominance
Q2 saw several $100M+ rounds, including Cyera and Endor Labs, reflecting investor confidence in cloud data security and software supply chain risk. Examples include Wiz ($1B) and Cyera ($300M).
Mobile Security Start-ups Rise: Start-ups focusing on mobile device security, a traditionally underfunded sector, are now seeing increased VC attention due to the evolving threat landscape.
M&A Activity Remains Strong: The market saw a wave of acquisitions, including CyberArk’s purchase of Zilla Security (identity governance) and TAC Security’s acquisition of CyberScope (blockchain audit).
AI Security Start-ups in Focus: Companies like Sentra and Endor Labs raised significant rounds to secure AI-generated code and agentic AI environments.
VCs Shift to DeepTech: DeepTech and robotics startups surpassed AI/ML as the top investment focus, showing a trend toward hardware-centric security solutions.
Strategic Market Analysis: Strategy of Security’s research highlights a shift toward platformization and the integration of AI across security solutions, as seen in recent M&A and funding trends.
Industry Analyst Influence Persists: Despite rumours of decline, industry analyst firms remain key influencers in vendor selection and funding decisions.
AI takes the stage: Over 82% of funded seed-stage cybersecurity startups are now integrating AI, and nearly 25% are devoted to securing AI systems themselves.

Source: Data Tribe Q2 2025
VCs hire cybersecurity experts to guide bets: Venture capital firms are increasingly hiring cybersecurity specialists to vet investments, reflecting growing recognition that digital safety is complex and critical.
AI pressures lead to small-firm consolidation: Smaller cybersecurity firms (with $50M–$300M ARR) are feeling the pressure to keep up with costly AI capabilities. Many are exploring acquisitions — pushing bigger players like Palo Alto Networks and CrowdStrike to bundle AI-powered services. For instance, Google spent billions in deals, including $32B to acquire Wiz.
Data Residency and Sovereignty: New tools address cross-border data protection requirements, especially for AI and cloud data.
Unified Security Frameworks: Organizations are adopting unified frameworks to streamline compliance across IT, OT, and cloud environments.
Zero-Day Response Protocols: Guidance urges faster patching and response to legacy vulnerabilities and zero-day exploits.
Cyber Insurance Alignment: Regulations are driving demand for resilience validation and cyber insurance alignment.
Acquisitions, Seed and Funding
Based on pinpoint search group, below are the key IT/OT acquisitions in Q2 2025:
Vendor | Activity Type | Acquiring Company | Financials | Market Segment |
Zorus | Acquisition | DNSFilter | Undisclosed | DNS |
Infigo | Acquisition | Allurity | Undisclosed | Security Services |
ProtectAI | Acquisition | Palo Alto Networks | $700,000,000 | AI/LLM |
Opus Security | Acquisition | Orca | Undisclosed | Threat Intel |
Lookout Cloud Security | Acquisition | Fortra | Undisclosed | Cloud |
Hornetsecurity | Acquisition | Proofpoint | $1,000,000,000 | Security Services |
Veriti | Acquisition | Check Point | $100,000,000 | Ratings |
Red Canary | Acquisition | Zscaler | Undisclosed | Detection / Response |
Apex | Acquisition | Tenable | Undisclosed | GRC |
Corellium | Acquisition | Cellebrite | $190,000,000 | Vulnerability |
Raito BV | Acquisition | Collibra | Undisclosed | Identity |
Nok Nok Labs | Acquisition | OneSpan | Undisclosed | Identity |
Fletch | Acquisition | F5 | Undisclosed | Vulnerability |
SecureAck | Acquisition | CybaVerse | Undisclosed | Automation |
