Disclaimer: All views presented here, in this newsletter, are my own.
Author or the newsletter are not liable for any actions taken by any individual or any organization / business / entity. The information provided is for education and awareness purposes only and is not specific to any business and or situation.
Table of Contents
Hi Securing Things Community,
📢 Welcome to Quantum Computing Cybersecurity crash course! 🛡️
If you've ever been curious about the Quantum Computing technology that could change everything - from solving the unsolvable to cracking codes that were once deemed unbreakable - you’re in the right place. I’ve broken it all down for you: what it is, how it works, the future it promises, and why it has the cybersecurity world on the edge.
In addition, I’ll be sharing my most viewed social media posts, ways in which I can help, and my asks.
Special Message:
Before we begin, do me a favour and make sure you hit the “Subscribe” button to let me know that you care and keep me motivated to publish more. Thanks!
Securing Things Academy:
IT & OT CySEAT (Cyber Security Education And Transformation) course is designed for IT and OT cybersecurity practitioners. Join the wait-list → here.
Checkout a brief overview below:
What is Quantum Computing?
Richard P. Feynman, well known physicists of 20th century, said: "Things on a very small scale behave like nothing you have any direct experience about... or like anything that you have ever seen." (Reference → Six Easy Pieces by Richard Feynman. Basic Books, 1998, p.116).
Quantum Physics + Computing = Quantum Computing.
Quantum computing is an entirely new paradigm of computation, using the principles of quantum mechanics to process data and information. Unlike classical computers, which use bits (0 or 1), quantum computers use Qubits. A qubit can be both 0 and 1 simultaneously, thanks to the quantum property called "Superposition". This allows quantum computers to process vast amounts of data much faster than classical ones.
Why is Quantum Computing Such a Big Deal?
Speed and Efficiency: Quantum computers have the potential to solve problems that are currently unsolvable due to the limits of classical computing. These range from complex simulations to real-time data analysis on an unprecedented scale.
Real-World Use Cases:
Drug Discovery: Quantum simulations could enable us to model complex molecules for creating new drugs.
Supply Chain Optimization: Companies like Volkswagen have already experimented with quantum algorithms to optimize traffic flow in urban areas.
Artificial Intelligence (AI): Machine learning models could see a huge leap in efficiency and accuracy, enabling smarter, faster AI systems.
Other applications: many other use cases to list but few examples are; material (battery) designs, computational fluid dynamics, secure communications, financial services and solutions (e.g. black swan forecasting) etc.
A combined project by NASA and google - 1097-QBUIT D-Wave, is claimed to be 100 M times powerful vs. the traditional computing we are familiar with today.
Key Security Concerns
Breaking Encryption: As quantum computing advances, it could easily break many encryption methods currently used. New quantum-resistant algorithms are being developed, but the race is on.
Data Vulnerability: Governments and organizations are stockpiling encrypted data, planning to decrypt it once quantum computers are capable. This makes the data vulnerable to future quantum attacks.
Blockchain at Risk: While blockchain technology is considered secure, its foundational encryption methods could be rendered useless by quantum attacks, putting everything from cryptocurrencies to smart contracts in danger.
But before we get started, if you are brand new to the topic, here’s a two great short layman documentaries:
by Cleo Abram (8.4M views), “Quantum Computers, explained with MKBHD”.
by Bloomberg (2.5 M views), “The Race to Harness Quantum Computing's Mind-Bending Power | The Future With Hannah Fry”.
Curated Learning Path (Quantum Computing)
To help you dive deeper into Quantum Computing, I’ve compiled a comprehensive learning path with reading materials, audio content, videos, and both free and commercial training courses. Whether you're just curious or looking to become proficient in quantum technologies, this guide will equip you with the right resources.
Intro to Quantum Computing
Goal: Understand the basic principles of quantum computing and how it differs from classical computing.
To Do / Actions | Reference Description | Link |
|---|---|---|
Reading (Articles/Books) | "Quantum Computing for Everyone" by Chris Bernhardt | |
Listening (Audio) | Quantum Computing Now Podcast | |
Watching (Video) | "Quantum Computing Explained Simply" | Qiskit for Beginners – YouTube (15 min) |
Learning (Free - Courses) | IBM Quantum Learning Learn the basics of quantum computing, and how to use IBM Quantum services and systems to solve real-world problems. Introduction to Quantum Computing by Brilliant.org | |
Learning (Paid - Courses) | MIT xPro: Quantum Computing Fundamentals |
What’s a Qubit?
Goal: Understand what qubits are, how they operate, and why they’re so essential in quantum computing.