ThreatQuotient | Acquisition | Securonix | Undisclosed | Threat Intel |
Tentacle | Acquisition | Cytracom | Undisclosed | GRC |
Mesh Security | Acquisition | Bitdefender | Undisclosed | |
Invariant Labs | Acquisition | Snyk | Undisclosed | AI/LLM |
Also, based on pinpoint search group, below are key fundings in Q2 2025:
Vendor | Activity Type | Financials | Investor | Market Segment |
Prowler | Seed | Decibel VC | $6,500,000 | Vulnerability |
Octane | Seed | Archetype | $6,750,000 | AppSec |
Liminal | Seed | Elevation Capital | $4,700,000 | Crypto |
Unosecur | Seed | VentureFriends | $5,000,000 | Identity |
Pillar Security | Seed | Shield Capital | $9,000,000 | AI/LLM |
Kenzo Security | Seed | The General Partnership | $4,500,000 | Threat Intel |
ideem | Seed | Sovereighns Capital | $2,400,000 | Fraud |
GlitchSecure | Seed | Business Development Bank of Canada | $1,440,000 | Vulnerability |
Hopper | Seed | Meron Capital | $7,600,000 | OSINT |
Terra Security | Seed | SYN Ventures | $8,000,000 | Pen Testing |
Authmind | Seed | Cheyenne Ventures | $19,300,000 | Identity |
Augur Security | Seed | General Advance | $7,000,000 | Threat Intel |
Minimus | Seed | YL Ventures | $51,000,000 | AppSec |
Valarian | Seed | Scout Ventures | $7,000,000 | Segmentation |
Tesseral | Seed | Y Combinator | $3,300,000 | Identity |
Kovr.ai | Seed | IronGate | $3,600,000 | GRC |
Pixee | Seed | Decibel VC | $15,000,000 | AppSec |
Unbound | Seed | Race Capital | $4,000,000 | AI/LLM |
Amplifier Security | Seed | Westwave Capital | $5,600,000 | Training |
Dedge Security | Seed | Tritemius | $4,600,000 | AppSec |
ZeroRISC | Seed | Fontinalis Partners | $10,000,000 | Firmware Security |
Repello AI | Seed | General Catalyst | $1,200,000 | PenTesting |
Circumvent | Seed | Paladin Capital Group | $6,000,000 | AppSec |
Quantix Edge Security | Seed | SETT | $22,600,000 | Firmware Security |
Steryon | Seed | 4Founders Capital | $1,100,000 | GRC |
RevEng.ai | Seed | Sands Capital | $4,150,000 | Supply Chain |
Bonfi.AI | Seed | TLV Partners | $9,500,000 | Data |
Better-Auth | Seed | Peak XV | $5,000,000 | Identity |
8Layers | Seed | JME Ventures | $1,700,000 | Identity |
Adaptive | Funding | Andreesen Horowitz | $43,000,000 | Training |
Aurascape | Funding | Menlo Ventures | $50,000,000 | AI/LLM |
Qevlar | Funding | EQT Ventures | $10,000,000 | Threat Intel |
VanishID | Funding | Dell Technologies Capital | $10,000,000 | Fraud |
NetFoundry | Funding | SYN Ventures | $12,000,000 | Network Security |
SixMap | Funding | IAG Capital | $7,000,000 | Threat Intel |
Cyacomb | Funding | Scottish National Bank | $2,900,000 | Forensics |
TrustCloud | Funding | ServiceNow Ventures | $15,000,000 | GRC |
StackHawk | Funding | Sapphire Ventures | $12,000,000 | AppSec |
Cyera | Funding | Georgian | $500,000,000 | Data |
Impart Security | Funding | CRV | $10,999,000 | API |
Naoris | Funding | Mason Labs | $3,000,000 | Crypto |
Corsha | Funding, A | SineWave | $18,000,000 | Identity |
Outtake AI | Funding, A | CRV | $16,500,000 | Detection/Response |
Netrise | Funding, A | DNX Ventures | $10,000,000 | Supply Chain |
Virtue AI | Funding, A | Lightspeed Ventures | $30,000,000 | AI/LLM |
Cy4Data Labs | Funding, A | Pelion Venture Partners | $10,000,000 | Data |
Exaforce | Funding, A | Khosla Ventures | $75,000,000 | Automation |
Miggo Security | Funding, A | SYN Ventures | $17,000,000 | Detection/Response |
Manifest | Funding, A | Ensemble | $15,000,000 | Supply Chain |
Scamnetic | Funding, A | Roo Capital | $13,000,000 | Fraud |
Jericho Security | Funding, A | Era Fund | $15,000,000 | Training |
SquareX | Funding, A | SYN Ventures | $20,000,000 | Browser |
Symbiotic | Funding, A | Pentera Capital | $29,000,000 | Crypto |
Pistachio | Funding, A | Walter Ventures | $7,000,000 | Training |
LayerX | Funding, A | Jump Capital | $11,000,000 | Browser |
Qnu Labs | Funding, A | National Quantum Mission | $7,000,000 | Quantum |
ClearVector | Funding, A | Scale Venture Partners | $13,000,000 | Identity |
BreachRX | Funding, A | Ballistic Ventures | $15,000,000 | GRC |
Theom | Funding, A | Wing VC | $20,000,000 | Data |
Bright Security | Funding, A | TOLOKA | $1,000,000 | AppSec |
Clarity Security | Funding, A | Silverton Partners | $9,000,000 | Identity |
Trustifi | Funding, A | Camber Partners | $25,000,000 | |
ThreatSpike | Funding, A | Expedition Capital | $14,000,000 | MSSP |
MIND | Funding, A | Paladin Capital Group | $30,000,000 | Data |
Compyl | Funding, A | Venture Guides | $12,000,000 | GRC |
Baobab Insurance | Funding, A | Viola FinTech | $13,676,000 | Cyber Insurance |
Infisical | Funding, A | Gil Capital | $16,000,000 | Identity |
Maze | Funding, A | Theory Ventures | $25,000,000 | Vulnerability |
Anecdotes | Funding, B | DTCP | $30,000,000 | GRC |
Portnox | Funding, B | Updata Partners | $37,500,000 | Network Security |
Sekoia.io | Funding, B | Revaia | $28,500,000 | XDR |
Sentra | Funding, B | Key1 Capital | $50,000,000 | Data |
Endor | Funding, B | DFJ Growth | $93,000,000 | AppSec |
Cynomi | Funding, B | Entrée Capital | $37,000,000 | Virtual CISO |
Reco | Funding, B | Zeev Ventures | $25,000,000 | SaaS Security |
Push Security | Funding, B | Redpoint Ventures | $30,000,000 | Identity |
Doppel | Funding, B | Bessemer | $35,000,000 | OSINT |
Ox Security | Funding, B | DTCP | $60,000,000 | AppSec |
Acompany | Funding, B | Beyond Next Ventures | $7,501,031 | Data |
CloudSEK | Funding, B | MassMutual Ventures | $19,000,000 | Threat Intel |
Cerby | Funding, B | DTCP | $40,000,000 | Identity |
Guardz | Funding, B | ClearSky | $56,000,000 | Detection/Response |
Turnkey | Funding, B | Bain Capital | $30,000,000 | Crypto |
Hypernative | Funding, B | Ten Eleven Ventures | $40,000,000 | Crypto |
Conveyor | Funding, B | SignalFire | $20,000,000 | GRC |
Fleet | Funding, B | Ten Eleven Ventures | $27,000,000 | Endpoint |
Supply Wisdom | Funding, B | Jurassic Capital | $14,000,000 | GRC |
Zama | Funding, B | Blockchange Ventures | $57,000,000 | Data |
Tailscale | Funding, C | Accel | $160,000,000 | Network Security |
Zero Networks | Funding, C | Highland Europe | $55,000,000 | Segmentation |
Clearspeed | Funding, D | Align Private Capital | $60,000,000 | Fraud |
Cyberhaven | Funding, D | StepStone Group | $100,000,000 | Data |
Chainguard | Funding, D | Kleiner Perkins | $356,000,000 | Supply Chain |
Veza | Funding, D | Accel | $108,000,000 | Identity |
Persona | Funding, D | Founders Fund | $200,000,000 | Identity |
Horizon3.ai | Funding, D | NEA | $73,000,000 | PenTesting |
ReliaQuest | Growth Funding | EQT Partners | $500,000,000 | XDR |
Swimlane | Growth Funding | Energy Impact Partners | $45,000,000 | Automation |
Cato Networks | Growth Funding | Undisclosed | $359,000,000 | SASE |
Gatewatcher | Debt Funding | European Investment Bank | $29,400,000 | Detection/Response |
Cyber Incidents, Ransomware Attacks & Data breaches
Hacktivist ICS (OT) Attacks Surge: According to Cyble report, Hacktivist campaigns escalated significantly in Q2, with Z-Pentest conducting 38 ICS attacks (up 150% Quarter on Quarter). Energy and utilities were especially targeted across Europe — highlighting strategic cyber disruption efforts.