To Do / Actions | Reference Description | Link |
|---|---|---|
Reading (Articles/Books) | "What is a quantum bit (qubit)?" | Link to article. |
Listening (Audio) | "The Qubit Revolution" Podcast | |
Watching (Video) | YouTube Video: "The Qubit Revolution" | |
Learning (Free - Courses) | The Coding School’s “Introduction to Qubits” (Qubit by Qubit) Qiskit Courses and Certifications Learn Qiskit, earn certificates with paid and free online courses from IIT Madras, TU Delft and other top universities around the world. Your Guide to 100+ Qubits: Quantum Computing in Practice - at Qiskit Youtube Channel by IBM. | |
Learning (Paid - Courses) | IBM Quantum Experience |
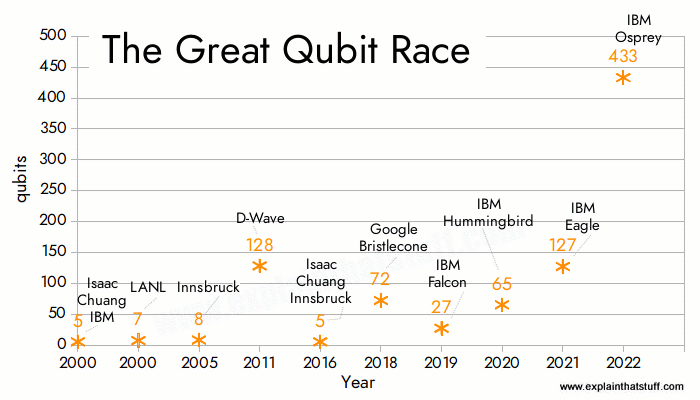
Below is an interesting chart on the development of Qubit.
Quantum Computing: Applications and Use Cases
Goal: Discover the real-world applications and industries that will benefit from quantum computing.
To Do / Actions | Reference Description | Link |
|---|---|---|
Reading (Articles/Books) | "Quantum Computing Use Cases" (IBM Whitepaper) | Link to Whitepaper |
Listening (Audio) | “Quantum Leaps in Business” Podcast | |
Watching (Video) | YouTube Video: "How Quantum Computing Will Transform Everything" | |
Learning (Free - Courses) | “Quantum Computing Applications in Industry” by edX | Link to Free Course |
Learning (Paid - Courses) | Coursera’s “Quantum Computing: Theory to Simulation” |
Quantum Threats to Cybersecurity
Goal: Understand the key security challenges quantum computing poses and the potential solutions.
To Do / Actions | Reference Description | Link |
|---|---|---|
Reading (Articles/Books) | Post-Quantum Cryptography (PQC) by NIST. NIST Report on Post-Quantum Cryptography | What Is Post-Quantum Cryptography (PQC)? NIST Report or NIST.IR.8105. |
Listening (Audio) | “EP164 Quantum Computing: Understanding the (very serious) Threat and Post-Quantum Cryptography” (Podcast) | |
Watching (Video) | YouTube Video: "The Quantum Threat to RSA Encryption" | |
Learning (Free - Courses) | Coursera’s "Introduction to Post-Quantum Cryptography" | |
Learning (Paid - Courses) | MIT, Udemy and other platforms also provide quantum computing foundation or security courses. | Checkout different platforms websites like udemy.com and search for quantum computing. |
According to NIST below outlines the impact of quantum computing to common cryptographic algorithms.

According to NIST IR 8105
Quantum-Resistant Cryptography
Goal: Learn about the current efforts to develop cryptographic algorithms that can withstand quantum attacks.
To Do / Actions | Reference Description | Link |
|---|---|---|
Reading (Articles/Books) | "Quantum-Resistant Algorithms" (Whitepaper by NIST) Post-Quantum Encryption Standards NIST Releases First 3 Finalized Post-Quantum Encryption Standards | |
Listening (Audio) | "Preparing for the Quantum Cryptography Transition" (Podcast) | |
Watching (Video) | YouTube Video: "Quantum-Resistant Encryption Explained" | |
Learning (Free - Courses) | Post-Quantum Cryptography by Cybersecurity Learning Hub | Link to Free Course |
Learning (Paid - Courses) | Udemy’s "Quantum Cryptography Masterclass" | Link to Course |
NIST announced a selection of an initial 4 algorithms that could prove to be PQC resistant algorithms namely — CRYSTALS-Kyber, CRYSTALS-Dilithium, Sphincs+ and FALCON. First 3 standards draft were released in 2023 and for Falcon it is planned for late 2024. The goal of these standards are to support general encryption (protect information exchange across public networks) and digital signatures (used for identity authentication). The first 3 algorithms are based on Lattices based cryptography (mathematical structure used for encryption and decryption).

Paper: Introduces Blockchain Cryptography Resistant to Quantum Computing Attacks
Above is referenced from → A Review of Quantum Cybersecurity: Threats, Risks and Opportunities.