Source: Cyble Blog (link under references)
Manufacturing was the second most targeted sector in Q2 after Education.

Source: Cisco Talos IR Trends Q2 2025
Phishing evolution: Threat actors used QR codes, CAPTCHA bypasses, and AI-driven multi-channel lures (email / sms / voice), with "PhaaS" kits like EvilProxy democratizing attacks.
Downtime costs: Unplanned outages cost Fortune 500 firms $1.5 trillion annually (11% of revenue).
UK-specific threats: Tax / immigration scams and fake Booking.com domains exploited seasonal lures.
Legacy system risks: Outdated vulnerabilities and zero-days remained widely exploited.
Data monetization: Stolen credentials sold in 30+ datasets averaging 550M records each.
Operational disruption: CISA-defined "substantial incidents" caused critical infrastructure downtime.
Industrial Attacks Surge: According to Honeywell report, attacks on OT/ICS and critical infrastructure rose by 46% quarter-over-quarter, with a 3,000% spike in credential-stealing malware targeting these sectors.
Mobile Device Threats: Mobile phishing and multi-channel lures (email, SMS, voice) are on the rise, with QR code and CAPTCHA-bypass attacks becoming mainstream.
SME Vulnerabilities: Small and mid-market organizations are increasingly targeted due to weaker defenses and slower patch cycles.
Supply Chain Risks: Compromises in third-party software and open-source components continue to drive high-profile breaches.
AI-Driven Attacks: Attackers are leveraging AI to automate phishing, social engineering, and vulnerability discovery.
Downtime Costs Skyrocket: Unplanned outages and cyber incidents now cost Fortune 500 companies an estimated $1.5 trillion annually.
Fake Domains and Scams: Seasonal lures, such as tax and travel scams, are increasingly used to trick users into divulging credentials.
The trend of significant data breaches in Q2 2025 continued throughout the quarter, emphasizing the ongoing cybersecurity challenges faced by organizations.
Personal data breaches rise: Breach events grew by ~21% quarter-over-quarter, with exposed email addresses up 15%. Records from the X/Twitter leak resurfaced, continuing to haunt victims.
Credential Mega-Breaches and Session Cookie Theft: Over 16 billion passwords were exposed in Q2, affecting major platforms like Facebook, Google, Apple, and Telegram, often via infostealer malware enabling 2FA bypass via stolen session cookies, enabling account takeovers even with strong authentication.
SharePoint zero-day exploitation: A critical zero-day (ToolShell, CVE-2025-53770) in Microsoft SharePoint was actively exploited, compromising over 400 systems globally. A new group “Warlock” is exploiting unpatched systems.
Here’s some stats on ransomware attacks targeting different industries and sectors:
Global ransomware incidents trend shifts: Roughly 1,600 – 1,758 ransomware events were reported globally in Q2 2025 — a ~19–25% year-over-year increase, with the U.S. hit hardest, accounting for ~49% of total attacks.
Hidden attacks surge: BlackFog reports a 63% year-over-year surge in Q2 ransomware attacks — yet 80.9% went unreported, underscoring massive under-the-radar risk.
But overall volume down from Q1: NCC Group noted a 43% drop in ransomware attacks compared to Q1, from 2,074 to 1,180 incidents, likely due to law enforcement disruption and internal conflict among hacker groups. Infosecurity Magazine.
A fragmented threat landscape: Ransomware groups remain highly active— with 71 groups now operating (up 58% YoY), and DragonForce claiming over 120 victims in Q2, with 20 new in June alone.
Ransomware pivot: 95% of ransomware incidents shifted from encryption to pure data theft/extortion to evade detection.
SME targeting: Ransomware groups focused on mid-market firms lacking enterprise-grade defenses.
Ransomware Tactics Evolve: 95% of ransomware attacks now focus on data exfiltration and extortion rather than just encryption, making detection and recovery more challenging.
Qilin ransomware skyrockets: Qilin saw an 80% increase in activity from Q1 to Q2, primarily by exploiting Fortinet/FortiGate vulnerabilities (CVE-2024-55591 & CVE-2024-21762).
Malware trend: SocGholish leads Malware notifications dropped 18% in Q2. The top malware was SocGholish (31% of detections), followed by ZPHP, Agent Tesla, and newcomer VenomRAT—an open source RAT showing growing use.
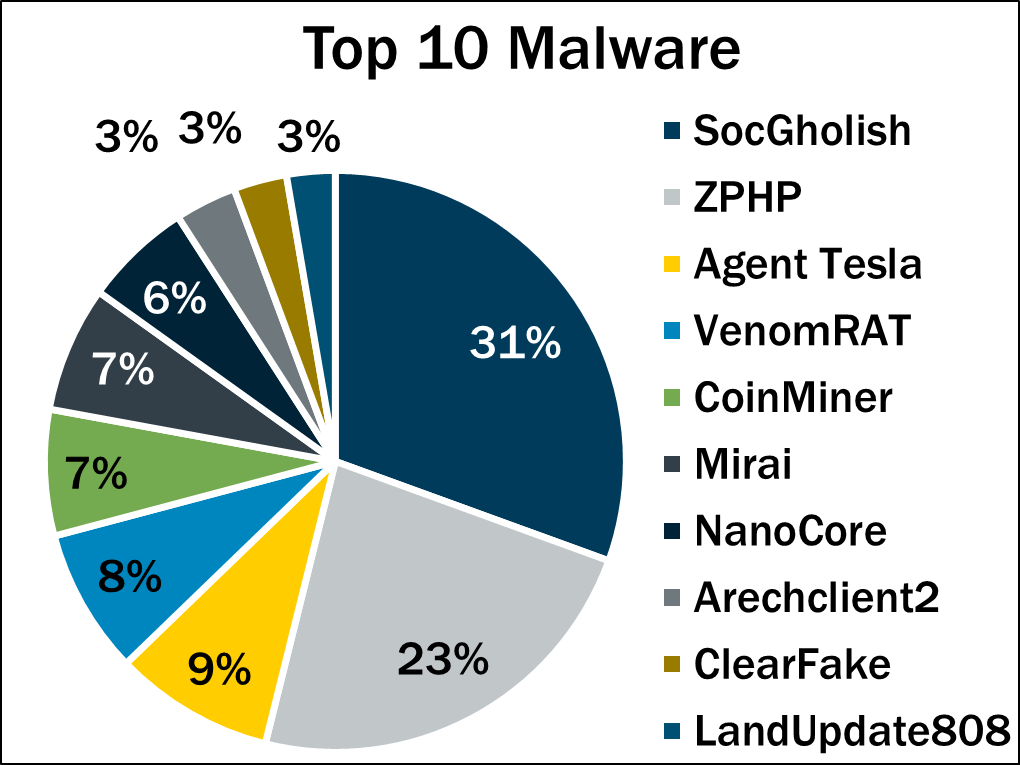
Source: CIS Q2 2025 Malware
Together with (Sponsor):
Typing is a thing of the past.
Typeless turns your raw, unfiltered voice into beautifully polished writing - in real time.
It works like magic, feels like cheating, and allows your thoughts to flow more freely than ever before.
Your voice is your strength. Typeless turns it into a superpower.
Updates - Guidance, Standards & Regulations!
Here are some of the updates on regulations and standards in the cybersecurity field from Q2 2025. (Note: No major regulatory updates were reported in Q2 2025 sources. Focus shifted to existing frameworks and emergent best practices).