Other interesting reads are:
Cybersecurity in the Quantum Era: Assessing the Impact of Quantum Computing on Infrastructure by Yaser Baseri, Vikas Chouhan, Ali Ghorbani.
Quantum Computing Cybersecurity Risks by World Economic Forum.
Moving toward an All-of-the-Above Approach to Quantum Cybersecurity - explains the concept of Quantum Key Distribution.
Post Quantum Cryptography initiative by CISA.
What is Y2Q?
It is anticipated that year 2030 (date: 14-April-2030) would bring a new technological cybersecurity challenge to the world, known as “Year to Quantum or Y2Q”. According to Bruno Huttner (Co-chair of quantum safe security working group at cloud security alliance), Y2Q is named like Y2K. Read more here.
Conclusion:
There’s much more to securing thing for a post quantum computing era. The above curated learning path is designed to give holistic view of quantum computing, its potential applications, and its security risks/implications. Whether you're a beginner or a seasoned professional, these resources will help you gain valuable insights and stay ahead of the curve in the quantum computing revolution.
What are your best reads? videos? courses? - do type in comments below and enrich this resource.
My Recent Most Viewed Social Posts:
In case you’ve missed - here are some of my recent most viewed social posts.
"Boost Your Defense Game - IT & OT/ICS Cybersecurity Training [Securing Things by M. Yousuf Faisal]"
IT & OT/ICS CySEAT - teaser video - only on Securing Things Academy (40% off)
🚀 Ready to Transform Your Career? Dive into IT & OT/ICS Cybersecurity🔐- Phase A - Getting started in IT & OT/ICS Cybersecurity.
🚀 Ready to Transform Your Career? Dive into IT & OT/ICS Cybersecurity🔐- Phase B - Getting started in IT & OT/ICS Cybersecurity.
🚀 Ready to Transform Your Career? Dive into IT & OT/ICS Cybersecurity🔐- The 3 Phase, 12 steps blue print - Getting started in IT & OT/ICS Cybersecurity.
🚀 Ready to Transform Your Career? Dive into IT & OT/ICS Cybersecurity🔐- 4 personas perspective, for 3 phase blue print - Getting started in IT & OT/ICS Cybersecurity.
Getting OT/ICS visibility for industrial, data centre or smart buildings environments.
IT & OT Security Dozen framework for building, executing & managing a Cybersecurity & Resilience Transformation Program.
Securing Things Academy:
IT & OT CySEAT (Cyber Security Education And Transformation) course is designed for IT and OT cybersecurity practitioners. Join the wait-list → here.
Checkout a brief overview below:
Ways in which I can help?
Whenever you are ready - I can help you with:
A - IT & OT Cybersecurity Advisory / Consulting services - for securing your business and or its digital transformation journey.
B - Security Awareness Training & Phishing Awareness Portal - Train your staff and build a Security awareness program subscription based service.
C - Securing Things Academy (STA) - Security trainings for IT & OT practitioners.
Visit the newsletter website for Links to above services and or reach out at info[at]securingthings[dot]com or DM me via LinkedIn.
D - Securing Things Newsletter - Sponsor this newsletter to showcase your brand globally, or subscribe to simply Get Smarter at Securing Things.
Reach out at newsletter[at]securingthings[dot]com or DM me via LinkedIn.
How are we doing?
I invite you as part of #SecuringThings community to share your feedback.
Rate the newsletter content
Your feedback and input is invaluable to me as we work together to strengthen our cybersecurity defenses and create a safer and smarter digital society.
Let us know how we can improve this and or what you’d like to see in future?
Thank you for your trust and continued support.
Do register, validate your email, and request login link to submit poll to be able to enter a chance to win a future course giveaway.
Thanks for reading - until the next edition!
It’s a Great Day to Start Securing Things for a Smart & Safer Society.
Take care and Best Regards,
M. Yousuf Faisal. (Advice | Consult Cyber & business leaders in their journey on Securing Things (IT, OT/ICS, IIOT, digital transformation, Industry 4.0, & AI) & share everything I learn on this Newsletter | and upcoming Academy).
The Newsletter Platform Built for Growth
When starting a newsletter, there are plenty of choices. But there’s only one publishing tool built to help you grow your publications as quickly and sustainably as possible.
Beehiiv was founded by some of the earliest employees of the Morning Brew, and they know what it takes to grow a newsletter from zero to millions.
The all-in-one publishing suite comes with built-in growth tools, customization, and best-in-class analytics that actually move the needle - all in an easy-to-use interface.
Not to mention—responsive audience polls, a custom referral program, SEO-optimized webpage’s, and so much more.
If you’ve considered starting a newsletter, there’s no better place to get started and no better time than now.