Mapping the U.S. Federal Cybersecurity Ecosystem
Strategy of Security published a comprehensive analysis mapping the complex U.S. federal cybersecurity, privacy, and trust initiatives, helping organizations navigate evolving compliance landscapes.EU Cybersecurity Research Funding Boost
The European Commission plans to increase cybersecurity research funding to €90.5 million in 2025, focusing on generative AI for cybersecurity, post-quantum cryptography, and operational cybersecurity tools.Incident Reporting and Compliance Automation
CISA updated its definition of “substantial incidents,” pushing for faster, more transparent breach disclosures. Automated compliance platforms are gaining traction to help SMEs meet regulatory requirements efficiently.NIST AI Risk Management Framework Update
The US NIST released updates focusing on adversarial robustness, privacy, and explainability in AI systems, aligning with growing regulatory scrutiny.EU AI Act Nears Enforcement
The EU AI Act continues to advance, with provisions targeting AI use in critical infrastructure and cybersecurity applications, raising the bar for secure AI deployment.Ethical AI Frameworks: While no major new regulations emerged in Q2, industry events and research emphasized “secure-by-design” AI principles and responsible innovation.
Supply Chain Security Frameworks
Industry coalitions released new standards for securing open source software supply chains, responding to ongoing supply chain attack threats.US Federal Cybersecurity Ecosystem Mapping: New research maps the complex landscape of US federal cybersecurity, privacy, and trust initiatives, helping organizations navigate compliance.
Artificial Intelligence (AI) Guidance & Regulations
AI-related cybersecurity investments, developments, incidents / attacks and risks in Q2 2025 showed significant trends and developments:
AI introduces real-world breach risks: IBM found 20% of organizations experienced breaches due to unauthorized "shadow AI," adding $670K extra to breach costs. 13% of breaches involved legitimate AI tools, often via compromised supply chains. Only 3% had proper AI access controls. Generative AI is widely misused in attacks—phishing (37%), deepfakes (35%)— with breach involvement rising to 16%.
AI supply chains under fire: Q2 revealed increasing “poisoned AI pipelines” becoming upstream attack vectors. Emerging frameworks like Europe’s DORA and final U.S. CMMC rules now push organizations to embed AI risk into resilience and incident response planning.
AI-native security: Innovation accelerated in AI-powered threat detection, with platforms automating agentic-model monitoring.
Offensive AI: Phishing campaigns leveraged AI for hyper-personalized multi-channel attacks, boosting success rates.
VC deployment: 4.4% of firms used AI for due diligence, portfolio analytics, and market forecasting.
Regulatory tension: AI was simultaneously an investment catalyst (4.4%) and compliance hurdle (3.2%) for VCs.
Data-protection synergy: Honeywell linked AI-driven attacks to data-breach costs, emphasizing runtime application monitoring.
Defensive tools: Oligo Security’s $50M Series B funded runtime app visibility to counter AI-exploited vulnerabilities.
AI Security Platformization Accelerates
Strategy of Security highlights how AI security is becoming a core part of cybersecurity platforms, as evidenced by major acquisitions and product launches.AI Security Shared Responsibility Model
Return on Security introduces the AI Security Shared Responsibility Model, a framework guiding organizations to manage AI risks and compliance effectively.Securing AI-Generated Code and Agents
Start-ups are pioneering solutions to secure AI-generated code and protect data in AI agent workflows, addressing unique AI security challenges.AI-Driven Threat Intelligence and SOC Automation
AI-powered platforms are enhancing predictive threat analytics and automating security operations center (SOC) workflows to improve response times.
AI Security Platformization: The integration of AI security into mainstream platforms is accelerating, as seen in major acquisitions and product launches.
AI as Double-Edged Sword: AI is both an enabler for attackers (automated phishing, vulnerability discovery) and a defender (threat detection, SOC automation).
VCs Grapple with AI Regulation: AI regulation is now a top concern for venture investors, shaping funding and product development strategies.
Secure AI Development: Start-ups are leading efforts to secure AI-generated code and agentic AI environments.
AI-Powered SOCs: Security operations centers are integrating AI-driven analytics and automation for faster, more accurate threat response.
Data Protection in AI: “Data Security for AI Agents” address the unique risks of data residency and privacy in AI workflows.
AI-Driven Threat Intelligence: AI-powered security operations centers (SOCs) integrated platforms are using AI for predictive analytics and proactive defense.
Automated AI Governance: vCISO platforms are helping organizations and consultants manage the complexity of AI compliance and risk.
AI Skills Gap Solutions: Automated vCISO solutions and similar tools are helping bridge the talent gap in AI security and governance.
AI is transforming cybersecurity in Q2 2025 by driving new laws, increasing threat sophistication, and pushing organizations to adopt advanced AI defenses and governance.
How CISO’s role is evolving in Q2 2025
By Q2 2025, the CISO role is evolving from a technical, defensive position to a strategic, business-aligned leadership role in both IT and OT cybersecurity.
Key Aspects of the Evolving CISO Role in Q2 2025:
From Technical Gatekeeper to Strategic Business Leader: CISOs have evolved from managing technical controls to becoming strategic partners in digital innovation, business enablement, and risk governance. They collaborate with executives and boards, translating cyber risks into business terms to influence enterprise strategy beyond IT security.
Focus on Cyber Resilience and Operational Continuity: Cyber resilience, the ability to withstand and quickly recover from cyberattacks, is now the top priority for CISOs. They focus on anticipating attacks, minimizing disruption, and maintaining operations, acknowledging that attacks are often inevitable.
Expanded Scope Including IT and OT Security: CISOs now manage security in both IT and OT/ICS settings, addressing rising threats in critical infrastructure and ensuring operational safety and security across these hybrid environments.
Integration of AI and Automation: AI is essential for threat detection, risk management, and automating security operations. CISOs assess its benefits and risks, integrating it into security frameworks and tackling challenges like AI-driven attacks.
Broader Risk Management and Compliance Leadership: The modern CISO manages enterprise risk, covering technical threats, regulatory compliance, and third-party risks. They align security policies with business goals and regulations, bridging technical teams and executives.
Talent and Culture Shaping: CISOs champion a cyber-aware culture by focusing on workforce development, training, and employee accountability to reduce vulnerabilities. Talent acquisition and retaining skilled cybersecurity professionals are pressing challenges.
Greater Accountability and Board Engagement: About half of CISOs report directly to CEOs, highlighting their increased visibility and influence. Their role includes defending the organization, demonstrating the value of security investments, and managing liability amid growing regulatory scrutiny and personal accountability.
Adoption of Modern Security Architectures: CISOs prioritize Zero Trust models and cloud-native security to protect complex digital ecosystems, including multi-cloud and hybrid infrastructures.

Source: Q2 2025 CISO priorities
By Q2 2025, CISOs are becoming multifaceted leaders, crucial for strategic cyber resilience in IT and OT. Their success depends on combining technical skills with business insight, communication, and leadership in innovation and risk management, ensuring secure digital transformation and operational continuity amid evolving threats.
This transformation highlights that the role now focuses on securely and sustainably driving business growth, not just technology.
Securing Things Academy: (coming soon)
IT & OT CySEAT (Cyber Security Education And Transformation) course is designed for IT and OT cybersecurity practitioners. Join the wait-list → here.
Checkout a brief overview below:
References Used
AGCS Q2 2025 cybersecurity market update.
Datatribe Q2 2025 market insights
Strategy of Security for Alphabet Wiz Acquisitions, 1Password Blue Ocean, Palo Alto and more.
The 10 Hottest Cybersecurity Start-ups Of 2025 (So Far).
Larger deals propel cybersecurity funding to 2-year high in Q2.
Hacktivist Attacks on Critical Infrastructure Grow as New Groups Emerge by Cyble.
Q2 2025 Cyber Threat Landscape UK Insights.
Blackfog Q2 2025 Ransomware Report.
List of Recent Data Breaches in 2025.
Ransomware and Cyber Extortion in Q2 2025.
Global Cyber Attacks Surge 21% in Q2 2025 — Europe Experiences the Highest Increase of All Regions - by Checkpoint Research.
Ransomware gangs join attacks targeting Microsoft SharePoint servers.
Top 10 Malware Q2 2025 by CIS CTI team.
Gen Q2 2025 Threat Report.
Cyber Intel Brief: Nation-state AI deception, Salesforce breaches, ransomware surge.
Cisco Talos IR Trends Q2 2025.
AI’s High Cost Pushes Smaller Cybersecurity Companies to Sell.
WEF Global Cybersecurity Outlook 2025.
The 10 Hottest Cybersecurity Start-ups Of 2025 (So Far).
Software Analyst, Return on Security and Strategy of Security newsletters.
The CISO evolution: From security gatekeeper to strategic leader.
Q2 2025 CISO priorities: Resilience, intelligence & impact take centre stage.
Top Focus Areas for CISOs in 2025.
Top 3 Priorities for CISOs in 2025 - annual survey report.
How CISOs Will Navigate The Threat Landscape Differently In 2025.
Six ways CISO role is changing in 2025 (And what to do about it).
CISO Outlook for 2025 by SecurityWeek.
CISOs in 2025: Evolution of a High-Profile Role.
My Recent Most Viewed Social Posts
In case you’ve missed - here are some of my recent most viewed social posts.
🗞️IIOT Security Guide - [ST # 72] 🗞️ What is IIOT, key threats, industry demands, best practices, & strategies to secure your IIOT implementations and more.✍️ [Securing Things by M. Yousuf Faisal] 🗞️ 🗞️
Getting started in IT & OT Cybersecurity - My 3 Phase blueprint Video introduction released on YouTube.
Digital Transformation & Cybersecurity Strategy📜intro on YouTube.
[ST # 71] 🗞️2025 Guide to Cybersecurity in Digital Transformation Projects✅Discover the 2025 guide to cybersecurity in digital transformation. Learn key threats, best practices, and strategies to protect your digital initiatives.✍️[Securing Things by M. Yousuf Faisal]📰
📰[ST # 70] 🗞️Jump Servers - Workgroup / Domain? ✅ Pros & Cons of joining Jump servers to IT Domain, OT Domain or workgroup, some reference resources and more ✍️ [Securing Things by M. Yousuf Faisal]📰
📰[ST # 69] 🗞️ OT Cybersecurity Procurement Process & Practices (OTCS PPP) an ultimate guide - Part 2 ✅Tailored strategies for the Water & Wastewater Utility sector by Alana Murray, related resources, upcoming part & webinar etc. ✍️[Securing Things by M. Yousuf Faisal].📰
📰[ST # 68] 🗞️ OT Cybersecurity Procurement Process & Practices (OTCS PPP) an ultimate guide - Part 1 ✅The foundations & international best practices for OT cybersecurity procurement with Alana Murray, reference resources and more ✍️ [Securing Things by M. Yousuf Faisal]📰
📰[ST # 67] The Real Security Risks - Divide between Cyber & Physical ✅Guest Post by Jamie Williams on Modern Cyber-Physical Threats and What Does Good Security Look Like Today? plus my views on the same ✍️ [Securing Things by M. Yousuf Faisal]📰
Ways in which I can help?
Whenever you are ready - I can help you with:
A - IT & OT Cybersecurity Advisory / Consulting services - for securing your business and or its digital transformation journey.
B - Security Awareness Training & Phishing Awareness Portal - Train your staff and build a Security awareness program through our subscription based service.
C - Securing Things Academy (STA) - Security trainings for IT & OT practitioners.
Visit the newsletter website for Links to above services and or reach out at info[at]securingthings[dot]com or DM me via LinkedIn.
D - Securing Things Newsletter - Sponsor this newsletter to showcase your brand globally, or subscribe to simply Get Smarter at Securing Things.
Reach out at newsletter[at]securingthings[dot]com or DM me via LinkedIn.
✉️ Wrapping Up
Have questions, comments, or feedback? Just reply directly, I’d love to hear from you.
Also, if you find this or previous newsletter edition(s) useful and know other people who would too, I'd really appreciate if you'd forward it to them. Thanks a ton.
Thanks for reading - until the next edition!
It’s a Great Day to Start Securing Things for a Smart & Safer Society.
Take care and Best Regards,
Rate the newsletter content
If you are reading this online don’t forget to register; validate your email, and request a login link to submit the poll.
Your feedback and input is invaluable to me as we work together to strengthen our cybersecurity defenses and create a safer and smarter digital society. Thank you for your trust and continued support.





